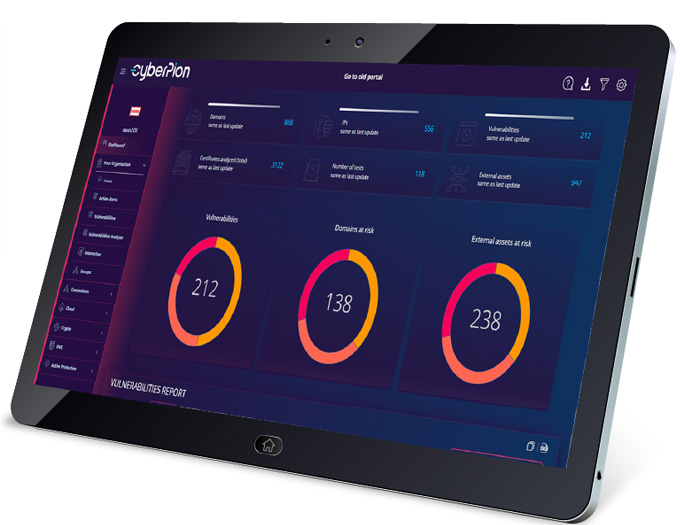
American Security Today’s Annual ‘ASTORS’ Awards is the preeminent U.S. Homeland Security Awards Program, and now in its Sixth Year, continues to recognize industry leaders of Physical and Border Security, Cybersecurity, Emergency Preparedness – Management and Response, Law Enforcement, First Responders, as well as federal, state and municipal government agencies in the acknowledgment of their outstanding efforts to Keep our Nation Secure.

An exclusive event featured on the opening day of ISC East, the Northeast’s largest security industry event, and the inaugural Natural Disaster and Emergency Management (NDEM) Expo, two hundred representatives of law enforcement, public safety, and top industry leaders came together to honor the selfless service of those who stand on the front lines, and those who stand beside them – providing the capabilities and technologies to create a safer world for generations to come.

AST Honors Thomas Richardson, FDNY Chief of Department; Dr. Kathleen Kiernan, President of NEC National Security Systems; and Richard Blatus, FDNY Assistant Chief of Operations, at the 2021 ‘ASTORS’ Awards Luncheon at ISC East.
The United States was forever changed 20 years ago on September 11th, and we were fortunate to have many of those who responded to those horrific tragedies join us at the 2021 ‘ASTORS’ Awards Luncheon.
In the days that followed 9/11, the critical needs of protecting our country catapulted us into new and innovative ways to secure our homeland – which is how many of the agencies and enterprise organizations that are today ‘ASTORS’ Awards Champions, came into being.
This year marks the 20th anniversary of Homeland Security as we know it today, including the 20th anniversary of the Transportation Security Administration (TSA), who gathered with us to celebrate new ways of thinking about responsibility, new legislation, and comprehensive collaborations between private and public sectors that have led to developing intelligence and technologies which serve to protect our nation.

We were delighted to welcome representatives of the TSA and Federal Air Marshals Service (FAMS), which included the Asst Administrator for Strategic Communications & Public Affairs; the Deputy Branch Manager of Aviation Programs Branch, the Assistant Federal Security Director of Screening, an Explosive Detection Canine Handler and K9 Warren, the Federal Security Director, a Supervisory Transportation Security Officer, and a Transportation Security Inspector in addition to members of the Office of the Administrator.

We were also pleased to have join us Chief of Department FDNY Thomas Richardson, Assistant Chief of Operations FDNY Richard Blatus, Doug Farber, National Board Member at InfraGard National (INMA); Assistant Chief Jeffrey Carroll of the Washington DC Metropolitan Police Department, Captain James Albrecht of the NYPD (Ret), U.S. Marshal Derrick Driscoll (Ret); Patrick Burke, the executive director of the Washington DC Police Foundation and former Assistant Chief of the MPDC; Jeff Wohler, Chief Executive Officer at San Diego Harbor Police Foundation, and representatives of the Naval Postgraduate School Center for Homeland Defense and Security, to name a few.

Our keynote speaker featured a moving and informative address from TSA Administrator and Vice-Admiral of the United States Coast Guard (Ret), David Pekoske; to our attendees who traveled from across the United States and abroad, on the strategic priorities of the 64,000 member TSA workforce in securing the transportation system, enabling safe, and in many cases, contactless travel.
Administrator Pekoske addressed the topics of ensuring smooth and timely holiday season traveling, COVID-19 mandatory vaccinations, how the TSA is addressing increasing inflight passenger disturbances, which include a ‘Crew Member Self Defense Training Program’ initiated and developed by the Federal Air Marshal Service, and new regulations imposed upon those travelers who become combative during flights.
Administrator Pekoske also educated attendees as to the overall critical missions of the TSA, and innovative new approaches his administration has undertaken since taking office.
(See an ‘American Security Today Exclusive Interview’ with TSA Administrator David Pekoske facilitated by Dr. Kathleen Kiernan, President of NEC National Security Systems at the 2020 ‘ASTORS’ Awards Presentation Luncheon in New York City on November 17, 2021. Courtesy of My Pristine Images, and Vimeo.)
And last but certainly not least, Legendary Former Police Commissioner William Bratton of the New York Police Department, the Boston Police Department, and former Chief of the Los Angeles Police Department, was also live at the event, meeting with attendees and signing copies of his latest work ‘The Profession: A Memoir of Community, Race, and the Arc of Policing in America,’ courtesy of the generosity of our 2021 ‘ASTORS’ Awards Premier Sponsors AMAROK, ATI Systems, Attivo Networks, Automatic Systems of America, Fortior Solutions, Reed Expositions, and SIMS Software.

At the conclusion of the luncheon, both Administrator Pekoske and Commissioner Bratton graciously spent time with attendees discussing their most critical concerns of the day and posing for photographs with their peers, old friends, and event sponsors and guests.
The prestigious Annual ‘ASTORS’ Homeland Security Awards Program highlights the most cutting-edge and forward-thinking security solutions coming onto the market today, to ensure our readers have the information they need to stay ahead of the competition and keep our Nation safe – one facility, street, and city at a time.

The program is specifically designed to honor distinguished government and vendor solutions that deliver enhanced value, benefit, and intelligence to end-users in a variety of government, homeland security, enterprise, and public safety vertical markets.
‘ASTORS’ nominations are evaluated on their technical innovation, interoperability, specific impact within the category, their overall impact to the industry, relatability to other industry technologies, and application feasibility outside of the industry,” said AST’s Publisher, Michael J. Madsen.
‘ASTORS’ Awards Winners are selected by our American Security Today Expert Panel of Judges, and the ‘ASTORS’ Homeland Security Awards are presented at the Platinum, Gold, Silver, and Bronze levels.
(See just a few highlights of American Security Today’s 2021 ‘ASTORS’ Awards Presentation Luncheon at ISC East. Courtesy of My Pristine Images and Vimeo.)
The vast majority of ‘ASTORS’ Award Winners return to compete in American Security Today’s Annual Homeland Security Awards Program each year to build upon their legacy of achievement, and we’ve been fortunate that our ‘ASTORS’ Awards Premier Sponsors return year to year to reap the benefits of their participation in the industry’s largest and most comprehensive Annual Awards Program.
American Security Today would like to express our deepest gratitude for the generosity of our New and Returning ‘ASTORS’ Awards Premier Sponsors for their continued support, and assistance in ensuring that our program continues to grow and to delight attendees at our Annual ‘ASTORS’ Awards Presentation Luncheon.
The 2021 ‘ASTORS’ Awards Program is Proudly Sponsored by AMAROK, Fortior Solutions and SIMS Software, along with Returning Premier Sponsors ATI Systems, Attivo Networks, Automatic Systems, and Reed Exhibitions.
And without further ado, American Security Today is Proud to Introduce the 2021 ‘ASTORS’ Homeland Security Awards Winners.
2021 ‘ASTORS’ Homeland Security Award Winners in Industry Are…
908 Devices
 Best CBRNE Detection System
Best CBRNE Detection System
-
MX908
-
New to the Annual ‘ASTORS’ Awards Program, the MX908 is a multi-mission handheld mass spectrometer for Chemical/Biological/Radiation/Nuclear/Explosive detection which can identify compounds at trace levels with a high level of sensitivity and selectivity, to provide elite responders conducting chemical, explosive, priority drug, and HazMat operations actionable intelligence fast.
-
The MX908 accurately discriminates priority threats from the broad range of interferents that lead to false alarms with other technologies.
-
The recently introduced MX908 Aerosol Module for military and civilian responders with Bluetooth further expands the capabilities of the field-deployable MX908 to detect and identify aerosolized and vaporized chemical threats, including chemical warfare agents, fourth-generation agents, pharmaceutical-based agents, and more.
(Learn More about how this first-of-its-Kind Aero Module Detects Aerosolized Chemical Threats; New Targets Added Including Cathinones and Cannabinoids; New MX908 Mobile App Provides Responders Rapid Access & Data Sharing. Courtesy of 908 Devices and Vimeo.)
Acoustic Technology Inc. (ATI Systems)
Best Mass Notification System – Hardware
-
Mobile Solutions for Giant Voice
-
When an emergency strikes, effective dissemination of information in a timely manner can be critical, and emergency communications for disasters require rapid deployment of Giant Voice (GV) systems.

-
ATI Systems, a world-leading provider of reliable emergency warning & mass notification systems (MNS), offers excellent Giant Voice Solutions for Military, Community, and Campus clients with the essential tools for emergency planning and preparedness, which includes their Mobile High Powered Speaker Station (HPSS) which is Rapidly Deployable on an Outdoor Siren Trailer, their Transportable High Powered Speaker Station (THPSS), and their Deployable High Powered Speaker Stations (DHPSS).
-
Through acoustic design and modeling, the company provides optimal sound coverage and superior voice intelligibility for both outdoor and indoor areas to ensure the safety of our clients worldwide.

*ATI Systems is also a Returning Premier Sponsor for the Fifth Consecutive Year in the Annual ‘ASTORS’ Homeland Security Awards Program, and a 2020, 2019, 2018 and 2017 ‘ASTORS’ Platinum Award Winner.
Actuate AI
 Best Video Analytics Solution (Tie**)
Best Video Analytics Solution (Tie**)
-
Actuate AI Software
-
Actuate’s cloud-based AI software, turns any existing security camera into a intruder- and threat-detecting smart camera with no additional hardware required.
-
The software identifies safety and security threats in real-time and issues automatic alerts to dramatically reduce the time it takes for security teams and law enforcement to respond.
- When an emergency strikes, effective dissemination of information in a timely manner can be critical.
(See how Actuate builds Gun Detection AI that Reacts Before Shots are Fired, to turn your existing security cameras into threat-detecting smart cameras with 99%+ accuracy. No servers required. Courtesy of Actuate AI and YouTube.)
Advanced Detection Technology
Best Under Vehicle Surveillance System
-
LowCam® VI100 Under Vehicle Inspection System (UVIS)
-
Every day poses a new security challenge, whether that’s protecting a nation’s borders, facilities, monuments, airports, or its people, so to help minimize these threats, Advanced Detection Technology has introduced the first-ever, battery-powered UVIS for use during ad hoc situations.

-
The LowCam® VI100 “No Strings Attached” UVIS – touting no cables and no cords, not to mention a self-contained battery and military-grade equipment – lets you take this level of improvised security with you for anywhere event security management.
-
Portable, affordable, and all-inclusive, LowCam VI100 provides well-defined, ultra-high-definition, and side-to-side daylight views, wirelessly displayed on a tablet with 15X zoom capabilities.
(Learn how since 2003, Advanced Detection Technology helps create full access control solutions that include Under Vehicle Inspection Systems (UVIS) for government and law enforcement agencies. Courtesy of Advanced Detection Technology and YouTube.)
-
*Advanced Detection Technology was also recognized in the 2020, 2019, 2018, and 2017 ‘ASTORS’ Homeland Security Awards Programs.
Aeroturn, LLC
Best Pedestrian Entrance Control Solution
-
Contactless Biometric Turnstile Entry & Exit System
-
Aeroturn continues to lead the way in perimeter protection solutions even through a global pandemic.

-
Aeroturn along with security integrator partner, Siemens-Beltsville, developed the integration of a facial recognition system with French-based Idemia for a complete and customized biometric credential access control system for one of the largest financial lenders in the world, which required state of the art locking turnstiles coupled with a built-in Covid compliant credential system, to ensure health safety during these highly infectious times.
-
Aeroturn accommodated the biometric facial recognition turnstile deployment’s aggressive timeline set for completion and commissioning, as the staff had a set date to return to the buildings in the complex.
-
Over the last year Aeroturn has also catered to its government clients by developing a hybrid touchless system for military bases in the Atlantic, and Aeroturn’s team continues to educate the end-user and integrator about the importance of quality turnstiles with touchless solutions.

-
*Aeroturn LLC was also recognized in the 2020, 2019 and 2018 ‘ASTORS’ Homeland Security Awards Programs.
AlertMedia
Best Mass Notification Solution – Software
-
AlertMedia Emergency Communication Software
-
Every day, businesses face an increasing number of threats to their people and operations—from severe weather events and security incidents to global health crises.

-
Keeping employees safe during these critical events requires a modern and reliable emergency communication solution.
-
It’s why companies in more than 130 countries across a range of industries—from Fortune 500 companies to small and mid-size organizations—have turned to AlertMedia for help.
-
AlertMedia‘s emergency communication software is more than just a mass notification system. Their robust solution integrates with internal systems and connects an entire organization to allow them to communicate with precision, interact with their audience, and confirm a resolution.
(Every day, organizations face a wide array of threats. Learn how AlertMedia can help you quickly identify emerging threats and send fast, effective emergency communications to employees in harm’s way. Courtesy of AlertMedia and YouTube.)
- *AlertMedia was also recognized with Multiple ‘ASTORS’ Awards in 2020, 2019, 2018, and 2017 ‘ASTORS’ Homeland Security Awards Programs.
Allied Universal (First of Three)
Best Machine Learning & Artificial Intelligence (Tie**)
-
HELIAUS
-
HELIAUS® is a sophisticated Artificial Intelligence (AI)-driven solution that goes beyond the outmoded “detect and respond” model of risk management.

-
More than just a tour or incident management system, HELIAUS® is a comprehensive workforce management solution that uses powerful algorithms to generate risk-adverse recommendations to keep your security professionals connected and engaged, situationally informed, and armed with the right recommendations to effectively create safer, more secure environments.
-
The bottom line is HELIAUS® can help reduce security and safety incidents by up to 20%, all while improving profitability and your bottom line.
(Learn about HELIAUS®, a revolutionary integrated solution beyond the archaic “detect and respond” model of risk management. It’s not just a tour or incident management system. HELIAUS® is a comprehensive workforce management solution with AI technology at its core. Courtesy of Allied Universal and YouTube.)
Allied Universal (Second of Three)
Best Airport/Aviation Security Solution
-
AUS – CMH
-
The John Glenn Columbus International Airport (CMH) is a medium hub facility, which proved challenging to implement mitigation measures having been built in the 1950s when certain security needs were never contemplated, and encompassing 2,265 acres of operational space; plus Rickenbacker International Airport (LCK) which covers 4,342 acres.

-
Allied Universal fulfills a unique opportunity at the John Glenn Columbus International Airport by continually analyzing Security Professionals routes and schedules not only to better interact with the facility and the public – but also to mitigate insider infiltration threats by using their HELIAUS® workforce management tool to identify risk patterns and behaviors that would otherwise not be visible.
-
By keeping their Security Professionals fluid, Allied Universal Officers can routinely roam the facility to conduct random security measures of employees, and with an average of 3,000 badged personnel, in 2020, conducted more than 50,000 checks.In partnership with Public Safety leadership at CMH, Allied Universal serves as the mobile eyes, ears, and badge readers.
Allied Universal (Third of Three)
Best Security Workforce Mgmt Platform
-
HELIAUS
-
HELIAUS is Allied Universal’s AI-powered workforce management solution that streamlines security operations at client’s sites, generates intelligent recommendations to help mitigate risk, and provides real-time communication and insight into the hands of clients Security Leadership to better protect their people, brand, and assets.
(Inspired by the power of the sun and Helios, the sun god of Greek mythology, Allied Universal’s proprietary HELIAUS® platform is the smart technology of tomorrow that places insight into the hands of your Security Professionals to better protect your people, brand, and assets. Courtesy of Allied Universal and YouTube.)
-
Allied Universal Programs have been recognized with Multiple Awards in the 2020, 2019, and 2018 ‘ASTORS’ Homeland Security Awards Programs.
AMAROK
Best Perimeter Protection Solution – Physical
-
FORTIFEYE featuring The Electric Guard Dog Fence
-
AMAROK, formerly Electric Guard Dog, introduced FORTIFEYE in 2020 to enhance their physical perimeter security deterrent offering.

-
FORTIFEYE integrates electric security fencing, video surveillance, and video monitoring to create an ultimate crime prevention solution for commercial businesses and industrial sites.
-
FORTIFEYE has multiple layers of integrated security to protect your business, starting with the Electric Guard Dog Fence which delivers 7,000 volts to would-be thieves.
-
Cameras capture and record every second of activity in real time, from initial approach to flight and finishes with remote video monitoring to validate the breach and dispatch authorities.
(AMAROK is the Ultimate Perimeter Security Solution. See how their full-perimeter solar electric fences paired with the company’s integrated security systems stop crime before it happens. Courtesy of AMAROK and YouTube.)

-
*AMAROK (formerly the Electric Guard Dog), is also a New Premier Sponsor in the 2021 ‘ASTORS’ Homeland Security Awards Program and was recognized in the 2020, and 2019 ‘ASTORS’ Homeland Security Awards Program.
American Signal Corporation (ASC)
Best Mass Notification Solution – Software
-
CompuLert NEXGen
-
American Signal Corporation’s CompuLert NEXGen is a premier control platform for mass notifications, allowing emergency managers to receive updates in real-time and quickly alert individuals who are in potentially hazardous situations.
-
CompuLert NEXGen’s robust technologies allows a variety of sensor inputs, detecting wind speed, water levels, chemical spills, lightning strikes and more. The system can then automatically notify residents through alerting devices, like ASC’s outdoor notification sirens as well as its ASC AWARE desktop alerts and ASC Sentinel mobile notification.

-
Furthermore, ASC’s CompuLert NEXGen seamlessly interfaces with National Weather Service Alerts and FEMA’s Integrated Public Alert Warning System, both of which can automatically activate alerts based on the threat or emergency. Emergency managers can customize their system to allow only relevant alerts and activate devices in designated areas to reach only those in immediate danger.
CompuLert NEXGen can been deployed for any application, including campuses, military installations, nuclear facilities, cities and counties, and more, and can be installed on a single PC, or on several servers to ensure availability during disasters.
(Understanding the changes and benefits of CompuLert™ NEXGen. Courtesy of John Coultas ASC and YouTube.)
-
*American Signal Corporation was also recognized in the 2019, 2018 and 2017 ‘ASTORS’ Homeland Security Awards Programs.
Apricorn

Best Data Storage Security Solution
-
Aegis Padlock SSD
-
Even before the COVID-19 pandemic, remote and mobile working was on the rise however, as the global workforce shifted from office to home practically overnight due to COVID-19, it became abundantly clear that workers would use a variety of devices at their disposal outside of their corporate firewall.

-
To comply with corporate security policy and protect data in the remote workforce, Apricorn developed the portable Aegis Padlock SSD, a software-Free, 100% hardware-based 256-bit AES XTS encrypted, onboard keypad PIN authenticated, and ultra-fast USB 3.1 (3.0) data transfer speeds.
-
The Aegis Padlock SSD also thrives where software-authenticated encrypted devices can’t even function, such as embedded systems, machines without a keyboard, and equipment in possession of a powered USB port and storage file system.
-
All internal componentry is protected from physical tampering with a layer of hardened epoxy, and its firmware is locked down to prevent any modifications making it impervious to malware attacks such as BadUSB.
-
The Aegis Padlock SSD keeps your Sensitive Data Secure On the Go, Encrypting on The Fly.
(The remake of the ultra compact, 256 bit AES XTS hardware-encrypted Padlock SSD USB 3.2, is still smaller than a deck of cards with its extruded aluminum enclosure, membrane style keypad, and FIPS 140-2 level 2 validation, and is nearly twice as fast as its predecessor, clocking in at up to 350 MB/s, and comes in five capacities from 240GB up to 4GB. And while the speeds and sizes have doubled and quadrupled, respectively, the cost of the Padlock SSD from then to now has come down to be about 1/3 of what they were back then. Courtesy of Apricorn and YouTube.)
-
*Apricorn was also recognized in the 2020, 2019, 2018 and 2016 ‘ASTORS’ Homeland Security Awards Programs.
Attack IQ
Best Breach & Attack Simulation
-
AttackIQ Security Optimization Platform
-
New to the ‘ASTORS’ Awards Program, the AttackIQ Security Optimization Platform enables risk and security practitioners to continuously assess and improve critical security controls within their production environment, optimizing their end-to-end security posture and providing trend reporting for demonstrable improvement over time.
-
By surfacing better, automated insights, teams are able to make smarter investment decisions and deliver on both business continuity and greater program effectiveness.
(Learn how AttackIQ’s Security Optimization Platform helps security teams achieve cybersecurity readiness through automated security control validation. Courtesy of AttackIQ and YouTube.)
Attivo Networks (First of Three)
Best Identity Detection & Response Solution
-
IDR Suite of Products
-
Attivo Networks®, a leader in identity detection and response, has expanded its portfolio to include cloud identity security.
Organizations provision human and non-human identities (applications, virtual machines, serverless functions, and such) on the network and in the cloud, which attackers target early in the attack cycle to progress their attacks.
-
By stealing these identities, they can impersonate authorized users, access resources, move laterally throughout the network and cloud environments, conduct reconnaissance, elevate privileges, identify targets, and compromise data.

-
While many tools intend to keep networks secure, Identity Detection and Response (IDR) gives organizations a critical new weapon in their arsenal to find and fix credential and entitlement weaknesses and detect live attacks on a real-time basis.
-
As modern cybercriminals attempt to exploit vulnerable credentials and entitlements to move through networks undetected, IDR solutions play a meaningful role in stopping them, whereas other tools simply cannot.
-
Attivo Networks IDR Suite of Products can seamlessly extend to the cloud and deliver detailed entitlement visibility for identities – including users, applications, containers, serverless functions, and other assets.
Attivo Networks (Second of Three)
Best Intrusion Detection & Prevention Solution
-
IDR Suite of Products
-
Attack surfaces have expanded dramatically with the shift toward remote work putting identity at the forefront of security, a major shift from traditional perimeter-based strategies.
-
Organizations must now defend identities across the entire enterprise with identity-based, least-privilege access programs and defenses capable of detecting attack escalation and lateral movement on-premises and in the cloud.

