Gartner Names Demisto ‘Cool Vendor’ in Security Ops & Vulnerability Mgt
Demisto, an innovator in Security Automation and Orchestration and Response technology, and a Winner in the 2017 ‘ASTORS’ Homeland Security Awards Program, has been included in the list of “Cool Vendors” in the...
DHS Unveils 5 Pillar Strategy to Guide Cybersecurity Efforts (See them Here)
We depend upon cyberspace for daily conveniences, critical services, and economic prosperity. At the U.S. Department of Homeland Security (DHS), we believe that cyberspace can be made secure and resilient.
DHS works...
Ivanti Competes in 2018 ‘ASTORS’ Homeland Security Awards Program
Ivanti, the company that unifies IT to better manage and secure the digital workplace, and a Platinum Award Winner in the 2017 'ASTORS' Homeland Security Awards Program, is pleased to announce...
SolarWinds NCM Competes in 2018 ‘ASTORS’ Awards (Multi-Video)
Successful threat mitigation requires continuous monitoring of network configuration changes and potential policy violations, but this process needs to be automated, fast, and reliable.
Continuous real-time monitoring and alerts for automated detection...
DoD: Apps in Over 100 Data Centers to Move to milCloud (Multi-Video)
By Jared Serbu, Federal News Radio
The Pentagon has ordered Defense organizations that operate more than 100 of its data centers to begin migrating their applications to milCloud 2.0, the new on-premises commercial cloud service...
RCSD Deploys NICE Next-Gen 911Recording & Incident Intel Tech
The Riverside County Sheriff’s Office (RCSD), the second largest Sheriff’s Office in California has upgraded to the latest NICE Inform multimedia recording and incident intelligence technology as it transitions to an all...
NICE Inform Competes in 2018 ‘ASTORS’ Homeland Security Awards
If it’s not available in your community already, chances are it soon will be.
All of the major wireless carriers now provide text-to-911 services to their subscribers, and more than 1,400 PSAPs...
IAEA Completes MOSAIC to Safe Guard Nuclear IT Info (Multi-Video)
The International Atomic Energy Agency (IAEA) has completed a three-year project to revamp its Safeguards information technology system to be more effective in its work to ensure the peaceful uses of...
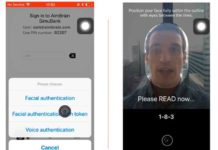
AimBrain Launches Free-for-Life Biometric ID Platform (See Demo)
AimBrain has just launched a free-for-life platform that lets entrepreneurs, app developers and technical audiences swap PINS, passwords and codes for facial and voice user biometric verifications, in an autonomous, trial-to-deployment...
When Employees Leave: Best Practices for Preventing Data Theft
By Chuck Burbank, CIO, FairWarning, Inc.
Empowering your employees to do their best work means providing them access to physical and digital assets in the company network that can help them scale...