-
Attivo Networks has leveraged its deep experience in privilege escalation and lateral movement detection to become a significant player in the Identity Detection and Response space.
-
In the last year, the company has secured its leadership position based on its broad portfolio of capabilities that focus on unprecedented visibility to exposures and misconfigurations of identities and entitlements and early detection of credential theft, misuse, and privileged escalation activities.
(The Attivo ThreatDefend® Platform delivers unparalleled attack prevention, detection, and adversary intelligence collection based on cyber deception and data concealment technologies for an informed defense. The platform efficiently derails attacker discovery, lateral movement, privilege escalation, and collection activities early in the attack cycle across endpoints, Active Directory, and network devices on-premises, in clouds, and on specialized attack surfaces. Courtesy of Attivo Networks and YouTube.)
Attivo Networks (Third of Three)
Best Cloud Security Solution
-
IDEntitleX
-
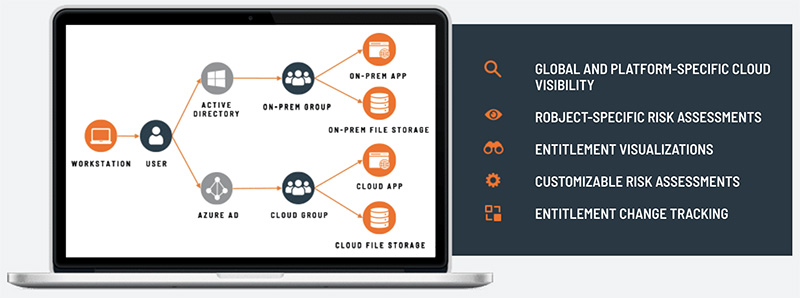
IDEntitleX is Attivo Networks’ Cloud Infrastructure Entitlement (CIEM) solution, which provides unprecedented visibility for cloud permissions management.
-
Customers gain actionable visibility to cloud identity risks and entitlement exposures so they can address risky entitlements and drift from security policies.
-
This solution makes it easy to identify and reduce risk by providing intuitive and interactive graphical visualizations for cloud identities, roles/permissions, and resources.
-
Defenders now gain the visibility needed to see misconfigurations and excess permissions attackers can leverage to create attack paths and persistence within the cloud environment.

*Attivo Networks is also a Returning Premier Sponsor of the Annual ‘ASTORS’ Homeland Security Awards Program for the Fourth Year, and a Multi-Platinum Award Winner in the 2020, 2019, 2018 and 2017 ‘ASTORS’ Awards Programs.
Automatic Systems America
Best Pedestrian Entrance Control Solution
-
SlimLane Optical Barrier Turnstile
-
Automatic Systems America continues to evolve its award-winning SlimLane swing optical barrier turnstiles to offer customized solutions able to meet customer requirements for even the most unique installations.
-
The variety of speedgate cabinets range from the sleek standard unit and evolve to the SlimLane EP model or the rounder SlimLane EPR.
-
Larger biometric peripherals such as facial recognition and frictionless fingerprinting offer a contactless alternative to proximity readers and can easily be integrated within the SlimLane EPW or NK cabinets.
(Automatic Systems’ Slimlane EPW speed gates offer extended integration capabilities, allowing us to offer contactless identification solutions, with best-in-class #biometric readers such as the MorphoWave Compact device from IDEMIA. Courtesy of Automatic Systems and YouTube.)
-
With the current social distancing and contactless requirements, the SlimLane can also offer a fully touchless solution while protecting its users.
-
The hand “wave” and facial recognition readers were easily integrated and offer a fully contactless solution while the UL 2593 Certified SlimLane offers a highly reliable (10 Million MCBF) physical access control turnstile.
-
With its 5-year standard warranty and infinite customizations, the SlimLane continues to be a perfect solution for lobby entrances.
-
Selected as the “standard” for multiple financial institutions, we are confident that the SlimLane will continue to answer any pedestrian access control requirements for your years to come.
(Automatic Systems SlimLane EPW Touchless swing glass turnstiles offer custom integration provides an innovative and effective solution with multiple biometric authentications during continuous movement. Courtesy of Automatic Systems and YouTube.)
*Automatic Systems is also a Returning Premier Sponsor for the Fifth Consecutive Year in the Annual ‘ASTORS’ Homeland Security Awards Program, and a Platinum-Award Winner in their Sixth Annual ‘ASTORS’ Awards Program.
Axis Communications (First of Three)
Best Body Worn Video Solution
-
AXIS W100 Body Worn Camera
-
The AXIS W100 Body Worn Camera produces sharp images and clear audio, thanks to dual microphones with noise suppression, is lightweight, robust, and water-resistant, starting and stopping quickly with a single touch, buffers up to 90 seconds before it’s switched on so users can catch entire encounters, and features a silent mode for discrete recording.

-
The AXIS W100 Body Worn Camera features Axis Zipstream technology so users can store as much footage as needed without compromising video quality – onsite or in the cloud, lives up to official FBI standards for cybersecurity with end-to-end encryption, and it’s easy to add as many cameras as needed at any time with open standards and cost-efficient docking stations.
-
The AXIS W100 Body Worn Camera comes with an easy-to-use mobile app – the AXIS Body Worn Assistant – for viewing and labeling in the field, making it easier to find and retrieve evidence, and enables users to start reporting out in the field by categorizing a recording and attaching notes to it.
-
The AXIS W100 Body Worn Camera offers a reliable option for law enforcement and security personnel in wearable surveillance, leveraging the quality & innovation of Axis to extend existing security systems.
(AXIS W100 Body Worn Camera is an easy-to-use, lightweight and robust body-worn camera that lets you store and manage video your way. It plugs right into your own Axis system or another system of your choice. Courtesy of Axis Communications and YouTube.)
Axis Communications (Second of Three)
Best Video Analytics Solution
-
AXIS Q1615-LE Mk III Network Camera
-
The AXIS Q1615-LE Mk III Network Camera is a top-of-the-line outdoor-ready camera that is ideal for city surveillance, transportation, and industrial applications.
-
With 120 fps in HDTV 1080p, the network camera offers exceptional video quality while capturing clear, detailed images of fast-moving objects and/or people regardless of challenging light conditions.

-
The camera is ideal for installation on the side of roadways or in poorly lit industrial lots and is equipped with Axis Lightfinder 2.0 and Axis Forensic WDR, which produces high-quality images with excellent color, detail, and sharpness.
-
AXIS Q1615-LE Mk III is equipped with advanced security functionality to safeguard the system and prevent unauthorized access.
-
With deep learning on the edge, the AXIS Q1615-LE Mk III platform is designed for third-party applications and allows analytics to run directly on AXIS Q1516-LE Mk III (on the edge), allowing for a faster, more scalable system.
-
With this ability to process powerful analytics, the camera is capable of edge-based automatic incident detection, counting, and anomaly detection, among other functions.
Axis Communications (Third of Three)
 Best IP Video Surveillance Solution
Best IP Video Surveillance Solution
-
AXIS Q6135-LE PTZ Network Camera
-
The AXIS Q6135-LE is a high-speed PTZ camera that offers OptimizedIR up to 250 m (820 ft) as well as Lightfinder 2.0 for clear, sharp overviews and excellent details in demanding light conditions.
It’s ideal for city surveillance in any unlit or low-light area – such as parks and alleys– eliminating the need for additional lighting.
(The AXIS Q6135-LE is a high-speed PTZ camera that offers OptimizedIR up to 250 m (820 ft) as well as Lightfinder 2.0 for clear, sharp overviews and excellent details in demanding light conditions. And, AXIS Object Analytics lets you detect and classify humans and vehicles. Courtesy of Axis Communications and YouTube.)
-
*Axis Communications, a Canon Company has been recognized in the 2020, 2019, 2018, and 2017 ‘ASTORS’ Awards Programs respectively.
BeyondTrust
Best Privileged Access Security Solution
-
Universal Privilege Mgmt Solutions
-
According to the White House, strengthening the cybersecurity of federal networks, systems, and data is one of the most important challenges the United States faces as a nation.

-
Controlling, monitoring, and auditing privileged access is extremely important to accomplish this mission by mitigating the risks posed by insider threats, preventing data breaches, and meeting compliance requirements.
-
With BeyondTrust agencies can keep pace, cost-effectively reduce IT security risk, confidently embrace innovation, and simplify the path to meet federal compliance mandates.
-
BeyondTrust’s Universal Privilege Management approach consists of three privilege pillars: Privileged Password Management, Endpoint Privilege Management, and Secure Remote Access.
(See a brief overview of BeyondTrust Universal Privilege Management Solutions. Courtesy of BeyondTrust and YouTube.)
-
*BeyondTrust was also recognized in the 2020, 2019, 2018 and 2016 ‘ASTORS’ Awards Programs.
BriefCam
Best Video Analytics Solution (Tie**)
-
BriefCam Video Analytics for Multi-Site Architectures
-
When it comes to deploying video surveillance systems, businesses with multiple sites or branches face several challenges.

-
From major retail chains to banks, utilities, transit agencies, among others, these organizations need the ability to record video locally on-site, but also seek to gain valuable insights through advanced video analytics across sites.
-
BriefCam’s innovative multi-site deployment architecture supports businesses with multiple locations or branches, enabling them to analyze cross-site surveillance video and realize the value of their video content.
-
Organizations can receive real-time alert notifications from across all locations, as well as visualize business intelligence from multiple sites into centralized dashboards, all while significantly reducing video processing bandwidth requirements.
(BriefCam introduces the new deployment option of a multi-site architecture. This enables businesses with multiple, distributed locations to view aggregate data from all remote sites to uncover trends across locations, optimize operations and boost real-time alerting and response – all while continuing to reap the benefits of BriefCam’s powerful analytics platform for making video searchable, actionable and quantifiable. Courtesy of BriefCam and YouTube.)
-
*BriefCam was also recognized in the 2020, 2019 and 2018 ‘ASTORS’ Awards Programs.
Canon U.S.A. (First of Two)
Best Email Security Solution
-
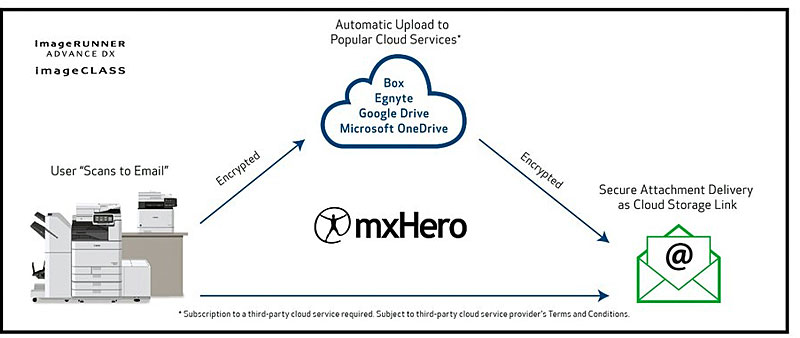
mxHero + Canon MFP
-
A cloud service for intelligent email management, mxHero™, can integrate onto a Canon multifunction printer (MFP) to help customers safely collaborate, govern, manage and share information.
-
By leveraging powerful storage platforms like Box (purchased separately), it can help create a cost-effective solution superior to single-purpose, document/email management products by replacing inbound and outbound email attachments with secure file links.
-
This solution is made to be compatible with most devices, helps to minimize end user effort, provides security measures to help control access to attachments (even when outside of the company) and can help screen malicious content.
-
Especially in today’s environment where solutions designed to help team’s collaborate while working in multiple places is important, services such as mxHero™ can help companies implement security features, govern and manage attachments while people aren’t able to physically connect face-to-face.
Canon U.S.A. (Second of Two)
Best IT Access Control & Authentication System
-
imageRUNNER ADVANCE DX Series + uniFLOW Online + Print via Cloud
-
The latest edition of the imageRUNNER ADVANCE platform, the imageRUNNER ADVANCE DX series with uniFLOW Online, is designed to help prepare its customers for the future of work through its simple, flexible design, advanced scanning, strong security, enhanced cloud features and user-friendly enhancements, like soft number keys similar to a smartphone or tablet.
-
The uniFLOW/uniFLOW Online platform is an end-to-end device management solution that can help improve the control and efficiency of imageRUNNER ADVANCE and other compatible multifunction print solutions through its security features.

-
The platform provides business employees the ability to control and monitor access to sensitive information with its enhanced authentication and user tracking features.
-
To help limit unauthorized use of devices and keep valuable and confident information safe, uniFLOW requires users to identify themselves at the solution, and its Secure Print functionality allows users to send sensitive documents to compatible network printers from desktops and compatible mobile devices.
-
When using this function, regardless of how users submit a print job, documents only print when the user is physically standing at the device and authenticates.
-
Through uniFLOW Online’s ability to store print jobs and release them only when users are in front of the supported Canon print device, solutions such as this help to limit document contamination, which is especially important in our current environment where mitigating contact between individuals is vital.
(Having the needs of the end-user in mind, we started to create a brand-new device user interface (UI) for uniFLOW Online. With a modern look and feel, uniFLOW Online focuses primarily on the login process on Canon imageRUNNER ADVANCE DX devices. It introduces the possibility of adapting the UI to suit customers’ own corporate identity. Subsequent development will expand the optimized user experience to secure printing and scanning functionalities. Courtesy of uniFLOW and YouTube.)
-
*Canon U.S.A. was also recognized with Multi-Award Wins in the 2020, 2019, 2018 and 2017 ‘ASTORS’ Awards Programs.
-
Additionally, Axis Communications, a Canon Company has been recognized in the 2020, 2019, 2018 and 2017 ‘ASTORS’ Awards Programs respectively.
Cellbusters
 Best Cell Phone Detection Solution (Tie**)
Best Cell Phone Detection Solution (Tie**)
-
Zone Protector
-
The Zone Protector™ from Cellbusters provides maximum protection for your environment by continuously scanning for cell phone and user-selectable RF transmissions, and is far more sophisticated than a cell phone detector.
-
Comparable to a spectrum analyzer, the Zone Protector™ has the ability to scan user-definable frequency ranges along with the ability to alert, notify, control a third party device, or simply log as soon as it detects relevant transmission activity.

-
Precise frequency filtering technology, managed and controlled by a 32-bit microprocessor, enables the Zone Protector™ to deliver accurate detection with virtually zero false positives.
-
Once cellular or appropriate RF activity is detected, the Zone Protector™ can be set to activate a choice of alerting options or to silently log all detected activity.
-
Additionally, Cellbusters Zone Protector has now been updated to detect 5G phones, proving a leading edge in the market, and protects investment in this technology for years to come.
(See a quick overview of the Zone Protector and the Zone Manger, both cell phone detection technology from Cellbusters. Courtesy of Cellbusters and YouTube.)
-
*Cellbusters was also recognized in all Six ‘ASTORS’ Awards Programs, respectively.
Certified Multi-Media Solutions
 Best Railroad/Mass Transit Security Solution
Best Railroad/Mass Transit Security Solution
-
TiniFiber
-
Certified Multi-Media Solutions Ltd, is being recognized for a complex installation of hybrid TiniFiber cable consisting of a 12-conductor power cable and a 12 strand Micro Armored Fiber Optic Cable under one jacket for the NYC Transit System to accommodate its CCTV camera system which is located below ground.

-
The project required a specific design and installation which would be minimally intrusive and incorporate both power and fiber under a single jacket due to space utilization and rodent protection.
-
Certified Multi-Media Solutions worked with the NYC, MTA’s design team to design and install this complex solution for the NYC, MTA.
CIS Mobile
Best Handheld Mobile Tech Solution
-
altOS
-
Smartphones are highly effective productivity tools, unfortunately, consumer mobile phones create an electronic trail that can put government employees at risk because they are built around collecting data to monetize the user.

-
Eliminating or minimizing these data trails is fundamentally at odds with the business models of the consumer-centric mobile eco-system which depends on data collection from mobile devices to sell targeted advertising, and OEM smartphones put government data at risk.
-
Additionally, it’s difficult to fully control the electronic trail left by consumer mobile phones, further exposing the presence and identity of individuals working in sensitive government, military, and intelligence roles.
-
In response, CIS Mobile developed altOS which was built exclusively for secure government use, using Android as a base but adding policy controls, secure containers, and management features into the platform.
-
In essence, it puts a new OS on the existing device to overcome the security challenges mentioned here to deliver the productivity of smartphones without the accompanying risk.
(Even approved government-certified devices leak user location, application use, and metadata back to 3rd party collectors however, altOS is different. It was built exclusively for secure government use, using Android as a base but adding policy controls, secure containers, and management features into the platform. Courtesy of CIS Mobile and YouTube.)
Cloudastructure
 Best Video Analytics Solution
Best Video Analytics Solution
-
Cloudastructure Video Surveillance Solution
-
Cloudastructure is a cloud-based surveillance platform integrated with powerful analytics, that uses machine learning (ML) computer vision to recognize objects, faces and more, to allow users to rapidly search video footage much like one does on the web through the company’s sophisticated object tagging capabilities.
-
The Cloudastructure cloud-based platform also offers an alternative to on-premises solutions, which can be costly to operate and scale and require on-site monitoring.
-
Cloudastructure, clients can securely store their recorded and live video feeds in the cloud through a browser, so they can safely store, index, access, monitor and review their surveillance footage in the cloud, 24/7 from any internet-enabled device.
(Cloud-based video surveillance keeps the enterprise safe and secure. Securely store, index and access footage in the cloud, so users always know what is happening, 24/7 from any internet enable device. Courtesy of Cloudastructure and Vimeo.)
CornellCookson (First of Two)
Best Vehicle Security Entrance Control
-
Extreme MicroCoil Grille
-
When you need security in an opening with limited vertical space, the Extreme High Performance MicroCoil® Grille – 500K Cycles is the answer.

-
Perfectly engineered to occupy the smallest amount of headroom on the market, this high-performance compact grille not only coils in nearly 50% less room than other security grilles but also provides higher performance, and engineered to handle at least 500,000 cycles (opens/closes) at speeds of up to 24” per second.
-
But, with the MicroCoil Grille, higher speeds do not mean you get a loud and clunky security grille, this low headroom parking security grille’s patented nested link system actually minimizes noise and vibrations – making it one of the quietest and smoothest coiling parking garage gates available today.
(See the Extreme High-Performance MicroCoil Grille – 500 Cycle in Action. Courtesy of CornellCookson and YouTube.)
CornellCookson (Second of Two)
Best Perimeter Protection Solution – Physical
-
The StoreDefender Door
-
Created to provide immediate security to store and building owners during times of unrest or unoccupied hours, the StoreDefender is not only a better choice for instant protection, but it can also be more cost-effective than other means of protection (such as plywood board-ups).

-
The StoreDefender™ Door was engineered to be a reliable solution to prevent theft and property damage, protecting against riot events and mob attacks.
-
More rigid and robust compared to traditional security doors, StoreDefender was created to be lift and impact-resistant and has been tested to withstand more than 4,500 pounds of effort to lift 3” and resists more than 2,500 pounds of pull force without exiting the guides.
-
Designed to safeguard property, merchandise, and most importantly, lives, the door ensures pharmaceutical facilities, cannabis dispensaries, high-end retail, and big-box chain stores can fortify perimeters against looting events and burglaries.

-
*CornellCookson, was also recognized in 2019 ‘ASTORS’ Awards Program.
CyberArk
Best Identification Management Solution
-
CyberArk Identity Security Platform
-
The CyberArk Identity Security Platform is an end-to-end identity access management solution that enforces privilege, enables access, and secures DevOps.
-
The CyberArk Identity Security platform is centered on privileged access management and offers the most complete and flexible set of least privilege-based identity and access capabilities, and is used to protect agencies across all three branches of the U.S. federal government – including multiple Department of Defense deployments

-
The CyberArk Identity Security platform is centered on privileged access management and offers the most complete and flexible set of least privilege-based identity and access capabilities, and is used to protect agencies across all three branches of the U.S. federal government – including multiple DoD deployments.
-
CyberArk delivers a comprehensive privileged access management solution designed to eliminate advanced cyber threats by identifying existing privileged accounts across networks, then proactively managing, monitoring, and protecting those accounts to reduce risk and improve security and compliance.
-
CyberArk continuously scans and monitors environments to discover and manage privileged credentials, isolates those credentials so they are never exposed to an end-user, isolates privileged sessions to safeguard critical systems, and automatically records and stores those sessions to enhance audit capabilities.
(In today’s hybrid and multi-cloud world, where every identity represents a potential attack path to an organization’s most valuable assets, traditional network barriers are not enough to secure the perimeter. That’s the importance of a robust Identity Security strategy. See how your organization can embrace a Zero Trust approach to protecting an ever-expanding number and diversity of identities. Courtesy of CyberArk and YouTube.)
- *CyberArk was also recognized in the 2020, 2019, and 2018 ‘ASTORS’ Homeland Security Awards Programs.
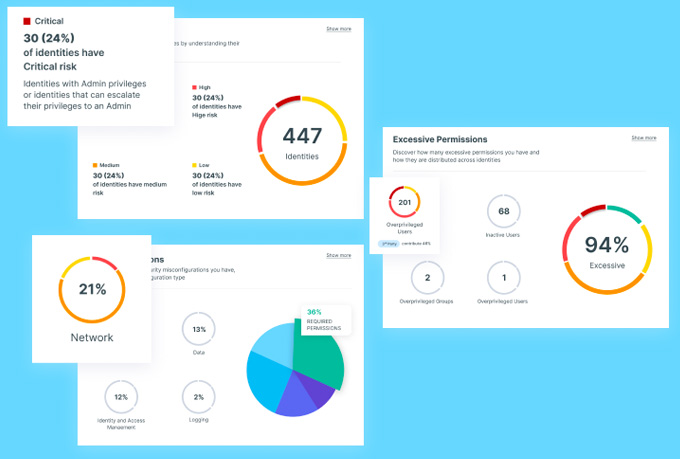
Cyberpion (First of Two)
Best External Attack Surface Mgmt
-
Every asset your customers and employees access when interacting with your company online makes up your online ecosystem.
-
These assets may be owned by your organization, owned and operated by a third-party vendor, or exist somewhere in your long chain of Nth-degree vendors, and this ecosystem represents an organization’s external attack surface.
-
Cyberpion’s leading Ecosystem Security platform continuously discovers, assesses, and alerts on vulnerabilities within your third-party, internet-facing assets, to provide security teams the opportunity to identify critical vulnerabilities within their online supply chains, infrastructure, and elsewhere, and remediate them before malicious actors exploit and abuse them.
-
Cyberpion’s continuous process of discovery, assessment, reporting, and protection across your entire ecosystem gives the necessary awareness for security teams to effectively protect the enterprise.
Cyberpion (Second of Two)
Best Cyber Security Risk Mgmt Solution
-
Cyberpion Ecosystem Security
-
What Do You Really Know About the Security Posture of Your Digital Ecosystem?
-
-
What about the security posture of your third-party vendors?
Cyberpion’s continuous process of discovery, assessment, reporting and protection across your entire ecosystem gives the necessary awareness for security teams to effectively protect the enterprise.
-
See the risks you’re exposed to with a Complimentary Cyberpion Online Ecosystem vulnerability assessment scan to help you assess and evaluate the vulnerabilities that threaten your cybersecurity, and gain a more accurate picture of your threat posture to reduce false positives.
-
Cyberpion assesses all of your organization’s owned (known and unknown) public-facing assets and their connected supply chain, to ensure that your security team takes action on accurate and reliable information.
Cyemptive Technologies (First of Two)
Best Anti-Malware Solution
-
Zero Trust Access Solutions
-
Cyemptive Zero Trust Access (CZTA) enables an unprecedented additional protection layer and provides a revolutionary approach for VPNs (Virtual Private Networks).

-
Cyemptive was the first to detect VPN networks being compromised and quickly informed the DHS of the issues, and have discovered more than 10 security holes in existing VPN technologies that are not getting detected by current leading technology perimeter defense firewalls.
-
CZTA is an optional add-on module to Cyemptive Perimeter Fortress technology solution leading a revolutionary defense for VPNs and your remote workforce.
-
This Cyemptive protection tool is prepared for, and can prevent, quantum computing-based attacks from penetrating VPNs.
Cyemptive Technologies (Second of Two)
Best Cyber End-to-End Encryption Solution
-
Cyemptive Perimeter Fortress
-
The experience of having your firewall compromised and fooled in real-time is a common problem that often goes unnoticed.
-
If you are not seeing thousands of attacks per day defended in your current firewall, then there is a high chance you are not seeing or detecting the ones getting through.

-
Cyemptive’s Perimeter Fortress (CPF) defense technology successfully stops many of today’s most advanced global hackers in seconds.
-
CPF handles root-level attacks and base firmware attacks with ease using their patented cyberslice technology, and found over 300 zero days in 2019 alone.
-
The company’s integrated protection platform prevents the most elite hackers from compromising your perimeter defenses.
Cymulate
Best Breach & Attack Simulation
-
Continuous Security Validation Platform
-
Cymulate SaaS-based Continuous Security Validation enables companies to challenge, assess, and test their security control simply and continuously even from their home.
-
Plug & Play. 7 Minutes to Deploy. Assure daily the operational effectiveness of your security stack that protect your IT environment, cloud initiatives, and critical data against threat evolutions.
-
Schedule a private demo today to see the benefits for your organization.
(See how you can operationalize threat intelligence and the MITRE ATT&CK framework for continuous purple teaming, to continuously challenge, assess, and optimize your security controls across the full cyber kill chain. Automated, comprehensive & prescriptive. Courtesy of Cymulate and YouTube.)
D-Fend Solutions
Best Persistent Aerial Monitoring Solution
-
EnforceAir
-
National and homeland security personnel face a wide variety of scenarios and drone threats, so the EnforceAir anti-drone product, features counter-drone, cyber, radio frequency (RF)-based takeover technology to provide users with operational agility and flexibility.
-
EnforceAir, in either autonomous or manual mode, detects, locates, and identifies rogue drones in your airspace and then neutralizes the threat by allowing you to take full control over the drone and land it safely in a predefined zone.
-
Since the system does not rely upon jammers or kinetic technology, EnforceAir avoids collateral damage, interference, disruption, and disturbance, and continuity prevails as communications, commerce, transportation, and everyday life smoothly proceed.
-
EnforceAir is lightweight and its core elements can be easily transferred, mounted, and configured within minutes, enabling personnel to go anywhere at any time, including vehicle, stationary and tactical installations.
(D-Fend Solutions focuses on the real threats from potentially dangerous drones so that varied organizations around the world can maintain full control of drone incidents in complex environments and be prepared for future threats. The EnforceAir anti-drone system, automatically executes radio frequency, cyber takeovers of rogue drones for safe landings and safe outcomes. Courtesy of D-Fend Solutions and YouTube.)
Data Theorem (First of Two)
Best Vulnerability Mgmt Solution
-
API Secure
-
The rapid growth of modern applications has led to a dramatic increase in the number of APIs developers are creating.
-
Cloud platforms such as Amazon Web Services, Microsoft Azure and Google Cloud Platform have introduced serverless services allowing developers to build applications at scale with less infrastructure complexity and lower costs.
-
However, as the adoption of these new cloud serverless services grows, it allows for the creation of rogue APIs called shadow APIs that operate outside of enterprise security.
(See how Data Theorem approaches API security. Identify your entire attack surface by discovering all APIs, hacking beyond the perimeter, and maintaining a superior security posture. We empower our customers with proactive ways to hack their APIs before attackers do. Courtesy of Data Theorem and YouTube.)
Data Theorem (Second of Two)
Best Breach & Attack Simulation
-
Cloud Secure
-
For cloud security, application & infrastructure teams need to address issues simultaneously using a full-stack approach, from cloud infrastructure to cloud applications.
-
Data Theorem’s Cloud Security product is CSPM + AppSec all-in-one to monitor users Cloud configs (CSPM), applications, microservices, serverless functions, key stores/keyvaults, Virtual Machines, Storage assets, Databases, etc.

-
Cloud Secure also ‘Hacks the Cloud’ on a daily basis in search of security vulnerabilities that can lead to data breaches, and ‘Protect the Cloud’ by preventing data breaches sourced from Cloud assets and configs.
-
Data Theorem’s Cloud analyzer continuously discovers vulnerabilities in multi-cloud environments and provides mitigation solutions in real-time.
-
As companies expand their global and cloud footprints, security teams are seeking new solutions to discover, inspect, and remediate their greatest internet-facing risks. This helps lock in stronger visibility across all modern apps and APIs, preventing data breaches.
-
Attack Surface Management extends beyond manual pen testing to provide a view into dangerous misconfigurations and process failures that can allow attackers easy access into cloud or web apps, or allow access to valuable data.
(Data Theorem delivers automated security for DevOps, ushering in a new era of DevSecOps, to help teams grow faster with fewer application security exposures. Courtesy of Data Theorem and YouTube.)
- *Data Theorem was also recognized in the 2020 ‘ASTORS’ Homeland Security Awards Program.
Databuoy Corporation
Best Gunshot Detection Solution
-
Shotpoint
-
Shotpoint is a highly-accurate gunshot detection and localization sensor network system first developed under research sponsored by DARPA, and is installed and protecting some of our most vulnerable citizens here in the United States.
-
Applicable for both indoor and outdoor environments, Shotpoint’s patented sensor mesh approach does more than just reliably detect shots, they fuse data from multiple sensors to localize on the source of gunfire in 3D.
-
Shotpoint works for all types of small arms, from handguns to rifles, and their patented fusion technique successfully eliminates all false alarms – and does not report echoes as shots.
(As gun violence continues with 2021 on pace to be the worst year in decades, Databuoy offers the Shotpoint® gunshot localization technology and Geofob™ mobile panic button to provide affordable, reliable, and field-proven technology with the highest performance standards in the industry. Courtesy of Databuoy and Vimeo.)
Dedrone
-
Best Airport/Aviation Security Solution (Tie**)
-
Dedrone
-
DedroneTracker counter-drone software, which can be hosted in the cloud or on-premise, uses the DedroneDNA database to recognize and classify RF, WiFi, and non-WiFi drones, plus triggers alerts and countermeasures.

-
DedroneTracker seamlessly integrates with a variety of 3rd-party sensing and threat mitigation technologies, enabling users to customize their platform and meet their specific needs and threat level.
-
A major metropolitan city in Southern Europe recently deployed less than a dozen DedroneSensors to detect, track and locate drones and their pilots across the city center.
-
The protected area includes internationally renowned tourist destinations, corporate and shopping districts, residential areas, and a port encompassing 50 square kilometers.
-
With Dedrone, organizations of all sizes can select and combine best-in-class sensors to personalize their airspace security solutions to protect their vulnerable airspace and effectively address their specific threat profile.
(See why Dedrone is a market leader in airspace security, protecting people, property and information against unauthorized and malicious drones. Courtesy of Dedrone and YouTube.)
- *Dedrone was also recognized in the 2019 ‘ASTORS’ Homeland Security Awards Program.
Durabook Americas (First of Two)
Best Handheld Mobile Tech Solution
-
Managing and securing sensitive data is critical to Homeland Security Professionals, so to meet their data management requirements the Durabook U11 features an SSD that’s quick and easy to remove – without having to open any covers – saving you time and effort.
-
Both Hardware and software-based encryption options are available based on each customer’s unique requirements.

In the field, portability equals productivity. The S14I weighs only 5.07 lbs and is 33% slimmer than the previous generation.
-
Durabook U11 is compact yet delivers reliability, power and functionality needed in today’s challenging environments. Equipped with its high-capacity battery, you can take advantage of non-stop operation for up to 24 hours with a single battery, making the U11 the market leader in power supply.
-
In addition, its hot-swappable battery enables Homeland Security professionals in the field to operate without interruption when charging isn’t possible.
-
In addition, this tablet is MIL-STD-810G certified, ANSI 12.12.01 C1D2 certified, and IP65 rated, assuring shock, 6-foot drop, and vibration protection, as well as the ability to withstand use in a wide range of temperatures.
-
What’s more, the unique, fanless design with 0 dBA means the U11 operates dependably and quietly.
U11 can easily be expanded to add functionality or another layer of security via an RFID reader, ExpressCard54, or PCMCIA Type II.
-
In addition, the U11 comes optionally with an embedded smart card reader. It is the only rugged tablet available today with the option of adding a second smart card reader via a built-in expansion module, which is useful for Homeland Security professionals who operate in the field or those collecting and transferring sensitive data and information.
(The U11 G2 fully rugged tablet delivers superb performance with Intel® 10th Generation CPUs and features a unique fanless design, the U11 provides the perfect blend of functionality, performance, and reliability. Plus, the high-speed data transmission capability of Intel® Dual Band Wireless AC 9260 and Bluetooth® V5.0 means smooth, congestion-free data processing at all times. For field operatives everywhere, the next generation of rugged mobile solutions has arrived. Courtesy of Durabook Federal and YouTube.)
Durabook Americas (Second of Two)
Best Data Storage Security Solution
-
S14I Laptop
-
For Homeland Security applications the Durabook S14I rugged laptop is widely used as an edge device in the frontend for data collection/data processing, source data visualization, Machine to Machine Communication, etc. (Edge Computing).
-
The S14I is engineered to combine military-grade durability, mobile functionality, computing performance, and long battery life for non-stop use, making it suitable for use in locations where rain or dust may be a regular occurrence.

-
For professionals who rely on drones for intelligence, the Durabook S14I has the data processing and storage power to analyze and map data from multiple drones from right from the Edge-decentralized data processing in close proximity to the devices themselves.
-
Additionally, the Durabook S14I can combine other in-field data, for example, from IoT and external sources, such as weather information, to help plan new aerial flight paths or arrange an instant repair.
-
The Durabook S14I is equipped with a smart card reader, fingerprint scanner, and hardware-based encryption (Trusted Platform Module (TPM 2.0)) to ensure storage security for sensitive data.
-
S14I is equipped with the latest NVMe PCIe SSD technology providing up to 1TB of storage, and can accommodate two additional internal SATA III SSD drives to maximize the onboard data storage.
-
The S14I’s media bay offers the user several setup options; instead of an optical disk drive, a third SATA III SSD storage can be mounted in the compartment, adding additional security using onboard RAID 0 & RAID 1 feature.
(The all-new Durabook S14I features the latest 11th Generation Intel® CPUs and class-leading 4’ drop spec/IP53 rating, pushing semi-rugged devices to a whole new level. The S14I is engineered to combine military-grade durability, field-worker functionality, computing performance, and long battery life for non-stop use, making it suitable for use in locations where rain or dust may be a regular occurrence. Courtesy of Durabook Federal and YouTube.)
- *Durabook (formerly GammaTech Computer Corporation), was also recognized in the 2017 ‘ASTORS’ Homeland Security Awards Program.
EAGL Technology (First of Two)
Best Body Worn Gunshot Detection Solution
-
BlueFly GSD
-
BlueFly™ is a body-worn Gunshot Detection Sensor (GSD), that uses patented technology designed specifically to detect gunshots near the wearer and monitor the wearer’s posture.

-
When gunshots are detected or an officer-down situation occurs, immediate and autonomous notifications are sent to the Real-Time Crime Center and/or Emergency Operations Center (RTCC/EOC).
-
These notifications can consist of text, email or voice calls to Computer-Aided Dispatch/Mobile Data Terminal (CAD/MDT) and smart devices, and are functions associated with EAGL’s adaptive response integration that includes real-time GPS location.
-
The BlueFly™ body-worn automatic gunshot and officer-down sensor also comes equipped with an integrated officer-activated panic button.
(Learn More about the EAGL gunshot detection system. Courtesy of EAGL Technology and YouTube.)
EAGL Technology (Second of Two)
Best Gunshot Detection Solution
-
EAGL Gunshot Detection & Lockdown System
-
The EAGL Technology Gunshot Detection and Lockdown System, which combines both indoor and outdoor detection sensors are wireless, battery-operated (7-year battery life), and use both Ballistic Energy Detection and Waveform Analysis to eliminate false alarms.
-

The FireFly® Indoor Gunshot Detection Sensor Additionally, the EAGL system can deliver ballistic analysis, live streaming video, automatic lockdown, and geofencing, full notification using text, email, voice, live notification via the systems GUI interface, and integrates directly into any Computer-Aided Dispatch (CAD) or management system using the EAGL application programming interface (API).
-
Through continued innovation and development, EAGL Technology continues to expand expectations by providing cutting-edge technology, industry-leading system response, and a suite of products that offer the most comprehensive Active-Shooter Emergency Response system available.
-
*EAGL Technology was also recognized in the 2020, 2019, and 2018 ‘ASTORS’ Homeland Security Awards Programs.
Ermetic
Best Cloud Infrastructure Entitlements Mgmt (CIEM) Solution
-
Ermetic Cloud Infrastructure Security Platform
-
Ermetic is an identity-first cloud infrastructure security platform that provides multi-cloud protection in an easy-to-deploy SaaS solution.
-
According to Gartner, the #1 threat to cloud infrastructure is entitlements and permissions, because identifying risky permissions and misconfigurations is hugely difficult and requires insight into the access that all users and services have and actually need.
-
Addressing this at scale calls for visibility into thousands of identities, policies, and resources – and mitigating the risks revealed.
-
Using Ermetic, enterprises can enforce least privilege access in their cloud for all identities, across the entire technology stack, and manage their security posture with ease.
-
Ermetic helps Security and DevOps stakeholders work together to ensure cloud security without impact to application continuity or speed to market.
(Ermetic is a public cloud security platform that governs identities and access entitlements, and enables enterprises to automatically enforce least privilege and mitigate risks at scale. Through continuous analysis of entitlements and activity, Ermetic powers least-privilege access policy definition and enforcement for both human and machine identities. Ermetic provides full-stack insight into the effective access entitlements granted by the configuration of identities, compute resources, data stores, and the network. Courtesy of Ermetic and YouTube.)
Everbridge
Best Federal Government Security Program
-
JARVISS
-
Everbridge Critical Event Management software solutions powers JARVISS, the U.S. DoD’s enterprise system for threat visibility so crisis teams can coordinate all response activities, teams, and resources to accelerate recovery times and maintain command and control when crises evolve into unanticipated scenarios.

-
JARVISS provides federal agencies one platform where senior leaders, antiterrorism officers, law enforcement personnel, and emergency managers can identify relevant threats, gain context around each threat to understand its importance, identify all assets that could be affected, and act to avoid or mitigate the impact of a risk event.
-
The Joint Analytic Real-Time Virtual Information Sharing System (JARVISS) primarily focuses on anti-terrorism and other security threats such as active shooters and natural disasters that might affect DoD operations.
-
The US Army and over 70 federal agencies are supported by the Everbridge CEM platform, and since the outbreak of COVID-19, JARVISS also provides support for ongoing threat analysis of the pandemic, giving Army commanders and other DoD users critical insight into the impact of COVID-19 to global operations across 400 military locations in 70 Countries.
(Everbridge Crisis Management provides organizations a single solution for business continuity, disaster recovery, and emergency communication. In one application, crisis teams can coordinate all response activities, teams, and resources to accelerate recovery times and maintain command and control when crises evolve into unanticipated scenarios. Courtesy of Everbridge and YouTube.)
-
*Everbridge was also recognized in the 2019, 2018 and 2017 ‘ASTORS’ Homeland Security Awards Programs.
Evolv Technology (First of Two)
Best Metal/Weapons Detection Solution
-
Evolv Express
-
Traditional security screening was not designed for today’s dynamic threats, so unlike metal detectors, manual bag checks, wanding, and other traditional solutions, Evolv Express® offers an innovative approach to physical security screening.

-
Evolv Express accelerates physical security screening while maintaining the highest degree of weapons detection accuracy.
-
It eliminates the friction that visitors, fans, patrons, employees, and students typically experience moving through security by screening them in a touchless manner.
-
This helps reduce the security risk of crowded security lines. It also drastically reduces false alarm rates and human errors by security guards.
(Spot weapons while ignoring harmless personal items. Evolv Express™ is the world’s first touchless security screening solution that meets all of the post-pandemic security screening requirements. Express is up to 10X faster and far more accurate than metal detectors because it uses new sensor technology and artificial intelligence, so visitors walk right through at a natural pace while carrying their phones, bags, and other personal items. Courtesy of Evolv Technology and YouTube.)
Evolv Technology (Second of Two)
Best Pedestrian Entrance Control Solution
-
At Evolv, they provide a secure and seamless screening experience, making it possible for venues of all kinds to keep visitors safe from concealed weapons, public health threats, and intruders.
-
Evolve is a mission-driven company headquartered and manufactured in the United States with a proven track record in screening people for threats without sacrificing the visitor experience.
-
People screening that’s intelligent, low-profile, and highly accurate — that’s what they do.
(Evolv Express™ is the first no-stop weapons-screening system built to automatically screen groups of people as they walk through without slowing or stopping. Express screens visitors individually or together, while automatically differentiating weapons from personal items. It is the fastest weapons-screening system on the market, consistently screening 60 people every minute for firearms and other threats. That’s 3,600 people per hour – 10X faster than a traditional checkpoint system. Courtesy of Evolv Technology and YouTube.)
-
*Evolv Technology was also recognized in the 2020, 2019 and 2018 ‘ASTORS’ Homeland Security Awards Programs.
Fiber SenSys
Best Perimeter Protection Solution
-
Terrain Defender
-
The need for reliable buried line sensors to secure applications including military, VIP and critical infrastructure is growing while the tolerance of faults/nuisance alarms is declining.
-
Customer requests and advances in RF technologies led Fiber SenSys, Inc. to develop the Terrain Defender TD100™ point location buried line sensor system.

-
The TD100™ BLS represents the latest advancements in coaxial perimeter intrusion detection, using a pair of ported coaxial cables, running parallel to form the sensor, and processors at each end pair sense disturbances using for real-time correlation which dramatically increases the performance of the system.
-
Key features of the Terrain Defender include point locating to within one-meter, virtual zoning, redundant bi-directional signal processing, and terrain-following volumetric sensing, which can be deployed in soil or other organic materials as well as under asphalt and concrete.
(See the key benefits of the TD100™ BLS volumetric point location intrusion sensor system, which was designed for the most critical sites in the world. Courtesy of Fiber SenSys, Inc. and YouTube.)
-
*Fiber SenSys was also recognized in the 2016 ‘ASTORS’ Homeland Security Awards Programs.
Forcepoint
Best Cyber Critical Infrastructure Solution
-
Forcepoint Data Diode
-
Government organizations need to be able to move data from an unclassified network to a classified one with the assurance that data never moves in the opposite direction.

-
The Forcepoint Data Diode enables rapid, uni-directional, automated transfer of highly complex data to segment and protect networks, devices, and other digital assets (including databases, historians, SCADA, PLCs, DCS, and more) from external cyber threats.
-
With a diode, data is transmitted one way, much like an ATM offers one-way cash transfers. The customer doesn’t have access to the whole vault—just an authorized amount.
-
This cost-effective solution integrates seamlessly with cross-domain technologies, ensuring one-way transfer traffic can also be deeply inspected at the content level.
(See how you can access and transfer sensitive data resident on multiple, separate networks to secure information sharing and mission success. Protect the human point with Forcepoint Cross Domain Solutions. Courtesy of Forcepoint and YouTube.)
-
*Forcepoint was also a Winner in the 2019, and 2018 ‘ASTORS’ Homeland Security Awards Program.
Fortem Technologies (First of Two)
Best Persistent Aerial Monitoring Solution
-
The SkyDome® 3.7 is a Counter-UAS System that can anticipate rouge drone vulnerabilities, alert personnel, cue defensive measures or launch a drone to autonomously neutralize malicious drones, so neither civilians nor communities are harmed, and minimize collateral damage in urban environments.

-
The SkyDome System has evolved to safely defeat larger and multiple targets where other systems are limited by cost, size, power, range, safety, or single drone targeting.
-
The 3.7 update is an example of that natural evolution where updates are added to a fundamentally disruptive autonomous architecture to create real, viable, ongoing solutions to the evolving drone threats.
-
Flexible and portable, the SkyDome® System deploys as a permanent installation or as part of a mobile solution, and is deployed at world-class venues, military bases, airports and infrastructures around the world and provides an effective and reliable solution.
(See a Live Virtual Demo of a prior SkyDome® System courtesy of Fortem Technologies and YouTube.)
Fortem Technologies (Second of Two)
Best Perimeter Protection Solution
-
SkyDome System 3.7 also pairs DroneHunter’s extensive mitigation range with a long-range camera option that extends the ability to validate a target visually.

-
While many competing drone solutions utilize camera systems that only have a ~30X zoom, SkyDome System 3.7 offers visual validation up to three times further utilizing an 88X zoom camera.
-
In conjunction with Fortem TrueView radar, this enhanced visual validation range now allows Fortem to boast one of the longest end-to-end detection, validation, and mitigation ranges in the industry.
-
SkyDome System 3.7 also introduced urban clutter suppression algorithms which allows the system to accurately view threatening drones in urban and other high clutter environments.
(Drone sales have exploded in the past few years, filling the air with millions of new aircraft. Simple modifications to these drones by criminals and terrorists have left people, privacy and physical and intellectual property totally exposed. Courtesy of Fortem Technologies and YouTube.)
Fortior Solutions
Best Access Control & Authentication Solution
-
The Fortior Solutions RAPIDGate Program is a patented, award-winning, and SAFETY Act-Designated identity, access and security solution that boasts 99.97% uptime, and serves the government, military, and critical infrastructure sectors, fulfilling end-to-end identity management needs and accommodating a wide set of compliance specifications.

-
The RAPIDGate program is a complete vendor management solution that includes verification of company sponsorship, company enrollment, multi-language kiosk based registration, individual biographic and biometric collection, equipment, commercial background screenings, DOJ/FBI NCIC/III checks (subject to approval of the relevant government authorities)
-
The RAPIDGate® and RAPID-RCx® programs provided unparalleled perimeter control at some of the most security-conscious organizations in the world including, the U.S. Army, U.S. Coast Guard, U.S. Navy, U.S. Marine Corps, and NASA among others.
(See RAPIDGate®, a high-assurance identity management program for vendors, contractors and service providers who require escorted or authorized access to secure facilities or sensitive corporate resources, and guard against threats such as unauthorized access, identity theft, fraud or cyber-crime. Courtesy of Fortior Solutions and Vimeo.)

-
*AST is delighted to welcome Fortior Solutions (formerly SureID) which was recognized in the 2016 ‘ASTORS’, as a New Premier Awards Sponsor in the 2021 ‘ASTORS’ Homeland Security Awards Program.
Fūsus
Best Investigation /Surveillance/ Detection
-
Fūsus Real-Time Crime Center in the Cloud
-
Whether it’s a natural disaster, an incident at a major event, or an active shooter or terrorist attack, situations inevitably arise where a multi-agency, multi-jurisdictional task force is required to immediately respond.

-
The Fūsus Real-Time Crime Center in the Cloud’s (RTC3s) video intelligence and map-based awareness interface serves as the central integration point for Law Enforcement agencies’ surveillance, security, and life safety technology.
-
Whether it’s a UAV, a traffic camera, a private cell phone video, a building security camera, or a bomb disposal robot, Fūsus can extract the live video feed and send it to your emergency operations center and officers in the field.
-
Fūsus RTC3 creates a public safety ecosystem that combines video with other utilities like Computer Aided Dispatch (CAD) data, gunfire detectors, real-time officer geolocator feeds, a registry map of all the public and private cameras in your region, a multi-media tips line for the public, and a digital evidence vault for investigators.
(See how Fūsus Real Time Crime Center In The Cloud Works for cities, schools, & businesses. Courtesy of Fūsus and YouTube.)
-
*Fūsus was also recognized in the 2020 ‘ASTORS’ Homeland Security Awards Program.
Gallagher (First of Two)
Best Access Control & Authentication Solution
-
Command Centre Mobile
-
The Command Centre Mobile App allows you to extend your security and access control directly to where you need it, on or off-site.

-
Whether your security staff are on guard or on patrol, Command Centre Mobile allows them to spend more time away from their desk, while still maintaining complete awareness of what’s happening on-site and allowing them to manage everyday security issues from wherever they are.
-
Downloadable from the Apple App and Google Play stores, this software provides you with the ability to manage your security securely from anywhere, on or off the corporate network.
-
The app interfaces directly with Gallagher Command Centre, providing a secure link to the site management capabilities that already bring security and business efficiency to your site.
(The Command Centre Mobile App from Gallagher allows you to extend your security and access control directly to where you need it. Whether your security staff are on guard or on patrol, Command Centre Mobile allows them to spend more time away from their desk, while still maintaining complete awareness of what’s happening on-site and allowing them to manage everyday security issues from wherever they are. Courtesy of Gallagher and YouTube.)
Gallagher (Second of Two)
Best Perimeter Protection Solution – Physical
-
Monitored Pulse Fence System
-
Gallagher offers a range of advanced perimeter security solutions founded on two core principles: deterrence and detection.

-
Configured and controlled using Gallagher Command Centre, our effective and reliable solutions can be managed and monitored across multiple sites from one central location.
-
Our cost-effective monitored pulse fence system consists of a grid of energized, high tensile wires that can be constructed inside a new or existing perimeter fence.
-
The monitored wires detect unauthorized entry or exit into defined areas and trigger instant alerts.
(Gallagher Security’s perimeter detection solutions offer quick and reliable detection of unauthorized entry to your site. As part of a responsive security approach, our sensors can trigger alarms without the intruder being aware, prompting video verification of the intrusion, or triggering an escalated security response. Courtesy of Gallagher and YouTube.)
-
*Gallagher was also recognized in the 2020, and 2019 ‘ASTORS’ Homeland Security Awards Program.
Genasys (First of Two)
Best Long Range Acoustic Hailing Solution
-
LRAD 1000Xi
-
The LRAD 1000Xi is a power efficient, long distance communication system designed for applications ranging from critical infrastructure protection to territorial water, border and port security, and large vessel and vehicle installations.

-
Featuring a rugged carbon fiber emitter head integrated with electronics and amplification, the LRAD 1000Xi comes standard with an MP3 Control Module for playing recorded messages and an all-weather microphone for live broadcasts.
-
The MP3 Control module also enables remote operation of the device from safe locations. Superior voice intelligibility and an extended frequency range ensure broadcasts are clearly heard and understood over wind, engine and background noise.
-
The LRAD 1000Xi provides a long-range communications capability to issue authoritative voice commands and attention-commanding deterrent tones to determine intent, safely enhance response capabilities, modify behavior, and scale the use of force if necessary.
Genasys (Second of Two)
Best Mass Notification Solution – Hardware
-
Genasys 360XT
-
During disasters and emergency situations, the ability to quickly deploy communication systems that broadcast exceptionally intelligible voice messages locally and over large areas is crucial to ensure public safety.

-
The Genasys 360XT delivers LRAD’s renowned, highly intelligible voice and alert tone broadcasts with uniform 360° coverage from a rapidly deployable, telescoping 30-foot pneumatic mast.
-
The Genasys 360XT is integrated and mounted on a fully self-contained, ruggedized trailer featuring securely mounted, lockable electronics and equipment enclosures containing the amplifier modules and battery pneumatic systems.
-
The mobile Genasys 360XT comes standard with a Genasys 360X dual emitter configuration that provides up to an 850-meter radius of communication coverage.
(Atherton and Menlo Park, CA fire, police and public safety officials experience the superiority of a Genasys Mass Notification system versus a siren installation. Courtesy of Genasus and YouTube.)
-
*Genasys Inc. (formerly LRAD) has now been recognized in their Sixth Consecutive Year in the Annual ‘ASTORS’ Homeland Security Awards.
Genetec
Best License Plate Recognition Solution
-
Genetec AutoVu
-
The Security Center AutoVu automatic license plate recognition (ALPR) system alerts users to wanted or unpermitted vehicles, even when they’re not looking for them.
-
This solution gives users real-time insights into your environment while helping your team work more efficiently.

-
Choose between fixed or mobile ALPR, or install both, as users also can unify the AutoVu solution with video and other systems to get a complete picture of any situation.
-
Genetec was also recognized in the 2017 ‘ASTORS’ Homeland Security Awards Program.
Global Elite Group
-
Best Airport/Aviation Security Solution (Tie**)
-
Airport/Aviation Security Solution
-
Global Elite Group oversees the security of over 60 clients across the aviation industry, including international airlines, and regional airports.
-
In the 17 years since the company was founded, a lot of growth has taken place and this once regional provider has a far-reaching reputation for delivering outstanding value and a customized approach for each client’s needs.

-
Most recently, Global Elite Group has been acquired by Securitas Transport Aviation Services USA for USD$22 million reflecting the growth and value of the company since it began.
Global Elite’s reputation outside of its aviation security offerings is excellent for delivering security services, emergency management and consulting services to governments and businesses throughout the world.
-
Global’s foundation offerings focus on aviation security, which makes up 95% of its business portfolio and has been the driver for developing a complete range of AVSEC services that are tailored to the express needs of each customer from aircraft guarding and airside escorting, baggage pilferage investigations/prevention and cargo guarding, escorting & screening, to emergency response support, passenger behavioral assessments & verification and even explosives/narcotics canine units.
-
*Global Elite Group was also recognized in the 2020, 2019, 2018, and 2017 ‘ASTORS’ Homeland Security Awards Programs, respectively.
GrammaTech
Best Software Composition Analysis
-
CodeSentry
-
CodeSentry is derived from GrammaTech’s ground-breaking binary code analysis research, which achieves deep scalable analysis without the need for source code and is suitable for enterprise-wide adoption.
-
Binary analysis is both efficient and less error-prone than conventional SCA tools and due to CodeSentry’s high precision and recall results in fewer missed vulnerabilities and fewer false positives.
-
The key advantage of CodeSentry is the ability to interrogate – at the binary level – both open source software and the third-party software that is now so commonly used.
(At least 90% of corporations use third-party software and 95% of proprietary or custom software applications they create contain third-party components. To overcome this blind spot in assessing third-party software inventory and risk, CodeSentry allows security professionals to measure and manage the risk associated with open source vulnerabilities in third-party software quickly and easily. Courtesy of GrammaTech and Youtube.)
guardDog Solutions (First of Three)

Best Cyber Analytics Solution
-
guardDog.AI
-
guardDog Protective Cloud Services (PCS) is an AI-powered network security solution that doesn’t require cyber security expertise to operate.
-
Once activated, users’ Fido device goes to work by detecting threats and vulnerabilities on your network.
-
From there, the users’ cloud dashboard displays incidents by threat level and shows them information on how to resolve the issues before they become a problem.
guardDog Solutions (Second of Three)
Best Vulnerability Mgmt Solution
-
guardDog.AI
-
Installation is a snap, and protection is a power light away.
-
Secure a home, a small office, a large enterprise, or any other organization with a cyber security management solution made easy that offers services to match the user’s needs.

-
How it Works: Unbox your Fido device, connect to your network, and register. From the moment the power light appears, protection begins. Fido gets to know your network and your devices.
-
It recognizes intruders and defends your network and devices. When someone attacks, it deploys automated countermeasures. User’s networks and devices are scanned vigilantly to protect against the known, and the unknown.
guardDog Solutions (Third of Three)
Best Threat Intelligence Solution
-
guardDog.AI
-
No Experience Required
-
Last year alone there were over 12,000 new vulnerability exploits that emerged, and no human could really keep up with that. guardDog’s ai-powered service learns about these attacks and keeps user’s Fido devices up to date.
-
The training never stops to prevent a crisis before it happens.
-
guardDog.ai has developed a cloud-based software service with a companion device that works together to simplify network security.
-
The solution exposes invisible threats on networks, and the devices attached to them, with patented technology to address and prevent cybersecurity threats before they compromise network environments.
Hanwha Techwin America (First of Two)
Best Cyber Security Solution (Tie**)
-
Wisenet 7
-
Security requirements change and market trends evolve, yet one constant remains the need for intelligent networked surveillance solutions – in every market, for any application.
-
At the heart of Hanwha Techwin’s new product development is the Wisenet 7 System on a Chip (SoC), the companies most technology-intensive, innovative, and feature-rich SoC, which features vivid 4K resolution, extreme WDR with scene analysis technology, sharper images with enhanced noise reduction technology, DIS with built-in gyro sensor, enhanced lens distortion correction, and end-to-end cybersecurity.
(With its own device certificate issuing system, Root CA, the Wisenet 7 camera lineup offers the highest levels of cybersecurity that satisfies stringent UL CAP standards as well as the company’s own requirements for product reliability and design innovation. Courtesy of Hanwha Techwin America and YouTube.)
Hanwha Techwin America (Second of Two)
Best IP Video Surveillance Solution
-
PNV – A9081R AI 4K IR Outdoor Vandal Dome AI Camera
-
Part of the Wisenet P series, Hanwha’s AI-based PNV-A9081 R AI camera captures pristine images at up to 4K resolution while including powerful, in-camera deep learning algorithms for advanced object detection, classification and error-free analytics.
-
Utilizing object recognition versus motion detection all but eliminates false alarms while also providing valuable business and operations insight.
(Wisenet P series AI cameras feature resolutions of up to 4K and are equipped with onboard license-free intelligent video analytics including mask detection and AI-based human and vehicle object classification with attribute extraction for easy forensic review. Courtesy of Hanwha Techwin America and YouTube.)
HID Global (First of Three)

Best Smart Card/Reader System
-
HID Element
-
HID ELEMENT® is the industry’s first heavy-duty, fully modular desktop-based card personalization portfolio that establishes a new category for mid-range and high-volume market segments.
-
The portfolio’s enhanced card production capabilities, flexible system architecture, and cost-effective deployment model empower organizations to create custom, secure IDs and financial card production solutions for a variety of use cases and applications.
(Designed for industrial ID and financial card personalization, the new HID® ELEMENT offers high-resolution, precision UV inkjet printing, optional laser engraving and an array of encoding options. Courtesy of HID Global and YouTube.)
-
*Hanwha Techwin America was also recognized in the 2019 and 2018 ‘ASTORS’ Homeland Security Awards Programs.
HID Global (Second of Three)

Best Back to Work Monitoring Solution
-
HID Location Services for Workplace Safety
-
HID Location Services delivers an IoT Enterprise Enablement Platform to ensure workplaces are safe for your employees to return to the office or operations floor — and to comply with new government mandates designed to reduce the potential threat of communicable diseases.
-
HID provides organizations a secure and digital solution to address social/physical distancing, contact tracing, and hand hygiene that leverages real-time location (RTL), proximity-based location services, and cloud technologies.
(To address the challenges of today’s workplace, it’s imperative to have immediate access to information that optimizes safety, delivers on compliance, and reduces facility costs while creating a better employee and visitor experience. Courtesy of HID Global and YouTube.)
HID Global (Third of Three)

Best Image Technologies Solution
-
HID Crescendo & WorkforceID Digital Credential Mgr
-
Enterprise IT security environments are often complex hybrid systems.
-
WorkforceID Digital Credential Manager streamlines this complexity by centrally managing many credentials and certificates.
-
Managed in a multi-tenant cloud environment through Amazon AWS, organizations can begin issuing and managing credentials in just a few hours, and supports a wide range of authenticators and form factors.
-
Deploy and manage a converged badge protecting access to buildings and IT systems with the Crescendo C2300 smart card or manage Crescendo USB security keys.
(Meet the HID Crescendo family of FIDO-enabled smart cards that streamline access for all IT and physical workspaces in a single credential without passwords. Courtesy of HID Global and YouTube.)
-
*HID Global was also recognized with Multiple Wins in the 2020 ‘ASTORS’ Awards, as well as Wins in the 2019, 2018, and 2017 ‘ASTORS’ Homeland Awards Programs, respectively.
High Rise Escape Systems
Best Disaster Preparedness, Disaster Recovery System
-
Guardian Evacuation System
-
The Guardian Evacuation System developed a fixed and/or portable escape system to attach to a structure, designed to mitigate means of egress for anyone living or working above the 2nd floor, including: government buildings, embassies, barracks, hospitals, air traffic control towers, apartments, condominiums, hotels, industrial and job sites, theme parks, cranes, oil platforms, ships and more.

-
High Rise Escape Systems (HRES) accomplished this in a combination of several simple, low-tech devices that require no power, are inexpensive, have a long shelf-life and are easy to use.
-
Using a Controlled Descent Device (CDD) which works like a pulley, a user slides a one of two permanently attached escape harnesses over them, exits off of a balcony/roof structure or out of a window and the CDD slowly lowers them automatically at the rate of 3 feet per second.
-
As the first user descends, the opposite end of the cable automatically retracts and reloads the CDD with the remaining escape harness for the next evacuee.
-
Then the process repeats. Everyone gets out.
-
The United States Military has been utilizing High Rise Escape Systems Guardian Escape Systems on Air Traffic Control Towers for years, which includes the Ellsworth AFB, Dyess AFB, Vandenburg AFB, Edwards AFB, Tinker AFB, Maxwell AFB and Patrick AFB as well as Army and Air National Guard installations such as Alpena CRTC, Grayling Air Gunnery Range & Selfridge ANG.
(See the HRES device in action as designed for the Dyess AFB ACT Tower which is much safer than taking the stairs or the elevator. Courtesy of Dyess AFB & YouTube.)
-
*HRES was also recognized in the 2020, 2019, 2018, and 2017 ‘ASTORS’ Homeland Awards Programs, respectively.
Hypori
Best Mobile Tech Solution
-
Hypori Virtual Mobility
-
Hypori is an Enterprise Virtual Mobility solution designed for Government secure teleworkers in Homeland and Defense that lets Work From Home (WFH) users perform business tasks on their mobile devices while leaving zero footprint and guaranteeing 100% separation of personal and enterprise data.
-
Hypori empowers users to access sensitive data from their remote Bring Your Own Device (BYOD) devices, to enable secure teleworking.
-
Hypori Virtual Mobility gives enterprise users access to a resilient cloud’s power, speed, and security from any physical edge device.
(Hypori is proud to be the solution of choice for those who can’t afford security breaches or mission failure. Their military-grade technology enables the most demanding users – like DoD and the IC community – to remotely access their highly sensitive data anywhere, anytime from any edge device. Courtesy of Hypori and YouTube.)
iboss
Best Network Security Solution (Tie**)
-
iboss Cloud
-
iboss cloud secures user Internet access on any device, from any location, in the cloud, shifting the focus from following perimeters to following users so that consistent cloud security is applied while users are in the office, on the road or working from home.
-
Built on a proprietary containerized architecture designed 100% for the cloud, iboss users are always connected to iboss cloud, regardless of device or location, to ensure all Internet traffic is secured for compliance, web filtering, malware defense and data loss at all times.
-
Since iboss cloud lives in the cloud, security goes where users go with elastic and instant scaling to meet the demands of the cloud-first future.
-
The iboss’ SaaS solution significantly reduces management costs and offers a faster, more distributed alternative to previous on-premise gateways.
(The iboss cloud secures user Internet access on any device, from any location, in the cloud. It is a cloud-based platform with a focus on following users instead of perimeters to ensure that Internet access is always secure regardless of user location. Courtesy of iboss and YouTube.)
-
*iboss was also recognized in the 2020 ‘ASTORS’ Homeland Awards Program.
ICEsoft Technologies
Best Alert Notification Solution
-
Voyent Alert!
-
Voyent Alert! is a multi-purpose notification system and alerting app that is designed to support communities through rapid dissemination of targeted information with enriched media alerts for both critical emergencies and day-to-day notifications.
-
Voyent Alert! goes beyond the traditional offerings to include personalized information, maps, visuals, and attachments, for enriched alerts that provide users with relevant information, allowing them to make better, more informed decisions, which helps increase registration and engagement among users.
(Voyent Alert! is an affordable multipurpose mass notification service designed to meet the needs of small and medium-sized populations. Courtesy of ICEsoft Technologies and YouTube.)
Identiv
Best Cyber Security Solution (Tie**)
-
uTrust FIDO2 GOV Security Keys
-
uTrust FIDO2 GOV Security Keys are strong near field communication (NFC) multi-factor authentication (MFA) devices, providing FIPS 140-3 validation and assurance level 3 (AAL3) of NIST SP800-63B guidance for regulatory compliance.
-
With multi-protocol FIDO U2F, FIDO2, smart card (PIV), OpenPGP, and OTP support, uTrust FIDO2 GOV Security Keys are resistant to phishing attacks, safeguarding your credentials and accounts.
(Identiv’s uTrust FIDO2 NFC Security Keys are made in the U.S.A. and provide a simple, strong authentication experience that eliminates the need for passwords. Our security keys support working from home and allow individuals, businesses, and government agencies to replace passwords with a secure, fast, scalable, cost-effective login solution. Courtesy of Identiv and YouTube.)
-
*Identiv was also recognized in the 2020, 2019, 2018 and 2017 ‘ASTORS’ Homeland Awards Programs, respectively.
Intelligent Waves
Best Cyber End-to-End Encryption Solution
-
GRAYPATH & Phantom Solutions
-
GRAYPATH & Phantom Solutions
-
Intelligent Waves (IW) is a cutting-edge IT systems integrator delivering high-impact transformational IT solutions to the U.S. Government’s most mission-critical challenges, and this year introduced several leading-edge disruptive cybersecurity innovations.

-
GRAYPATH is the next generation of cybersecurity expeditionary communications, in a simple, asymmetric solution that ensures robust, reliable, secure, non-attributable global communication for Homeland Security and special operations of the U.S. military.
-
Phantom provides the ability for organizations to access foreign points of presence to conduct remote open-source information gathering and research while at the same time protecting organizations and individuals from exposure to foreign intelligence, achieved by combining the GRAYPATH software-defined obfuscated network with the managed attribution capability of the Phantom platform in a secure but unclassified package.
(Unlike VPN solutions that do not address or solve the common capability gaps, GRAYPATH DOES. GRAYPATH is a seamless, easy-to-deploy asymmetric solution that ensures robust, reliable, secure,non-attributable global communication. Courtesy of Intelligent Waves and Vimeo.)
Intrado Corporation (First of Two)

Best Risk, Crisis Mgmt Solution
-
Intrado SchoolMessenger
-
Schools across North America are leveraging Intrado’s trusted solutions for school community engagement to help them navigate the challenges associated with the COVID-19 pandemic as students return to school, and users can combine school notification, mobile apps, and web content management all under one, easy-to-use platform.
-
It’s part of Intrado Safety Shield, an end-to-end safety management platform designed to provide prevention, preparation, and active response for threats faced by educational organizations of all kinds, leveraging the company’s comprehensive and secure notifications capabilities along with connectivity to the entire public safety ecosystem and access to expanding sources of threat-relevant data.
(See how the Intrado Safety Suite can create safer environments for students, faculty, and parents by providing an end-to-end solution to manage safety events from incident detection all the way to resolution. Courtesy of Intrado and YouTube.)
This unique and powerful combination provides information and insights to 911 dispatchers, first responders, and educational leaders, allowing them to make more informed decisions and ultimately protect their communities more effectively.
Intrado Corporation (Second of Two)

Best IT Disaster Preparedness & Recovery Solution
-
Intrado Safety Suite
-
Intrado Safety Shield offers a set of tools to help educational institutions enhance school safety and improve their emergency response capabilities.
-
Intrado Safety Shield unites Intrado’s 911 and mass notification capabilities with panic buttons, first responder collaboration, and emergency response planning solutions to create a comprehensive crisis prevention and response offering.

-
Additionally, Intrado Safety Shield provides a single operational view and integrates with other relevant software to create a simplified hub for emergency response activities.
-
Unlike point solutions that only address part of the problem, or which lack a well-established connection to 911 infrastructure, Intrado Safety Shield offers a complete solution that helps schools prevent, prepare for, respond to, and recover effectively from school emergencies large and small.
-
Intrado has long-term relationships with thousands of public safety answering points, government agencies, and other relevant organizations, and with over 63,000 schools on its client roster and decades of experience in K-12 education, Intrado has more experience serving educational institutions than any other provider.
-
*Intrado was also a Multiple-Award Winner in the 2020 ‘ASTORS’ Homeland Awards Programs.
IonSense
Best CBRNE Detection Solution
-
DART-MS
-
DART® stands for Direct Analysis in Real-Time, and provides new ionization for rapid, non-contact surface sampling of compounds.
-
Analysis of hundreds of chemicals, including pharmaceuticals, their metabolites, peptides, oligosaccharides, synthetic organic molecules, organometallics, explosives, and toxins has shown that the DART® is a versatile method for rapid detection of analytes.
-
These chemicals have been detected on surfaces including concrete, asphalt, human skin, currency, paper stock, vegetables, fruit, and even clothing.
(See how the Pulsed Gas DART®-MS System will help you rapidly explore new chemistry and identify new compounds. Courtesy of IonSens and YouTube.)
IPVideo Corporation (First of Four)
Best Sound & Chemical Incident Detection
-
HALO SMART SENSOR 2.5
-
IPVideo Corporation has introduced firmware 2.5 of the HALO IOT Smart Sensor which now provides instant Health and Indoor Air Quality readings and alerts.
-
HALO, a real-time vape detector, is truly an all-in-one security device that includes sound alert incident management alerts for spoken keywords, advanced gunshot detection, and includes chemical incident detection and can assist with the workplace return from COVID 19.

-
For example, a daughter in her dorm room, a hotel housekeeper, a patient under duress, a student in a hazing incident, or your elderly parent living by themselves can alert security to an attack or emergency situation in real-time by shouting a keyword like “HALO HELP”.
-
The audio is still not being recorded to maintain privacy, but the alerts are automatically sent to security for immediate response. To help diffuse situations, the alerts can also trigger an audible message that an emergency has been declared and security has been notified.
-
Another new feature is the addition of machine learning capabilities to establish audible level “normalcies”. Advanced gunshot detection audio analytics can trigger a facility lockdown and an emergency call response via the integration of third-party security applications when detected.
(See how the HALO IOT Smart Sensor will detect vape in bathrooms, locker rooms, etc. HALO Smart Sensor can monitor the air in your facility for chemicals, temperature, quality, and more! Courtesy of IPVideo Corporation and YouTube.)
IPVideo Corporation (Second of Four)
Best Cell Phone Detection Solution (Tie**)
-
ViewScan 2.0
-
ViewScan, the concealed weapons detection and cell phone detection system, by IPVideo Corporation has just been updated with version 2.0 allowing for greater flexibility and faster processing with weapons and loss prevention screening.
-
ViewScan 2.0 comes with all-new features and updates, such as an updated new browser, optional mobile trolley, an improved camera, enhanced cybersecurity and reporting, as well as additional capabilities for 3rd party integration.

Does not emit radiation. Safe for all including those with medical devices or may be pregnant.
-
What stands out the most about ViewScan compared to other concealed weapon detection systems is that it detects disturbances in the earth’s electromagnetic field, making this a safe passive system for all that go through it without emitting radiation or affecting medical devices.
-
All non-ferrous weaponry and theft items can be detected whether they are concealed in the body or belongings.
-
With the new ViewScan 2.0 interface, you can capture the three most current screens, conduct remote monitoring, as well as view up to five simultaneous ViewScan systems per window. These improvements allow for greater flexibility and a faster screening process.
-
The ViewScan 2.0 system now includes a trolley option allowing for easier mobility and flexibility of use.
-
This can be particularly useful for organizations utilizing ViewScan at events where the system would temporarily need to be placed.
-
Along with the mobile trolley, add-on battery options are available for extra power when using it on-the-go.
IPVideo Corporation (Third of Four)

-
Best Back to Work Monitoring Solution
-
HALO SMART SENSOR 2.5
-
The HALO Smart Sensor is now helping facilities monitor their indoor health and air quality.
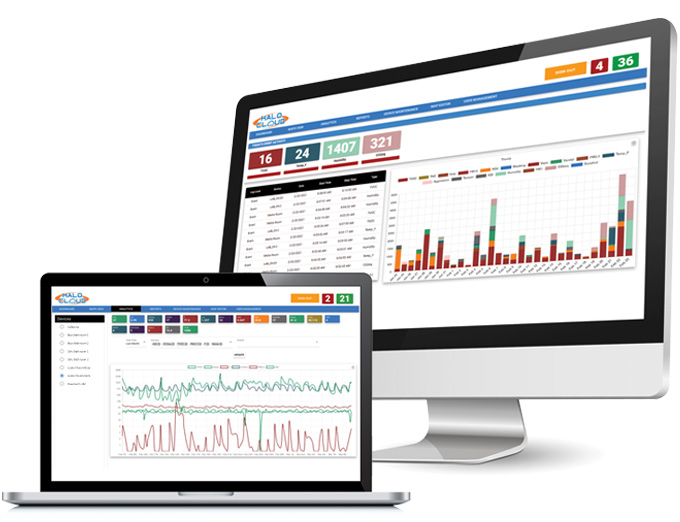
-
As part of the new v2.5 software release, HALO provides both a real-time air quality and Health Index and sends alerts when either index falls into danger zones.
-
Working with HALO Cloud, the sensor also provides critical automated reports that allow building owners and administrators to demonstrate they are providing a healthy indoor environment and/or validate when facility improvements are required.
IPVideo Corporation (Fourth of Four)

-
Best Metal/Weapons Detection Solution
-
ViewScan 2.0
-
ViewScan, the concealed weapons detection and loss prevention system, by IPVideo Corporation, is a passive weapons detection system that can accurately detect the location and number of objects hidden on a person, including those hidden in shoes and inside body, giving an exact pinpoint location of each object.
-
ViewScan significantly reduces the need for labor-intensive manual pat-downs and facilitates the rapid screening of individuals – while being completely safe.
-
ViewScan is an advanced and safe weapons detection and loss prevention system that does not emit radiation, making is safe for all including persons with medical devices or those who may be pregnant.
(See the ViewScan from IPVideo Corporation, a completely passive weapons detection system that emits no radiation and is safe for anyone to walk through. Courtesy of IPVideo Corporation and YouTube.)
-
*IPVideo Corporation was also recognized with Multiple Awards in the 2020, 2019, and 2018 ‘ASTORS’ Homeland Security Awards Programs.
Iris ID Systems
Best Facial/Iris Recognition System
-
iCAM D2000
-
The iCAM D2000 Multi Biometric System is the newest product from Iris ID that fuses iris and face recognition as the ultimate biometric solution.
-
The iCAM D2000 is compact and insightful, the result of twenty-plus years of research and development.
-
Unique features such as extended capture range from 50cm to 100 cm, anti-spoof measures, mask detection, and REST API build on the family of high-quality products that Iris ID already offers.
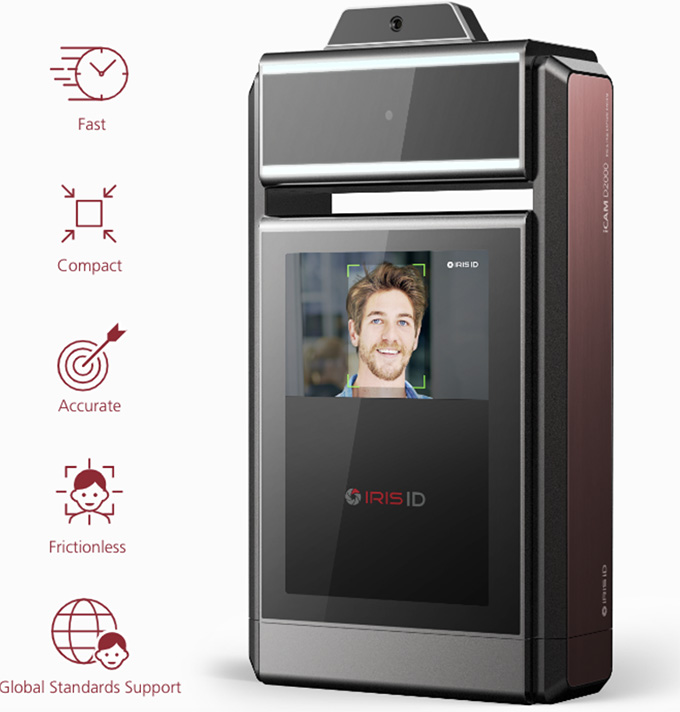
-
Additionally, the iCAM D2000 is a platform-independent solution, and application developers will find the REST API easy to implement.
-
With a focus on usability and dimensions, the iCAM D2000 is ideal for identity, travel, and access solutions and is applicable for border control, National ID programs, public security, e-Gates, and kiosk use.
-
Key features of note include multimodality biometric simultaneous capture, user height accommodation, a countermeasure for security, installation flexibility, and increased capture range, intuitive user guidance, mask detection, with standards-compliant hardware and software.
-
*Iris ID was also recognized with Platinum Award Wins in the 2020, 2019, 2018 and 2016 ‘ASTORS’ Awards Programs.
Konica Minolta Business Solutions
Best Image Technologies Solution
-
Dispatcher Suite
-
Business solutions are made easy with Dispatcher Suite which allows companies to effectively manage and reduce their printing costs, while increasing their document workflow productivity and security.

-
This feature-rich, integrated platform simplifies print and scan operations, maximizes office efficiencies, and provides businesses of all sizes with the flexibility they need.
-
The Dispatcher Suite platform combines two of Konica Minolta’s most powerful applications: Dispatcher Paragon for print management and our award-winning Dispatcher Phoenix for automated workflows, to provide a unified platform that allows customers to manage both their print and scan responsibilities simultaneously.
-
With Dispatcher Suite’s single sign-on capabilities and dynamic toolset, users have the ability to easily create powerful, automated document workflows for capturing, indexing, processing, and routing documents with zero manual effort.
(Look to Konica Minolta to get the job done better, faster, and more efficiently, with solutions to combine advanced bizhub printing and scanning features with integrated software functionality to streamline workflows in any industry. Courtesy of KonicaMinoltaUS and YouTube.)
-
*Konica Minolta Business Solutions was also recognized in the 2020 ‘ASTORS’ Awards, and with Multiple Awards in the 2019, 2018, and 2017 ‘ASTORS’ Homeland Security Awards Programs.
Lumina Analytics
Best Big Data Analytics Solution
Radiance Enterprise Search Platform
-
Lumina Analytics, a U.S.-based technology company that specializes in engineering cutting-edge solutions to the challenges of weeding through the world wide open-source web to identify critical risk information, to provide a proactive force for good.
-
RadianceSM, developed by Lumina, is a comprehensive enterprise search tool that uses Machine Learning (ML) and Artificial Intelligence (AI), which transforms publicly available data into timely, actionable intelligence, to help their clients anticipate, understand, manage and mitigate risk.
(See how Lumina Analytics provides intelligent solutions to help clients manage and mitigate risk. Serving large, regulated industries, law firms and governments globally with risk management intelligence, Lumina mines data from the open-source web to develop risk intelligence for large, regulated industries, and provides clients with unprecedented continuous, actionable prevention and mitigation opportunities. (Courtesy of Lumina Analytics and Vimeo.)
-
Lumina Analytics provides intelligent solutions to help clients manage and mitigate risk.
-
Lumina mines data from the open-source web to develop risk intelligence for large, regulated industries, and provides clients with unprecedented continuous, actionable prevention and mitigation opportunities.
Luminator Technology Group
Best COVID-19 Emergency Response Solution
-
Renew Air Treatment System
-
Luminator develops and delivers technology with tangible benefits that support transit bus and rail car manufacturers as well as public transit operators around the globe.
-
Luminator’s Renew™ Air Treatment system dispenses Grignard Pure, an antimicrobial air treatment through a connected, technologically advanced system that measures and automatically adjusts the amount of Grignard Pure that is dispensed in the air.
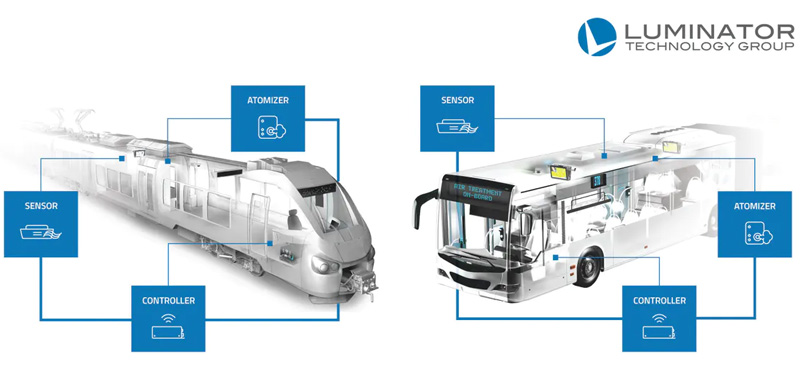
-
The adaptive system utilizes on-board sensors to automatically adjust the system based upon the fresh air intake and other conditions in the vehicle, maintaining proper concentration for efficacy – even with doors opening and closing as passengers embark and disembark the vehicle
-
As conditions change, such as fluctuations of fresh air intake throughout the route, the system maintains an effective level to continuously kill virus particles in the air.
-
Luminator Technology Group delivers globally-recognized technology solutions that increase intelligence, safety, and efficiency for public transit operations
(Grignard Company, a manufacturer of atmospheric effect solutions, and Luminator Technology Group (Luminator), a global leader in transit technology and communication solutions, announce a partnership focused on providing new safety offerings for public transit amid the ongoing coronavirus pandemic. Courtesy of Luminator Technology Group.)
Mark43

-
Best Public Safety Workforce Mgmt
-
Mark43 Product Suite
-
Mark43, a cloud-native public safety software company, offers a single-platform Computer-Aided Dispatch (CAD) and Records Management System (RMS) for seamless data entry and faster reporting that are a natural extension of the dispatcher, call taker, and in-field first responder during an emergency response.

-
Additionally, the Mark43 Product Suite includes Mark43 Analytics, which centralizes CAD and RMS data in real-time enables agencies to make informed, data-driven decisions.
-
Mark43 partners with over 120 public safety agencies of all sizes in the U.S. and abroad and uses its platform to support the demands of any mission.
-
By providing fast, powerful technology Mark43 enables first responders to focus on their most important work–keeping communities safe.
(See how Mark43 empowers communities and their governments with new technologies that improve the safety and quality of life for all. Mark43’s cloud-native public safety platform includes no-downtime updates, industry-leading functionality, and an uncompromising commitment to security and compliance. Courtesy of Mark43 and YouTube.)
-
*Mark43 was also recognized in the 2020, and 2019 ‘ASTORS’ Homeland Security Awards Programs.
Mercury Notifications

-
Best Mass Notification Solution – Hardware
-
n.FORM Mass Notification
-
Specializing in life-safety technologies, Mercury Notifications, and their n.FORM® Mass Notification System is a complete, end-to-end, supervised solution that provides the hardware, software, integration, and controls needed for mass notification and emergency communication systems.
-
No matter what the emergency, Mercury Notifications keeps the line of communication open, enabling targeted messages via distributed audio, wide-area speakers, phones, email, SMS/Text, Twitter, Skype/Teams, desktop alerts, digital signage, and more.
-
Additionally, Mercury’s n.FORM® meets the NFPA72 code and UL2572 standard-design requirements needed to be recognized as a true mass-notification system and provides the hardware and software that supports its distributed audio, distributed recipient mass-notification systems, fire-panel integration, and controls.
(Curious about how a mass notification system can reach everybody in the case of an emergency, this video will show you how we do it. Courtesy of Mercury Notifications and YouTube.)
Mission Secure
Best ICS/SCADA Cyber Solution
-
Mission Secure Platform
-
The Mission Secure Platform was built for one purpose, ICS/Industrial Control System (OT) cyber-protection.
-
Going beyond other available solutions with truly innovative capabilities integrated into one platform, the Mission Secure Platform is the first integrated cyber-protection platform for complete visibility, segmentation, protection, and patented signal-integrity monitoring.
-
The Mission Secure Platform protects OT networks from cybersecurity threats by providing unsurpassed visibility, segmentation, protection, and signal integrity.
(Mission Secure Inc. (MSi) is a leading Industrial Control System (ICS) cybersecurity company protecting clients in maritime, industrial, autonomous vehicles, smart cities and defense industries from cyber attacks. The patented MSi Platform is the only end-to-end ICS cybersecurity solution with visibility and protection down to Levels 0-1. Courtesy of Mission Secure and YouTube.)
N2WS Software
Best Cloud Computing/Storage Solution
-
N2WS Backup & Recovery
-
As more enterprises move to the cloud, data loss, outages, and malicious attacks become inevitable vulnerabilities. Scaling data and varying requirements become complex, as is the need to meet compliance regulations and optimize costs. This breeds an environment too complicated for manual scripts.
-
N2WS allows customers to ‘set it and forget it’, and effortlessly manage petabytes worth of data, recover quickly from attacks/outages/errors and manage storage costs, by leveraging N2WS’ secure, rapid data recovery and easy management for key services – all from a single console.
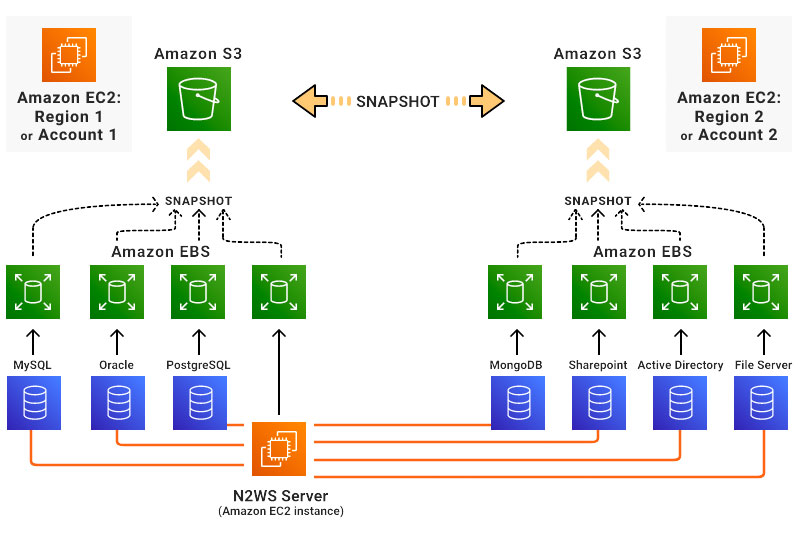
-
N2WS leverages AWS-native snapshot technology to fully automate backup of Amazon EC2, EBS, RDS, Redshift, Aurora, DynamoDB, EFS and S3. It has been the leading storage solution on the AWS Marketplace since 2012, providing very flexible backup scheduling and 1-click disaster recovery to restore a single file or entire environment in less than 30 seconds, across multiple regions and/or accounts.
-
N2WS Backup & Recovery has been dubbed the Next Generation Backup and Recovery for AWS due to its unique Disaster Recovery orchestration, data lifecycle management and cost savings capabilities. With N2WS, exponentially scaling data is now tantamount to managing complex backup schedules for thousands of AWS EC2 instances.
(N2WS optimizes RTO/RPO, supports multi-tenancy for large, complex environments and enables customers to lifecycle EBS snapshots into Amazon S3 and/or Glacier for long term retention. Courtesy of N2WS and YouTube.)
-
*N2WS was also recognized in the 2020, 2019 and 2018 ‘ASTORS’ Homeland Security Awards Programs.
nanoFIBER (Formerly Point 2 Point Communications)
Best Security Wire & Cable Solution (Tie**)
-
Armored Fiber Optic Cables
-
Airport information, security, video surveillance, alarms, fire suppression systems, and communication pathways fiber optics must pass through miles of overhead trays, countless wall conduits, and pathways as well as conduits carrying miles of cable between buildings, concourse terminals, and towers, and cannot afford downtime due to faulty cables due to vermin attacks, crimping, and breaking, etc.
-
They require the smallest outer diameter (OD) fiber optic jacket qualified to protect the inner fragile glass fiber optics that can be prone to cracking and breaking, while also being cognizant of future cabling requirements without the need to disturb existing cables.
-
nanoFIBER’s CPR Certified LSZH Stainless Steel Armored nanoFIBER fiber optic cables provide the safest and Secure armored cable solution in aviation the market today.
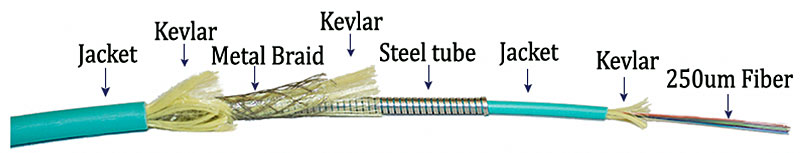
-
The nanoFIBER fiber optic cable provides aviation with a very small OD secure cable that is crush resistant, hard to cut through and safest for humans in a fire scenario.
-
The stainless-steel armored cable is impervious to harsh weather and ideal for indoor and outdoor environments, and when pulling nanoFIBER throughout aviation security and building management systems, the cable takes up minimal space and simplifies installation.
-
Additionally, nanoFIBER has the highest-level EU certification for low smoke zero halogen outer jacket that provides the best security to protect life in case of a fire at the airport or in a plane.
(nanoFIBER is a leader in the stainless steel armored fiber optic cabling structures for both patch cords and bulk usage. Courtesy of Steve Stark and YouTube.)
-
*nanoFIBER (Formerly Point 2 Point Communications) was also recognized in the 2020 ‘ASTORS’ Homeland Security Awards Program.
NEC Corporation of America
Best Integrated Security Mgmt System
-
NEC I:Delight
-
Star Alliance, one of the world’s largest airline alliance, connecting customers of prominent airlines like Lufthansa, United Airlines, and Air Canada, late last year launched Star Alliance Biometrics, powered by NEC technology’s NEC I:Delight identity platform software.

-
A service that benefits everyone from passengers to TSA agents, NEC’s I:Delight offers a contactless mechanism that ultimately makes the airport experience more hygienic, something we’re all grateful for as the fight against COVID-19 rages on.
-
Technology truly made for its time; the NEC face matching algorithm has proven its accuracy even with a face mask, as identity verification can occur in as little as 1.5 seconds .
-
Biometrics-powered security is the future of travel, one where passengers seamlessly navigate across a global network with a single secure digital ID.
(The world’s largest global airline alliance, Star Alliance, launched its new #biometrics service, Star Alliance Biometrics in November 2020. The identity management platform provides travelers with a seamless curb-to-gate, #touchless experience using NEC I:Delight. This technology enables travelers simply create a single #DigitalID to pass through the airport from check-in, bag drop, security checkpoints to boarding, and beyond. Courtesy of NEC Corporation of America.)
NEC Corporation of America
Best COVID-19 Detection Solution
-
NEC NeoFace Thermal Express
-
As the COVID-19 pandemic has stretched on through the year, airports have gone above and beyond to avoid becoming hotspots of virus contraction as people cross paths from across the globe.
-
Every state has taken a different approach to combat the deadly virus’s presence in travel hubs, the Hawaii Department of Transportation (HDOT) turned to the experts in AI-powered technology for safety and security, NEC Corporation.
-
The State of Hawaii has deployed NEC’s innovative NeoFace Thermal Express technology, at all five Hawaiian airports which automatically screens the body temperature of every arriving passenger entering the airport terminal, to ensure they do not become hotspots of virus contraction as people cross paths from across the globe.
(The Hawaii Department of Transportation (DoT) partners with NEC to install a hygienic, contactless thermal body temperature screening solution at Hawaii’s 5 major airports. The purpose of this project is to protect the health and safety of the traveling community, the visitors and the residents and to prevent the spread of COVID-19. Courtesy of NEC Corporation of America and YouTube.)
-
*NEC Corporation of America was also recognized in the 2018, and 2017 ‘ASTORS’ Homeland Security Awards Programs.
NEC National Security Systems
Best Federal Govt/DoD Access Control Mgmt
-
NeoFace, deployed by Leidos
-
NEC National Security Systems (NSS) provides full-service solutions for large agencies using the intellectual property and resources of the global NEC brand.

-
Redstone Arsenal, one of the most important military bases in the US (serving the DoD, DOJ, the NASA, and the likely future home of USSPACECOM, requires best-in-class security solutions, and with 44,000 employees and guests using the facility, it also requires solutions geared towards improving daily efficiency around the base.
-
In March 2021 Redstone began using a new NEC Face Recognition Algorithm (NeoFace) deployed by Leidos to verify all entries onto the base, while seated comfortably in their vehicles.
-
The NeoFace System minimizes time-consuming manual checks, and gives security personnel an added tool to verify identity with greater assurances.
(Redstone Arsenal is the only base in the country with this facial recognition technology. “We are the only post right now with facial recognition. So, we are leading the army in this part of the technology,” said Redstone Garrison Commander Col. Glenn Mellor. “…all Arsenal employees, members of the military, and retirees and their dependents who utilize a Defense Common Access Card for entry to the installation are automatically registered in the pilot programs database via hand-held scanners at the Gates. Once the initial scan is complete, the registered individual is clear to use the Facial Recognition lanes,” added Arsenal representatives. Courtesy of WZDX News and YouTube. Posted on Mar 12, 2021.)
NetAbstraction
-
Best Network Obfuscation Solution
-
NetAccess
-
NetAbstraction’s patented NetAccess technology protects online identity by isolating, disguising, anonymizing, and providing dynamic misattribution for Internet activities so that users can communicate on the Internet anywhere in the world securely and with non-traceable connectivity.
-
The lack of a traceable digital footprint protects user activity, presence, and their organization’s resources, including networks, applications, mobile devices, software and data. NetAbstraction provides security by obscurity: If hackers can’t find you they can’t attack you.

-
NetAbstraction augments the multi-layered security capabilities provided by the commercial cloud providers to include implementing dynamic security policies which help ensure that malicious traffic is not allowed to enter the network.
-
NetAbstraction is being used by Fortune 500 organizations in a wide array of industries, including Financial Services, Healthcare, Law Enforcement, Government Agencies, Professional Services, National Infrastructure providers, and more, to help with initiatives including providing secure, private networks, and disaster recovery, including fast backup network restoration.
-
The NetAbstraction network has been extensively red-teamed and approved for a range of offensive and defensive cyber operations, and is only available to organizations that are registered, validated, and initiated directly through NetAbstraction, Inc.
(Using patented technology developed and proven by leaders in the US intelligence community, NetAbstraction controls your information and obfuscates all of your cyber activity. Courtesy of NetAbstraction and YouTube.)
Netskope
-
Best Cyber End-to-End Encryption Solution
-
Netskope’s Security Cloud
-
Netskope safely and quickly connects users directly to the internet, any application, and their infrastructure from any device, on or off the network.
-
With CASB, SWG, and ZTNA built natively in a single platform, Netskope is fast everywhere, data-centric, and cloud smart, all while enabling good digital citizenship and providing a lower total-cost-of-ownership, with over 25% of Fortune 100 companies trust Netskope to deliver the SASE architecture digital transformation requires.
-
Netskope truly understands the cloud and takes a data-centric approach that empowers security teams with the right balance of protection and speed they need to secure their digital transformation journey.
-
Using patented technology called Netskope Cloud XD™, the Netskope Security Cloud eliminates blind spots by going deeper than any other security provider to quickly target and control activities across thousands of cloud (SaaS and IaaS) services and millions of websites.
-
Named by Gartner as the 2021 Gartner Peer Insights Customers’ Choice for both CASB and SWG, Netskope serves more than 1,500 worldwide customers, including over 30 companies of the Fortune 100.
(Hear from three industry experts, Enrique Salem, Former CEO of Symantec, John Thompson, Chair of the Board for Microsoft, and Mark Anderson, Former President of Palo Alto Networks, on why Netskope is exactly what companies need to secure their users and data. Courtesy of Netskope and YouTube.)
New Jersey City University
-
Best Cyber Security Education
-
BS in CyberSecurity
-
Center of Academic Excellence in Cybersecurity Defense is a multidisciplinary Center that supports New Jersey City University’s (NJCU) mission as an institution that provides its diverse population of students, faculty, and community with scholarship and pragmatic approaches to the field of Information Assurance.

-
Information Assurance is generally defined to include cyber security, cyber forensics, data quality, data completeness, data accuracy, privacy, and issues associated with the storage, communication, and sharing of data and information.
-
The Center involves faculty and students from across the University in teaching and learning, service projects, and research.
-
The Center aligns itself with faculty and students at other institutions such as Community and other four-year Colleges, with an overall mission to enhance the security and integrity of information within the geographical region, with future plans to extend nationally and beyond.
-
The Cybersecurity Program at NJCU takes a leadership role within information assurance and cyber defense by contributing to the Homeland Defense initiative.
-
*New Jersey City University was also recognized in the 2020 ‘ASTORS’ Awards, and NJCU Adjunct Professor Ewart Williams was honored in the 2019 ‘ASTORS’ Homeland Security Awards Program.
NICE Public Safety
-
Best 911 Recording & Analytics
-
E-Request
-
E-Request from NICE is a new cloud-based solution in the Evidencentral platform that supports timely disclosure of 911 audio evidence through automation.
-
As disclosure laws mandate stricter deadlines for reproducing and sharing 911 audio recordings and other evidence, agencies across the public safety and criminal justice continuum are struggling to keep up with requests using current manual processes.
-
E-Request digitally transforms how emergency communications centers (ECCs) receive and process 911 audio evidence requests and share incident information with district attorneys, police investigators, and other key stakeholders.
-
NICE’s e-Request works with NICE’s existing recording solution (NICE Inform) to address this challenge, by ensuring timely disclosure of 911 audio evidence through automation.
(Law enforcement leaders are under more pressure than ever coming from every possible direction demanding greater transparency – to questions and complaints over police response and incident handling. The key to getting answers to questions lies in getting control of your data. NICE Investigate brings all of your data together in one place so you can get operational insights and answers to questions fast. Courtesy of Nice Public Safety and YouTube.)
NICE Public Safety
-
Best Investigation/ Surveillance/Detection
-
NICE Investigate
-
Today, police departments have a “big data” problem, and crime solving hinges on digital evidence.
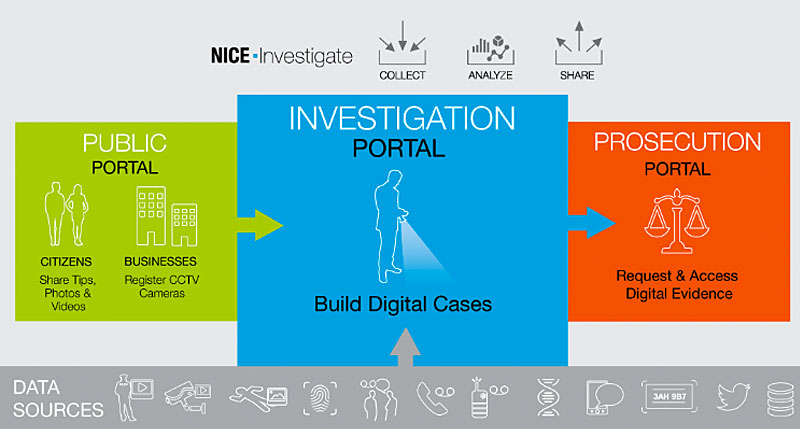
-
But there’s so much data coming from so many silos that it’s becoming increasingly difficult for investigators to ingest it, correlate it and absorb the relevant facts of a case.
-
The NICE Investigate Digital Investigation and Digital Evidence Management Software (DEMS) Solution which automates the entire digital investigation and evidence management process, helping investigators close more cases faster.
(Explore the challenges law enforcement investigators face every day, and the many ways that NICE Investigate, one of the solutions in the Evidencentral cloud-based, open, end-to-end digital transformation platform, can help. Courtesy of Nice Public Safety and YouTube.)
-
*NICE has now been recognized with Multiple Awards in all Six of in the Annual ‘ASTORS’ Homeland Security Awards.
OnSolve (First of Three)
-
Best Machine Learning & Artificial Intelligence (Tie**)
-
OnSolve Risk Intelligence
-
OnSolve offers a suite of AI-powered risk intelligence, critical communications, and incident management capabilities, so organizations can control the entire critical event management process, keep ahead of change, monitor disasters, and be empowered to make quicker, more accurate decisions during the times that matter most.
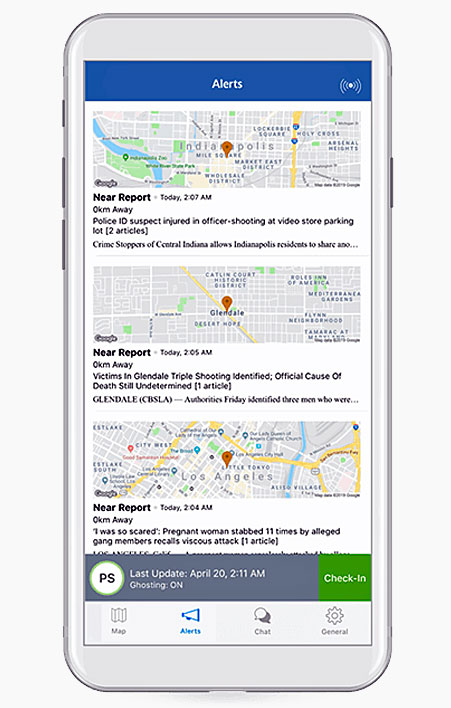
-
Organizations are able to gain risk intelligence information that allows them to prepare in advance for disasters and ensure business resiliency, send out mass alerts to notify the right people at the right time during a crisis, leverage a mobile incident management platform to retain full control during emergencies, and more.
-
Before, during, and after a critical event strikes, organizations now have the power of AI to inform timely and accurate situational awareness, the relevance and speed of leading mass notification services to manage critical communications, and the ability to holistically and seamlessly manage critical events through incident management – all from OnSolve.
-
OnSolve risk intelligence technology continues to keep people safe and informed, allowing them to better protect themselves, their employees and communities.
(There’s a fine line between critical event management and critical event mis-management. With speed, relevance, and usability, we give our customers what they need to successfully resolve crises — true actionable intelligence. The OnSolve Platform for Critical Event Management combines AI, machine learning, unmatched expertise and a modern platform to do what no one else can. We get the right information to the right people in the right way at the right time — when every minute counts™. Courtesy of OnSolve and YouTube.)
OnSolve (Second of Three)
-
Best Security Orchestration, Automation & Response
-
OnSolve Control Center
-
Gain 360-control of critical events. With Risk Intelligence, Critical Communications, and Incident Management capabilities unified in a comprehensive interface, you’ll have real-time critical event management.

-
Spot emerging threats early. With OnSolve’s AI-powered engine users can filter through all the noise and delivers accurate, actionable intelligence, so they can launch crisis workflows earlier.
-
Ensure the right information gets to the right people at the right time. With a common operating picture, clients can assess the impact and activate relevant teams for immediate resolution.
-
Third-party integration enables clients to manage risk without disrupting existing operations and infrastructure.
OnSolve (Third of Three)
-
Best Threat Intelligence Solution
-
OnSolve Risk Intelligence
-
Get Real-Time Visibility into Critical Events.
-
View actionable information on an intuitive dashboard, and easily visualize and filter critical event intelligence.
-
Dynamic maps of facilities, logistics, and personnel movements provide visibility into an event’s impact on your business or agency.
(If you are responsible for helping your organization respond to a crisis, OnSolve has the experience and capabilities to help you save time, money, and lives. We’re in the business of successful results, and we help you achieve them through the speed, relevance, and usability of our innovative OnSolve Platform for Critical Event Management. Courtesy of OnSolve and YouTube.)
-
*OnSolve was also recognized with Multiple Wins in the 2020, 2019 and 2018 ‘ASTORS’ Awards Programs.
PlateSmart Technologies
-
Best License Plate Recognition Solution
-
PlateSmart ARES 3.0
-
The all-new PlateSmart ARES 3.0 solution offers more than just license plate data, it’s a true vehicle intelligence solution.
-
Whether your objective is preventing crime or growing revenue, PlateSmart ARES 3.0 delivers actionable intelligence you can use.

-
In a nutshell, ARES 3.0 starts with ALPR, driven by cutting-edge AI and deep learning, and ends by delivering virtually unprecedented vehicle analytics.
-
Capture the license plate and jurisdiction as well as the vehicle make and color, and then use the software’s powerful analytical tools to make smarter decisions.
-
Even better, ARES 3.0 offers almost unlimited scalability, making it ideal whether monitoring three cameras or 3000.
-
The software integrates with top video management systems (VMS), and it’s capable of integrating with virtually any third-party software solution, offering customers enhanced functionality via ALPR.
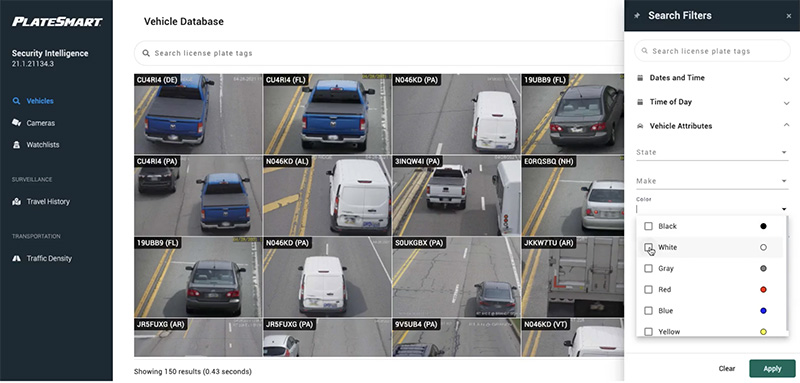
-
Fighting crime is a key application for PlateSmart ARES 3.0 software. That’s why it integrates seamlessly with NCIC and state Fusion Center databases, to help your local police solve more crimes and keep you safer by notifying them when a suspect vehicle arrives at your location.
-
*PlateSmart Technologies has now been recognized for their Sixth Consecutive Year in the Annual ‘ASTORS’ Homeland Security Awards.
Probable Cause Solutions
Best Surveillance Camera Tracking Software
-
Camera Canvass Tracker
-
Camera Canvass Tracker, a patented pending technology used to simplify canvassing for surveillance cameras, a task done by investigators every day.
-
Camera Canvass Tracker automatically builds a database of camera locations along with other pertinent information that allows the investigator to calculate time differences, record the DVR/cameras, view the database on a list or on a map, and export the database when needed.
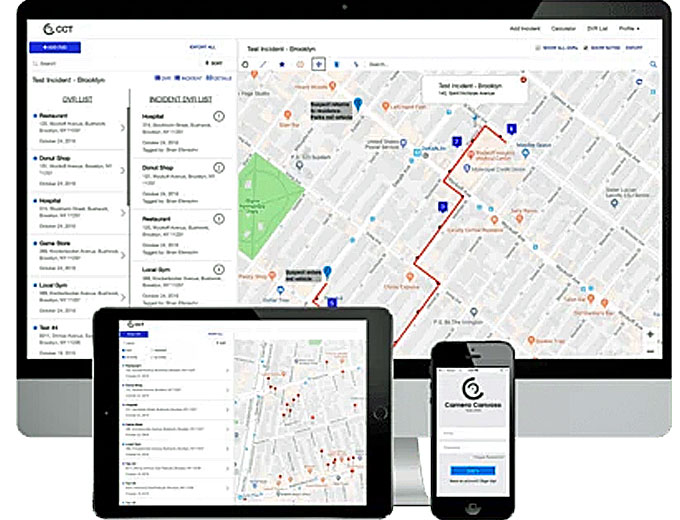
-
With Camera Canvass Tracker you can:
-
-
Map It – Create a centralized database of surveillance cameras within your jurisdiction. Search your database with our interactive geo-coded map.
-
Organize your Data – Store the name, address, and contact information for the custodians of the surveillance cameras. Save all DVR information for future reference.
-
Usable Data – Upload camera angle screenshots for future reference. Update the DVR data and add important notes for you and the rest of your agency to benefit from the next time you need it.
-
Calculate – Calculate those difficult time calculations down to the second. Saves valuable time and reduces the risk of human error. Creates a permanent record for future reference and strengthen testimony.
-
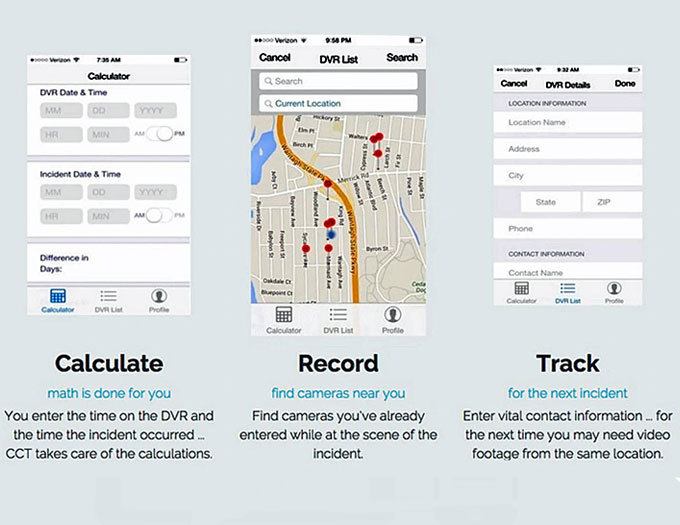
-
-
Incident Tracking & Custom Mapping – After creating your “Incident” Document the locations visited and create custom maps. Customize the map with a variety of pins and notes while plotting the course of travel.
-
Detailed Exports – Strengthen your case and testimony with proper documentation.
-
Group Plans – Share DVR data across your entire jurisdiction with everyone in your agency/group. Users can access the database from ANY internet-capable device, including their desktop computer.
-
-
*Probable Cause Solutions was also recognized in the 2020, 2019, 2018 and 2017 ‘ASTORS’ Homeland Security Awards Programs.
PRYME
-
Best Cyber Security Education
-
BTH-550-MAX & Drop-in Charger Bundle
-
The new BTH-550-MAX Wireless Speaker Microphone is the star of the revolutionary PRYMEMAX product suite, the world’s first crossover accessory solution that combines two-way radio and cellphone PoC operation in a single platform.

-
With rotary volume control and built-in wireless PTT, the BTH-550-MAX is completely universal, and with a new, more advanced chipset technology, one MAX speaker mic will work with virtually any two-way radio brand or PTT application to deliver exceptional performance.
-
Pryme created a BTH-550-MAX Bundle especially for first responders which includes a bonus Drop-in Desktop Charger, in addition to a wall charger and mini USB charging cable it already comes with.
-
The BTH-550-MAX is designed to be rugged and functional, with a waterproof front-facing speaker and dust/weather/rain resistance to IP56 levels, yet it’s small and lightweight with a 360° swivel clip and a 3.5 jack that fits a variety of headsets, from acoustic tube earphones to motorcycle helmet kits.
-
*Pryme was also recognized in the 2016 ‘ASTORS’ Homeland Security Awards Program.
PureTech Systems (First of Six)
-
Best Perimeter Protection Solution
-
PureActiv
-
PureTech Systems has been recognized with a record Six 2021 ‘ASTORS’ Awards for it’s PureActiv fully integrated automated outdoor wide-area and perimeter protection system.
-
PureActiv integrates with a vast array of short- and long-range perimeter sensors such as radar, buried or on-fence fiber detection systems, and ground sensors either singularly or in a combination to provide just the right level of protection to cost-effectively meet the most secure perimeter requirements.
And PureActiv delivers among the highest probability of detection with the lowest nuisance alarm rates for securing facilities, infrastructure, and borders.
(See a brief introduction to PureTech’s PureActiv automated outdoor wide-area and perimeter protection system in action. Courtesy of PureTech Systems and YouTube.)
PureTech Systems (Second of Six)
-
Best Long Range Surveillance Solution
-
PureActiv for Borders
-
Controlling national borders is an important part of a nation’s security, and the ability to effectively monitor vast areas in varied weather conditions and terrain, while accurately identifying potential threats at great distances is a complicated scenario.

-
The solution calls for knowledgeable personnel and accurate sensors that work together to quickly assess a situation and enable border agents to effectively intervene.
-
Ideal for Border Security, the PureActiv Automated Perimeter Intrusion Detection System enables detection, and classification of intruders up to 6 miles away.
-
Once PureActiv automatically identifies an intruder, the system has the ability to automatically track them and quickly provide accurate intruder location on a GIS map to the end-user.
(The MVSS platform utilizes PureTech Systems’ PureActiv software as its central command and control, providing AI enhanced video detection and classification, user interface display, and sensor collaboration logic for the surveillance suite. The suite consists of visible and thermal cameras, laser illuminators and range finders mounted on telescoping masts located in the back of commercial pickup trucks. Courtesy of Fox 5, PureTech Systems, and YouTube.)
PureTech Systems (Third of Six)
-
Best Maritime Perimeter Protection Solution
-
PureActiv
-
Our nation and the world depend on safe and efficient shipment of goods around the globe.
-
Threats to seaports and the resultant potential loss of lives and economic losses due to service interruptions make it imperative that seaports throughout the world are properly protected from terrorist and safety-related events.
-
PureTech’s PureActiv wide area and perimeter protection solutions help Port Authorities improve the safety and security of seaports with a tangible return on investment, and automates the protection of land and water-side perimeters to help ensure the safety and security of personnel and critical assets.
-
By detecting intrusion events at the perimeter before they result in more catastrophic events, loss of life, and operational downtime, port authorities, and law enforcement can intervene to deescalate situations and quickly return to normal operations.
-
The PureActiv system provides detection, alerting, and proactive deterring of potential safety and security events, which helps protect lives, cargo, and critical assets.
PureTech Systems (Fourth of Six)
-
Best Machine Learning & Artificial Intelligence
-
PureActiv
-
PureActiv AI Auto-verify Analytics eliminates 95% of nuisance alarms from radar, fence sensors, and motion video analytics.
-
With expertise from 16 years of real-world deployments and cutting-edge innovation, PureTech Systems patented Video Analytics are AI Deep Learning and Geospatially boosted and provide among the highest in probability of detection, and lowest in nuisance alarm rates for electronically securing perimeters around facilities, infrastructures, and borders.
(See how PureActiv’s deep-learning trained automated perimeter protection system includes intrusion detection, auto-verification, PTZ Auto-follow, and invoking non-lethal acoustic deterrents. Our enhanced capabilities detect, geolocate, classify and track intrusions, alerting only on verified threats ensuring near-zero nuisance alarms with market-leading detection rates. Courttesy of PureTech Systems and YouTube.)
PureTech Systems (Fifth of Six)
-
Best Video Analytics Solution
-
PureActiv
-
Key benefits of PureActiv AI Deep Learning Geospatial Video Analytics include:
-
Automatically detects, classifies, geolocates, tracks and alarms only on Objects of Interest.
-
Technology backed up by 13 patents and over 16 years of innovation and field training data.
-
-
-
Lower total cost of ownership when considering infrastructure cost and maintenance,
-
Effective in the most challenging of outdoor conditions.
-
Uses Convolutional, Neural Network Deep Learning, and Geo-spatial data for high fidelity classification.
-
Longest detection ranges in the industry (over 5 miles)- requires fewer cameras.
-
Higher accuracy – Industry-leading Probability of Detection and low Nuisance Alarm Rate.
-
Simplified configurations support rapid deployment.
-
Image Stabilization.
-
-
-
Autonomous PTZ camera lock-on-target tracking enhances situational awareness.
-
Object geo-location on map enhances situational awareness.
-
Combines with other detection sensors (radar, fence, ground, etc.) for most demanding applications such as nuclear power plants.
-
-
-
Seamless integration with market-leading VMS systems including Genetec, Milestone, PureActiv AlertView, and others.
-
Easily scales to fit your needs today and tomorrow.
-
Camera agnostic- deploys on edge devices and/or servers.
-
PureTech Systems (Sixth of Six)
-
Best Mobile Tech Solution
-
PureActiv Rapid Deploy Virtual Perimeter
-
Scalable to small and large perimeters, the new Rapid Deploy Virtual Perimeter Unit (RDVPU) provides a temporary or permanent virtual perimeter protection system that requires very little deployment time.

-
The smart and effective protection system uses a wireless connection to transmit alarms and video to a co-located or remote command and control center and is enhanced with the use of radar, a pan-tilt-zoom (PTZ) camera, and optional loud hailers and light deterrents.
-
The RDVPU is equipped with PureTech’s patented AI and geospatially boosted video analytics, PureActiv, which provides among the highest probability of detection while maintaining near-zero nuisance alarms.
-
Additionally, the RDVPU is solar-powered, needing little to no backup fuel, thus providing an environmentally friendly protection system that does not require ground penetration and has no impact on local wildlife.
(Click Image above to view a Rapid Deploy Virtual Perimeter Unit Deployment in Action. Courtesy of PureTech Systems.)
-
*PureTech Systems was recognized with Multiple Awards Wins in the 2020 ‘ASTORS’ Homeland Security Awards Program, and also won a Platinum ‘ASTORS’ Award in the 2018 ‘ASTORS’ Awards Program.
Quantum Corporation (First of Two)
-
Best Video Data Storage Solution
-
Pivot3 Surety
-
Organizations are finding themselves overwhelmed by managing and monitoring all the various servers and appliances in use for video recording, video analytics, access control, intrusion detection, and other physical security applications, especially in environments with multiple distributed locations, but also in large, centralized environments.

-
The time it takes to gather all the right information to ensure all the servers and appliances are healthy, performing optimally, and up to date takes them away from other more critical tasks, yet a problem with just one of those servers can put their entire organization at risk.
-
Pivot3 Surety, which was recently acquired by Quantum Corporation, unifies the management and monitoring of both Pivot3 servers and appliances along with non-Pivot3 servers, and provides visibility and management of key information through a single-pane-of-glass management console, saving clients time and ensuring their security applications are running at their peak performance and efficiency.
Quantum Corporation (Second of Two)
-
Best Video Data Storage Solution
-
VS-HCI Series Edge
-
The Quantum VS-HCI Series is purpose-built for supporting video management systems (VMS), video storage, and video analytics plus enabling the consolidation of other related applications such as access control onto an integrated server and storage platform called hyperconverged infrastructure (HCI).
-
The Quantum VS-HCI Series uses innovative software-based intelligence and automation to simplify management, provide the highest levels of resilience and efficiency, and ensure scaling and maintenance are easy. With solutions optimized for edge and centralized environments as well as security operations centers, and support for any VMS and video analytics, the VS-HCI Series can cover all your video capture, storage, and visualization needs.
(See how Quantum provides organizations with the software and services to manage and enrich data, including the most complex unstructured data and video files, and when enriched, data delivers the insights clients need to drive your business forward—faster than ever before. Courtesy of Quantum Corporation and YouTube.)
-
*Quantum Corporation was also recognized in the 2018, and 2017 ‘ASTORS’ Awards Programs, and Pivot3 was recognized in the 2020, 2018, and the 2016 ‘ASTORS’ Homeland Security Awards Programs, respectively.
Rajant

-
Best Wireless Video Surveillance Network
-
Rajant BreadCrumb Hawk
-
The Rajant Hawk is a high-performance, dual-radio industrial-grade, wireless Kinetic Mesh BreadCrumb.

-
Infused with Rajant’s patented InstaMesh protocol, the Hawk offers higher throughput with enhanced security performance using 256QAM, 80 MHz channels, and hardware acceleration.
-
The Hawk is reliable in extreme environmental conditions and has several mounting options, and contains two transceivers delivering MIMO operation over multiple frequencies for reliable and resilient connections.
-
The platform combines high-speed, highly flexible mobile connectivity to reliably power new applications at the edge with unlimited coverage through a Layer-2 multi-radio mesh fabric extended across the deployment.
(Introducing the Hawk, one of Rajant’s newest industrial-grade high-performance BreadCrumb platforms that offer dual MIMO transceivers, up to 1.7Gbps aggregated data rate, higher throughput, and enhanced security performance. Courtesy of Rajant and YouTube.)
-
*Rajant was also recognized in the 2020 ‘ASTORS’ Awards Program.
RangeForce

-
Best Cyber Security Training Platform
-
RangeForce Cybersecurity Training
-
RangeForce helps organizations achieve cyber resiliency by providing a metrics-driven platform that assesses strengths and weaknesses and trains and cross-trains staff so they can confidently address cyber threats with expertise, both individually and as a well-oiled team.

-
RangeForce has developed the industry’s first integrated cybersecurity training platform and virtual cyber range that uses real IT infrastructure, tools, and malware.
-
RangeForce cybersecurity training is 100% cloud-based and can be performed remotely via web browser/login, which changes the old paradigm of traditional, time-consuming, and expensive classroom-based cyber training.
-
Enterprises can now operationalize a SaaS-based cybersecurity training program in hours, which saves them up to 65% over traditional training and up to $1M annually on hosted cyber ranges.
(RangeForce makes creating highly skilled cybersecurity defenders simple, flexible, and fast for all enterprises. Powered by the industry’s first SaaS-based, integrated cybersecurity simulation and virtual cyber range, we help customers operationalize a security training program in hours, saving up to 65% over traditional training and up to $1M annually on hosted cyber ranges. Courtesy of RangeForce and YouTube.)
Rave Mobile Safety (First of Two)

-
Best COVID-19 Communications Solution
-
Rave Coronavirus Recovery Solution
-
As public safety and first responders continue to struggle with the implications of COVID-19, it is more crucial than ever that they are able to proactively identify, communicate with and respond to those at greatest risk.
-
Of equal importance is ensuring the protection of first responders to COVID-19 exposure, and in order to provide better safety and communication capabilities to organizations across all industries, Rave Mobile Safety developed its Coronavirus Recovery Solution, to enable these organizations and agencies to adhere to national and local guidelines while creating a safe environment for their staff and community.
-
Two key applications include Critical Communications for timely, targeted, and personal notifications to employees and members within an organization; and Mass Notifications across 9-1-1, first responders, and emergency management to protect public safety through natural disasters, operational events, and crisis incidents.
(Learn what to look for in a critical communications platform and how it can help your agency improve response efforts during your coronavirus recovery efforts. Courtesy of Rave Mobile Safety and YouTube.)
Rave Mobile Safety (Second of Two)

-
Best Risk, Crisis Mgmt Solution
-
Rave Collaborate
-
It’s challenging to have paper-based checklists sitting in a folder or notes on a personal mobile phone when lifesaving decisions and actions must be made.
-
Teams need to be prepared for all possible events and make strategic decisions quickly during those initial critical moments of an incident as first responders arrive on scene.
-
Rave Collaborate ensures all key resources can be easily found and implemented when the unimaginable occurs.
-
Staff can quickly see what needs to be done, make appropriate response decisions, and account for their actions.
(See how you can Mitigate Operational Disruptions, and initiate communication during major events, from severe weather to facility closures, power outages and road closures to operational issues that impact your supply chain, infrastructure and IT. Courtesy of Rave Mobile Safety.)
-
*Rave Mobile Safety was also recognized with Multiple Award Wins in the 2020, 2019, 2018 and 2017 ‘ASTORS’ Homeland Security Awards Programs.
Regroup Mass Notification

-
Best Risk, Crisis Mgmt Solution
-
Regroup Mass Notification
-
Regroup Mass Notification® empowers better mass communication to keep people safe and informed during critical and daily events and is used every day by thousands of organizations to save lives, improve safety for entire communities, respond to potential hazards, prepare for emergencies, and more.
-
Regroup’s easy-to-use system enables administrators to send thousands of notifications per minute, rapidly alerting large groups of recipients to danger. Administrators can also expand their reach by distributing messages via websites, PA systems, digital signage, and more.
-
Whether used for critical or routine communications, Regroup Mass Notification helps organizations across America communicate quickly to improve homeland security, strengthen operational resilience, mitigate risk, and thrive in an increasingly unpredictable world.
-
Regroup Mass Notification is dedicated to making continuous service improvements, towards making our nation more resilient and secure, and especially during the current pandemic that is still impacting so many American communities and businesses.
(See why Regroup’s award-winning platform is a top choice for emergency and day-to-day notifications for universities, hospitals, corporations, and venues across North America and worldwide. Courtesy of Regroup Mass Notification and YouTube.)
-
*Regroup Mass Notification was also recognized in the 2020, 2019, 2018, and 2017 ‘ASTORS’ Homeland Security Awards Programs.
Remee Wire & Cable

-
Best Security Wire & Cable Solution
-
Warehouse Access Control Cabling
-
Remee Wire & Cable is being recognized for a project involving a Warehouse Access Control Security Cabling Installation for a large online retailer with hundreds of distribution centers around the globe.

-
A retailer has strong security software platforms and related hardware to operate their very efficient security system however, with an average of 30-50 access-controlled doors per warehouse and the mandatory 3-5 cables needed per door, plus other devices, there were roughly 200-250 cables to run to the various security system panels.
-
Mistakes were made, and over time wires became mixed, mislabeled, confused, and terminated to the wrong control panels for a variety of reasons, which slowed down the commissioning of the warehouse’s access control doors.
-
Security designer Acenes, working alongside Remee successfully aggregated all 5 component cables under single, color-coded jackets, reducing the average number of cables pulled from 250 to just 50 – an 80% reduction in the number of individual cable pulls, which lowered the overall installation cost.
-
This project began in 2021, and its immediate success resulted in this solution becoming the worldwide standard for the global retailer, to be installed in the hundreds of warehouse facilities worldwide.
Robotics Assistance Devices (First of Two)

-
Best Motion Detection Solution
-
ROSA180
-
ROSA180 is a supplemental security device that includes critical autonomous response capabilities to help simulate security personnel actions at a fraction of the cost.
-
-
The device’s 180° field of view through dual hi-resolution, full-color, always-on digital cameras provide 24/7 visibility and monitoring.
-
ROSA180 can also be used to recognize and deter loitering, and the device’s built-in continually active analytics can activate security alerts to onsite security or law enforcement, as defined by the end-users particular needs.
(See an illustration of ROSA180, a proven perimeter surveillance superstar for Robotic Assistance Devices (RAD), with its human and vehicle detection analytics and keen ability to detect and deter trespassers, loiterers and vagrants. Courtesy of Robotic Assistance Devices and YouTube.)
Robotics Assistance Devices (Second of Two)

-
Best Robotic Perimeter Protection
-
ROSA180
-
ROSA180 comes equipped with RAD’s AI-driven security systems including both human and vehicle detection, license plate recognition, and complete integration with the RAD Software suite notification and response library.

-
Additionally, ROSA180 has stood out as a proven perimeter surveillance superstar with its keen ability to detect and deter trespassers, loiterers, and vagrants, as well as enforce COVID-19 mask requirements in a non-confrontational manner.
-
ROSA180 houses dual cameras with a combined 180° Field of View that drive its internal AI-analytics to detect any unexpected movement (human or vehicle) then initiate any number of autonomous responses both visual and audible.
-
The system also opens direct video and audio communication to remote monitoring personal who are able to view and speak with any detected persons.
-
ROSA180 is a game-changer in the security services industry, allowing a very cost-effective force multiplier in nearly every environment.
-
*Robotic Assistance Devices was also recognized with Multiple Award Wins in the 2018, and 2017 ‘ASTORS’ Homeland Security Awards Programs.
SafeGuard Cyber

-
Best Cyber Security Risk Mgmt Solution
-
SafeGuard Cyber Platform
-
Business today thrives in the cloud. Connections, collaborations, trials, and transactions all happen in the cloud, and while the cloud provides unprecedented convenience and computing, it also brings unquestionable risk.
-
When people do business outside of the IT infrastructure, they lose the power to keep connections and data safe, and social engineering threats, ransomware, compliance gaps, and unprotected sensitive information are just some of the risks plaguing businesses that remain unseen and unaddressed by current security protocols for cloud-based applications.
-
SafeGuard Cyber protects the human connections businesses need to thrive in a digital world, by securing business-critical communications, detecting and stopping cyber threats, and ensuring compliance in real-time without disruption to natural workflows.
-
In 2020 alone over a trillion dollars was lost to insider threats, data breaches, and ransomware attacks. And while some businesses struggle to protect themselves from bad actors, others in regulated industries like banking and pharmaceutical deal with the significant compliance hurdles that come hand-in-hand with a digital sales force.
-
Whether somebody is a CISO charged with securing their entire organization, or a Chief Compliance Officer responsible for adhering to strict industry regulations, SafeGuard Cyber provides security and governance and compliance for business-critical digital communications of an entire enterprise and its workforce.
(SafeGuard Cyber is a pioneer in Communication Security. Learn how the platform works to keep your business secure and compliant while permitting the adoption of modern collaboration and communication cloud applications. Save money, reduce risk, enable growth, and above all SafeGuard Human Connections. Courtesy of SafeGuard Cyber and YouTube.)
SafeLogic

-
Best Encryption Solution
-
CryptoComply
-
CryptoComply has quickly become a preferred encryption module deployed by technology vendors into the Public Sector.
-
By combining cryptographic technology with FIPS 140-2 validation expertise, SafeLogic has perfected a drop-in crypto bundle for regulated industries.
-
Vendors develop their products around the CryptoComply core, focusing on what they do best, while the SafeLogic team ensures FIPS 140-2 validation, the benchmark certification for encryption in the federal government.
-
The validation (administered by NIST) is delivered in less than 8 weeks, a huge competitive advantage for clients who are facing rivals in procurement RFPs as well as any pursuing additional compliance initiatives like FedRAMP, Common Criteria, DoDIN/UC APL, or the upcoming CMMC.
(See how SafeLogic simplifies and accelerates the FIPS 140-2 validation process. Courtesy of SafeLogic and YouTube.)
-
*SafeLogic was also recognized in the 2020, 2019, and 2018 ‘ASTORS’ Homeland Security Awardss Program.
Securiti

-
Best Data Security, Privacy, Governance & Compliance
-
Securiti Platform
-
Organizations are collecting petabytes of sensitive data regulated by GDPR, CCPA, CPRA, PCI DSS, HIPAA, and more, which is distributed across hundreds of assets, often impossible to find, let alone protect.
-
Securiti has innovated AI-driven Sensitive Data Intelligence (SDI), which automates data privacy and protection to make compliance with privacy regulations faster and cheaper while reducing the risk of sensitive data leaks.
-
By combining data security and privacy on a single platform, Securiti eliminates blind spots and the need for redundant, siloed tools, and is capable of real-time, integrated data privacy and security management across complex enterprise environments that include on-premise, cloud, multi-cloud, Saas applications, in structured and unstructured data stores.
-
With more than 200 native data connectors, Securiti SDI integrates easily into existing environments to identify and protect high-risk data, wherever it resides, and help customers ensure strong data security, privacy and governance as they pursue modernization, cloud data migration, digital transformation, and privacy by design.
Select Engineering Services (First of Two)

-
Best Personal/ Protective Equipment Product
-
Automatic Injury Detection (AID) System
-
The Automatic Injury Detection (AID) system provides help in seconds when the sensing panel has been pierced by a bullet, knife or shrapnel.

-
When an AID flexible mylar sensor panels (front & back, comfortably inserted into the wearer’s bulletproof vest) is pierced by either a bullet, knife or shrapnel from an IED, the communications module will sense the break in the circuit and automatically sends an emergency alert with GPS location to phone, radio or communication system.
-
The automated and instant emergency alerts help save lives by improving the response from medics and backup personnel to stop, apprehend or contain the attacker, even when the officer is incapacitated.
Select Engineering Services (Second of Two)
-
Best Alert Notification System
-
Personal Emergency Transmitter (PET)
-
The Personal Emergency Transmitter (PET), is a wearable device that automatically sends alert text messages, with your personal info and a link to your GPS location in the event of an emergency.
-
The PET system provides a covert method to summon help when you are faced with a dangerous situation and it’s impossible to call help without alerting your attacker (i.e. reaching for your cell phone).
-
The PET system allows you to avoid escalating a potentially dangerous confrontation and have backup on the way in seconds.
-
*Select Engineering Services was also recognized with Multiple Award Wins in the 2020, 2019, 2018, and 2017 ‘ASTORS’ Homeland Security Awards Programs.
Senstar

-
Best IP Video Surveillance Solution
-
Symphony Common Operating Platform
-
The Senstar Symphony™ Common Operating Platform with sensor fusion is a modular solution for security management and data intelligence.
-
In addition to being an open, highly scalable video management system with built-in video analytics, it includes full-featured access control and perimeter intrusion detection modules.
-
But what truly sets Senstar Symphony apart is its sensor fusion engine. By intelligently combining low-level sensor data with video analytics, the sensor fusion engine achieves the highest levels of performance, far beyond that of the individual devices.
-
Senstar Symphony seamlessly incorporates sensor fusion, event algorithms, and rule-based actions to provide unmatched capabilities, flexibility, and performance.
(Central to Senstar’s vision of unifying security and operations is Senstar Symphony, Senstar’s video, security and information management platform. Courtesy of Senstar and YouTube.)
-
*Senstar was also recognized with Multiple Award Wins in the 2019, and 2018 ‘ASTORS’ Homeland Security Awards Programs.
Seoul Robotics

-
Best Machine Learning & Artificial Intelligence
-
SENSR for Security
-
Seoul Robotics, a 3D computer vision company building a perception platform that uses AI and deep learning to power the future of mobility, robotics and smart cities, has introduced the SENSR™ for Security.
-
SENSR™ for Security is the first-of-its-kind deep learning software application able to create flexible, scalable 3D data solutions for the security market.
-
The first non-proprietary 3D software application on the market, SENSR for Security is compatible with more than 75 different brands and models of sensors, making it highly versatile, additionally, a single solution can even comprise a variety of different sensors from multiple manufacturers within one system, a first for the industry.
-
The SENSR™ for Security solution is powered by Seoul Robotics’ proprietary deep learning software platform and works in tandem with 3D data collected by LiDAR sensors.
(See how SENSR can keep track of more than 500 people or objects within a location at a given time as well as total the number who have come and gone. Courtesy of Seoul Robotics and YouTube.)
ShotSpotter (First of Two)

-
Best Public Safety Workforce Mgmt
-
ShotSpotter Connect
-
ShotSpotter® Connect™ is AI-driven software that helps law enforcement deter crime by pro-actively directing patrol resources to specific locations that have the highest likelihood of crime that day.

Research shows that high visibility patrols are an effective deterrent to crime. Agencies receive precise locations to patrol based on AI that is superior to traditional hot spot analysis.
-
Connect develops risk assessments for future crimes by collecting and analyzing three sources of data: historical crime data from a police jurisdiction; public data such as weather, transportation points, locations of parks, schools, and liquor establishments; and exclusive ShotSpotter gunfire data.
-
Machine learning determines the areas of highest risk and the forecasts are turned into data-driven patrol plans by shift and beat every day, and disseminated electronically to officers in the field, and carefully meters out recommended time spent on a directed patrol, suggests tactics by crime type, and automatically randomizes patrol locations to minimize the possibility of over or under policing any area.
-
ShotSpotter Connect has been proven to reduce crime by 33%, measured over a period of 90 days in one part of a district where patrol officers use the software and compared to crime levels where officers in a neighboring part of the district do not use the software.
(See a brief overview of ShotSpotter Connect – a Community First Patrol Management Software that dynamically direct patrol resources to areas of greatest risk, more effectively deter crime, and serve the community. Courtesy of ShotSpotter and YouTube.)
ShotSpotter (Second of Two)

-
Best Gunshot Detection Solution
-
ShotSpotter Respond
-
Gun violence in America’s cities is a devastating epidemic, which has killed more than 65,000 individuals and injured several hundred thousand in just the last five years, and yet 88% of gunfire incidents are never reported to police.
-
-
ShotSpotter’s real-time alerts notify police precisely when and where gunshot incidents occur, within 60 seconds, with critical data such as number of rounds fired, number of shooters, and type of weapons used.
-
This results in a faster, more accurate response to the scene to better recover evidence, interview witnesses, and attend to gunshot victims—improving overall police effectiveness.
-
By working with ShotSpotter, law enforcement agencies can better connect with their communities and bolster their mission to protect and serve.
(Learn how law enforcement agencies can proactively address gun violence and build community trust with ShotSpotter Gunshot Detection. Courtesy of ShotSpotter and YouTube.)
-
*ShotSpotter was also recognized in the 2020, 2019 and 2018 ‘ASTORS’ Awards Programs.
Simeio

-
Best Identification Mgmt Solution
-
Simeio Identity as a Service
-
Employees, partners, and customers require secure, role-appropriate access, and they need it now, not tomorrow.
-
That’s why Simeio’s team of identity professionals, powered by the company’s Identity Orchestrator platform and Identity Intelligence Center, have the required expertise to provide a comprehensive IAM solution, and can even integrate with and manage clients’ existing IAM system(s).
-
If a client needs it, Simeio can provide all the benefits of a dedicated team of security and identity professionals without the overhead.
-
Their hosted IAM solutions eliminate the large, up-front capital investments required for IAM infrastructure, shifting costs to pay-as-you-go operating expenses.
-
Simeio eliminates clients’ complexity and replaces it with consistent and reliable identity services and a single point of contact for operations and support, backed by their stringent service level agreements.
(Is your organization saddled with aging identity and access management infrastructure? IAM has grown increasingly complex and costly to maintain. So see what Simeio’s Identity as a Service can do for your organization. Courtesy of Simeoio and YouTube.)
-
*Simeio was also recognized in the 2020, 2019 and 2018 ‘ASTORS’ Awards Programs.
SIMS Software

-
Best Security Workforce Mgmt Platform
-
SIMS
-
SIMS Software is widely recognized as the industry leader in security information management systems, to the government and defense industries with a track record spanning nearly four decades.

-
SIMS flagship product, Security Information Management System (SIMS) manages visitors, classified contracts, classified information tracking, and control, as well as personnel security clearance processing and monitoring at all levels, including Top Secret and Sensitive Compartmented Information (SCI) requirements.
-
The company was founded by a Navy Veteran in 1983 and remains the pre-eminent industrial security information management tool for the Defense Industrial Base and extensive high-profile government agencies however, the relevance of the companies capabilities doesn’t end in the DoD world.
-
In today’s modern threatscape, holistic security goes beyond protecting the perimeter fence and preventing break-ins or triggering alarm bells, it’s about locking down the lifeblood of our organizations.
-
It is critical to know who controls and has access to highly sensitive data and where it resides, particularly during the COVID-19 era with a dispersed workforce in many cases working remotely.
-
As such, our security toolsets must evolve, as has SIMS. For example, Insider Threat has become a widely used buzzword, but how do you define what it means?
-
Being able to report, review, track trends over time and analyze individuals for questionable and repeated abnormal behavior patterns is paramount.
And it is just as important to be able to share that data across the proper functional representatives inside your organization that can roll up into a Dashboard to present statistics in real-time, all at your fingertips for proper investigation and decisioning.
-
SIMS provides all the features and functionality necessary to run a powerful, paperless industrial security program with a single system of record, so clients are able to escape the development costs and interoperability issues associated with in-house solutions.

-
*American Security Today (AST) is delighted to welcome New Premier Awards Sponsor SIMS Software to the 2021 ‘ASTORS’ Homeland Security Awards Program.
Singlewire Software (First of Four)

-
Best IT Disaster Preparedness & Recovery Solution
InformaCast Command Center
-
To help organizations prepare for and manage disasters, Singlewire Software has added InformaCast Command Center to its InformaCast Mobile and InformaCast Fusion offerings.
-
Command Center helps organizations prepare for disasters by giving them the opportunity to identify the disasters that will have the most impact on their operations, whether it be an active shooter, chemical spill, severe weather, medical emergency, or any other disaster they are likely to encounter.
-
Each identified event can be assigned a button with customizable text, colors, and graphics to make it as easy to identify as possible.
-
The buttons will appear in the InformaCast web console or within the InformaCast Mobile app so no matter where someone is they can trigger a notification the moment they see an incident occur.
(Quickly send notifications in the event of an emergency with InformaCast Command Center. Build icons on the homepage for crisis scenarios such as fires, severe weather, medical emergencies, active shooter, and more. Courtesy of Singlwire Software and YouTube.)
Singlewire Software (Second of Four)

-
Best Mass Notification Solution – Application
-
InformaCast Fusion with Zoom Phone
-
InformaCast Fusion with Zoom Phone from Singlewire Software gives the 1 million people utilizing Zoom Phone the ability to leverage the mass notification power of InformaCast Fusion for security and communication.

-
In an emergency, every moment matters, and organizations need communication systems that reach all their people quickly, and the faster a message goes out, the more time security personnel have to respond to and manage the situation at hand.
-
Using InformaCast Fusion, Zoom Phone users can now trigger mass notifications that reach all of their people.
-
InformaCast Fusion with Zoom Phone can be used to enhance security with emergency alerts in enterprise businesses, healthcare, manufacturing, K12, higher education, and other industries that need assistance reaching all of their people quickly during a crisis.
-
Organizations can use it to activate lockdowns, share details about approaching severe weather and send alerts about active shooter situations, as well as other emergency scenarios they are likely to face.
Singlewire Software (Third of Four)

-
Best Mobile Technology Solution
-
InformaCast Mobile
-
InformaCast Mobile is a cloud-based mobile app that offers organizations an easy way to reach all of their people on their mobile devices with mass notifications.
-
InformaCast Mobile users can launch notifications directly from their mobile devices. With the InformaCast Command Center feature, organizations can pre-build buttons for common emergency scenarios to quickly access notifications and provide detailed information, like the location of the incident or a description of an intruder.
-
Flexible message templates mean organizations can create notifications for any kind of situation they are likely to encounter, from active shooters and severe weather to network outages and medical events.
-
Messages can be sent in multiple formats including SMS text messages, push notifications, emails, and audio messages. The more formats used the more likely it is that someone sees the message quickly and takes appropriate action.
-
InformaCast Mobile also offers geofencing capabilities to alert everyone within a certain area and even trigger alerts when particular users enter or leave a designated location.
(InformaCast Mobile mass notification software is a great solution for navigating reopening and a return from the coronavirus pandemic shut down. Courtesy of Singlwire Software and YouTube.)
Singlewire Software (Fourth of Four)

-
Best COVID-19 Communications Solution
-
InformaCast Fusion
-
At the onset of the COVID-19 pandemic one of the biggest challenges was sharing information with workers.
-
As companies closed and local and federal guidelines shifted, organizations without solid communication tools suffered and put people at risk as unorganized responses led to confusion, downtime, and in severe cases the exposure to the disease.
-
The mass notification capabilities of InformaCast Fusion from Singlewire Software helped organizations stay in touch with employees to keep them up to date about health and safety guidelines as well as operational changes caused by the pandemic.

-
With the ability to reach on-premises and mobile devices from a single system, organizations could still reach all of their people whether facilities were open or closed, using text, audio, and visual cues to send messages to desk phones, IP speakers, desktop computers, mobile devices, digital signage and more.
-
With a wide variety of channels being used, people see messages quickly and take action. During an event like the pandemic, this is critical when trying to maintain business continuity.
(InformaCast mass notification software by Singlewire Software is a comprehensive emergency mass communication solution. InformaCast allows its users to leverage on-site devices to IP phones, monitors, overhead paging systems, panic buttons, and others to reach on-premises employees, while also leveraging mobile devices, Microsoft Teams and Cisco Webex Teams to remote workers. InformaCast has 3 different services levels, Fusion, Advanced and mobile to send emergency notifications, communicate promptly with employees and guests as well as create bell schedules and automated weather alerting. Courtesy of Singlwire Software and YouTube.)
-
*Singlewire Software was also recognized with Multiple Awards in the 2020 ‘ASTORS’ Awards, as well as Awards in the 2019, and 2018 ‘ASTORS’ Homeland Security Awards Program.
Siren Operated Sensors (SOS)
-
Best Fire & Safety System
-
-
SOS Silent
-
SOS Silent Emergency Gate Access Systems are the fastest way for emergency vehicles to gain access to gated facilities, campuses, and residential communities.
-
-
-
This pure and simple system allows responders to focus on driving and on the emergency ahead without pushing a remote, looking up a code, stopping to use a key, or changing the channel on their radio to trigger the gate.

-
Using RFID the SOS Silent System will open gates quickly, silently, and automatically when emergency response vehicles come within range of the gate and can be adjusted from 10 to 600 feet to customize each gate entrance.
-
The SOS Silent also has a backup entry system to open with the “YELP” siren.
-
SOS Silent ensures first responders can get to community members in need with no life-threatening delays. No stopping, no getting out of the vehicle, no codes to remember, no remotes to push, no keys to lose, and no cost to the municipalities.
-
*Siren Operated Systems has now been recognized for Five Consecutive Years in the Annual ‘ASTORS’ Homeland Security Awards Programs.
SolarWinds Worldwide (First of Three)
-
Best Security Incident & Event Mgmt (SIEM)
-
Threats to IT networks continue to accelerate and evolve and while enterprising hackers from external sources test the robustness of network security parameters, internal threats in the form of careless and malicious insiders remain a major and ongoing concern.
-
It is critical that agencies take steps to combat these threats—and SolarWinds® Security Event Manager (SEM), formerly Log & Event Manager is a powerful weapon. This comprehensive SIEM solution delivers dynamic, real-time log collection and analysis for immediate and actionable threat intelligence.
(See a brief, high-level overview of the capabilities of SolarWinds Security Event Manager and how you can use the SIEM tool to detect threats, quickly respond to cyber incidents, and report compliance from a consolidated interface. Courtesy of Solarwinds Worldwide and YouTube.)
-
SEM can capture and analyze log data in real-time from multiple sources and specific incidents, allowing users to quickly identify and remediate threats, uncover policy violations, and resolve vital network issues, and users can quickly shut down breached systems, block IP addresses, kill unexpected processes, and disable user accounts.
-
SEM includes an easy-to-use, point-and-click interface and data visualization tools to quickly search log data, perform event forensics, and identify the cause of security incidents or network problems.
-
Like all SolarWinds software, SEM is built to scale and can support IT environments of all sizes, and employs a node-based license model that allows users to stay within their planned budgets as they deploy and expand their IT infrastructures across multiple data centers and geographies.
-
SolarWinds SEM is used by nearly every U.S. federal civilian agency, DoD branch, and intelligence agency. It is available on the U.S. General Services Administration (GSA) Schedule and other contract vehicles.
SolarWinds Worldwide (Second of Three)
-
Best Network Security Solution
-
Successful threat mitigation requires continuous real-time monitoring of network configuration changes and potential policy violations, and alerts for automated detection and remediation of harmful security violations is essential.
-
SolarWinds® Network Configuration Manager (NCM) offers compliance auditing and leverages baselines and differential viewers to help ensure that devices are configured correctly, with an automated change control workflow, bulk configuration updates, and automatic vulnerability assessments to help teams efficiently identify and fix vulnerabilities – all in a single solution.
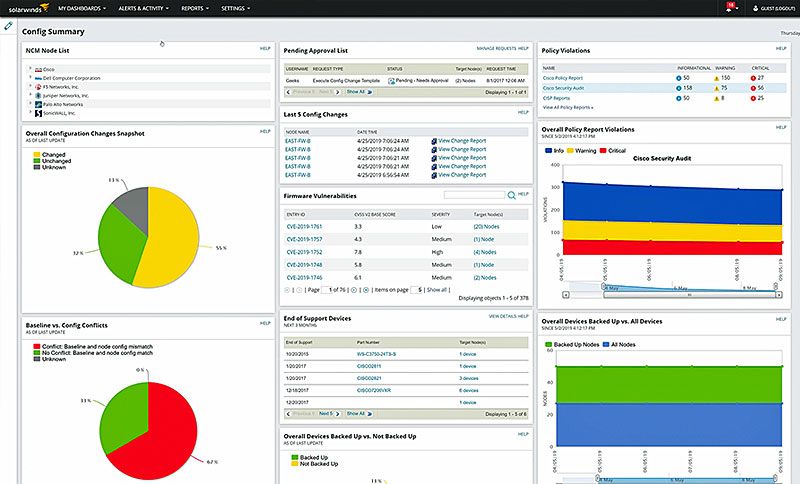
-
NCM offers several unique and powerful features to help agency IT professionals protect against vulnerabilities and prevent unauthorized network configuration changes, and uses Cisco® IOS® and ASA vulnerability scanning and NIST FISMA, DISA STIGs, and DSS PCI compliance assessments to improve network security.
-
The software itself features hundreds of built-in compliance reports to help meet major auditing authority requirements, including DISA STIGs, NIST FISMA, and more, and THWACK®, SolarWinds’ online user community, provides a number of free report templates that can be used to prepare for an inspection.
-
NCM is built for IT environments of all sizes and can easily scale to meet growing infrastructure needs. Licensing depends on the total number of devices an IT pro manages, including firewalls, routers, switches, or any other device that supports remote access and a command line interface.
(Increase visibility to your network devices with SolarWinds® Network Configuration Manager. Save time and improve network reliability by automating network configuration and change management to reduce configuration errors, recover quickly from downtime, and improve security and compliance. Courtesy of SolarWinds and YouTube.)
SolarWinds Worldwide (Third of Three)

-
Best IT Access Control & Authentication System
-
SolarWinds Access Rights Manager (ARM) is designed to assist IT and security admins to understand and act on high-risk access and minimize the impact of insider threats.

SolarWinds® Access Rights Manager (ARM) is designed to deliver customized Active Directory (AD) and Azure AD reports—showing who has access to what, and when they accessed this data.
-
SolarWinds ARM enhances security by monitoring, analyzing, and auditing Active Directory®, Azure AD, Exchange™, SharePoint, OneDrive, and file servers to see what changes have been made, by whom, and when those changes occurred, and customized reports can be generated to demonstrate compliance with most regulatory requirements.
-
The solution also provisions and deprovisions users using role-specific templates to help assure conformity of access privilege delegation in alignment with security policies.
-
ARM helps prevent data leaks and unauthorized changes to sensitive files and data through visualization of permissions on file servers.
-
SolarWinds ARM reduces IT workload through a web-based self-service portal, put access rights of data in the hands of data owners instead of admins.
(SolarWinds Access Rights Manager (ARM) helps IT and Security Admins meet compliance requirements with centralized provisioning, de-provisioning, management, and audit of user permissions and access to systems, data, and files while protecting their organizations from internal security breaches. Courtesy of SolarWinds and YouTube.)
-
*SolarWinds has now been recognized with Multiple Awards in all Six Annual ‘ASTORS’ Awards Programs.
Stellar Cyber

-
Best Cyber Analytics Solution
-
National Security requires scanning every potential ingress point for cyberattacks. Networks are the prime vector for cyberattacks, and network security focuses on spotting those attacks. Stellar Cyber addresses the challenge that network security is broken because it creates too many alerts and alert fatigue.
-
The good thing about network security (network detection and response, or NDR) tools is that they capture evidence of attacks from the true source – the network that connects everything, including servers, endpoints, users and the cloud.
-
The bad thing is that most network security tools create a torrent of alerts, leaving security analysts overwhelmed with alerts and spending all of their time chasing them down instead of responding to real security exploits.
-
Stellar Cyber’s Open XDR platform distills related alerts into contextual incidents so analysts can move quickly to responding to remediating real attacks.
-
Stellar Cyber’s platform was the first Open XDR platform – that is, it collects data from other, existing security tools (including NDR tools), or customers can deploy Stellar Cyber’s patented sensors that extract the relevant security data at ingestion, minimizing storage costs.
-
Stellar Cyber’s platform then normalizes their data for ingestion by its AI engine, and automatically correlates that data to spot breaches that might go unnoticed in security systems that require manual correlation of data from multiple consoles.
(See how Stellar Cyber’s Open-XDR Platform solves the tool, data, and people challenges in the security industry today. Courtesy of Stellar Cyber and YouTube.)
Strata Identity

-
Best Cloud Identity Orchestration Solution
-
Maverics Identity Orchestration Platform
-
The cloud has created an identity management crisis, with companies being forced to simultaneously manage on-premises and several different cloud provider systems to enforce security policies.
-
Strata’s Maverics Identity Orchestration Platform™ creates an identity control plane that enables customers to enforce a global access policy at scale across multiple distributed clouds and on-premises systems.
-
It is not another Single-Sign-On (SSO), directory, or authentication solution, it is the first distributed, standards-based identity orchestration solution that automates multi-cloud and hybrid cloud identity management, and represents a brand new approach to distributed identity management.
-
Maverics eliminates the need for companies to replace their existing identity systems or rewrite apps in order to make them compatible with new identity systems, which avoids years of integration and migration time and costs.
-
Strata’s ‘migration factory’ approach enables organizations to “lift-and-shift” apps, whether it’s one or one thousand (or more), quickly to the Cloud.
-
By design, Maverics connects to any identity system, transparently migrates users and credentials, replicates and synchronizes policies and configurations, and abstracts authentication and session management.
(With Strata’s Maverics Identity Orchestrator™, enterprise identity management is simplified as you can migrate and modernize your identity systems without painful application rewrites. You’ll save hundreds of hours, and millions of dollars on your upcoming project. Courtesy of Strata Identity and YouTube.)
StrikeReady

-
Best Threat Intelligence Solution
-
StrikeReady
-
StrikeReady addresses both cyber security skill gaps & the talent shortage via an AI-driven virtual assistant – CARA (Cyber Awareness and Response Assistant).

-
CARA assists defenders to reason and respond to threats using institutional knowledge, and accelerates the SOC to be leaner, efficient and mature.
-
CARA was designed to not only assist, but also empower cybersecurity teams that are overburdened with an endless tally of incidents, alerts, and an ever-changing threat landscape.
-
It can join any team – SOC, Incident Response, Threat Intel, Security Engineering, Red Team, Security Operations, and more — and offer expert assistance.
-
With CARA, defenders can quickly respond to incidents, proactively defend against emerging threats, or operate at lightning speed as they continue to perform any security operations-centric task.
Teledyne FLIR
Best CBRNE Detection Solution
-
identiFINDER R700
-
The Teledyne FLIR identiFINDER R700, introduced in June 2021, is a Backpack Radiation Detector (BRD) that fills a need in the operational deployment of radiation detectors.

-
The R700 builds upon years of tried and true spectroscopic algorithms applied to a man-portable backpack detection system for accurate and reliable results.
-
The R700’s lightweight, flexible and portable design allows users to configure the system as either an unmarked backpack or a stationary device, enabling mission sets from wide-area searches to temporary checkpoints.
-
With its nondescript backpack form-factor and phone-based user interface, operators detect radiological threats covertly, even in a crowd.
-
The identiFINDER R700 which is a recent recipient of a U.S. government award, provides the capabilities required to successfully perform wide-area searches quickly and efficiently while offering exceptional sensitivity, communication, and trusted spectroscopic algorithms in a lightweight, ergonomic form-factor.
(The FLIR identiFINDER R700 Backpack Radiation Detector (BRD) offers new spectroscopic broad-search capabilities. Once dismounted, the identiFINDER R700 provides the capabilities required to successfully perform wide-area searches quickly and efficiently while offering exceptional sensitivity, communication, and trusted spectroscopic algorithms in a lightweight, ergonomic form-factor. Courtesy of Teledyne FLIR and YouTube.)
-
*FLIR Systems has now been recognized in all Six Consecutive Years of the Annual ‘ASTORS’ Homeland Security Awards.
TiniFiber
-
Best Security Wire & Cable Solution (Tie**)
-
TiniFiber
-
TiniFiber is a breakthrough innovation in fiber optic cabling that delivers some of the smallest, strongest, and most flexible armored fiber optic cable on the market to meet aviation cabling project requirements in the tightest congested airport pathways.
-
TiniFiber® protects the fragile fiber optic glass within the cable jacket with a U.S. Patented Micro Armor Fiber™ cable which has a similar outer diameter (OD) of a standard fiber cable but 75% smaller and 65% lighter than the aluminum interlock armor (AIA).
For example, a typical AIA 12 strand armored cable can cause many challenges for airport installation and maintenance, including a minimal bend radius which when stressed, can crack the glass within the cable.
Additionally, AIA is heavy to handle, requires multiple technicians to roll out, and requires large reels to ship to sites, which takes up mission-critical space within the pathways.
12 Strand Fiber Optic Armor Competitive Analysis – Based on 1000 Feet:
-
*Tinifiber was also recognized in the 2019, and 2018 ‘ASTORS’ Homeland Security Award.
True Security Design
-
Best Law Enforcement Training Solution
-
Remote & On Demand Police Training Subscription
-
In 2021 True Security Design released Remote Live Training and an On-Demand Police Training Subscription services to address Budget, Social Distancing and Scheduling Issues Departments are Facing.

-
These remote services enable police agencies to train their staff around any of the covid lockdown and social distancing guidelines.
-
With the subscriptions entire police agencies are addressing budget cuts by training entire staffs for the cost of a single officer training, stretching scarce training dollars and provides training to every officer in an agency regardless of size for the same price.
-
With the On-Demand service police officers can take the training at any time overcoming scheduling obstacles they commonly face and benefit the individual officer their agency and the communities they serve.
(Addressing the entire officer, the mind, the body, and the spirit of your people is not just a good idea, it should be the focus, and this on-demand police training subscription does exactly that. Courtesy of True Security Design and YouTube.)
-
*True Security Design was also recognized in the 2019, and 2018 ‘ASTORS’ Awards Program, and Lt. Joseph Pangaro, the President and CEO of True Security Design, was recognized in the 2020 ‘ASTORS’ Awards Program.
TrueFort
-
Best App & Cloud Workload Protection Solution
-
TrueFort Fortress
-
Applications are the lifeblood of a business – regardless of how or where they’re delivered and accessed. Yet, while enterprises spend millions on new solutions, breaches and exfiltration continue to rise in frequency, profile, and impact
-
TrueFort has developed an innovative, application-centric approach that overcomes the security blind spots inherent in traditional application security tools to provide unparalleled visibility and protection for modern application environments.
-
TrueFort Fortress was designed specifically for the complex, dynamic nature of modern application workloads that span multi-cloud, hybrid, and data centers, applying deep, continuous analytics and machine intelligence to identify threats, align and apply controls in real-time, and adapt at machine speed to application and architecture changes, all while minimizing false positives.
-
TrueFort Fortress greatly reduces business risk by supporting zero or lean trust application environments that protect themselves, and the platform’s patented automation and intelligence monitors, alerts and responds to threats in real-time and establishes a trust profile for every application.

Next-gen application & workload protection. Adaptive trust technology gives your applications the power to protect themselves intelligently and in real-time across your entire application landscape.
-
TrueFort Fortress detects and prevents advanced persistent threats (APTs), insider threats, account compromise, and more.
-
Application security teams use Fortress to achieve unparalleled security visibility to inform and improve their security strategy and architecture decisions.
-
Identity governance teams use Fortress for visibility into all of the software service account identities being used, as well as the usage patterns.
-
For threat hunters, TrueFort Fortress provides out-of-the-box searching and querying capabilities against application contextual data that significantly reduces the typical setup time required to begin threat hunting.
-
For audit and compliance, Fortress provides the visibility and controls necessary to satisfy regulatory, industry, and corporate compliance policies.
-
(Hear from Sameer Malhotra, CEO & Founder of TrueFort, as he describes application challenges and how TrueFort can reduce clients’ security attack surface with application risk posture. Courtesy of TrueFort and YouTube.)
TruU
-
Best IT Access Control & Authentication System
-
TruU Platform
-
Still Using Passwords? TruU’s Passwordless Multi-Factor Authentication (MFA) can do better.
-
80% of breaches start with compromised credentials
-
$2.1 Trillion Global cost of data breaches in FY 2019
-
-5% Drop in stock price the day a breach is announced
-
-
TruU offers a Passwordless Workforce Identity Management Solution designed to use a unique combination of self-sovereign biometrics and behavioral biometrics, to create the most frictionless access user experience for physical resources and computing systems.
-
Enjoy complete and robust passwordless authentication for your entire workforce and eliminate the possibility of phished or stolen passwords with TruU.
-
Integrate into major enterprise identity stores and IT infrastructure and ensure compatibility with your environment.
Valor Systems
-
Best IT Access Control & Authentication System
-
Valor Incident Mgmt System
-
The Valor Incident Management System (Valor IMS), is an integrated suite of modern computer programs designed to automate and enhance the flow of critical information amongst communications operators, the response units in the field, support units, and the public.

-
Valor IMS serves emergency response and records management needs of government, corporate security, and university safety/security organizations, with an interactive situational awareness incident management platform to complement synergistic operations among all stakeholders.
-
Valor Systems Integrated Public Safety
and Security Software Platform offers CAD, RMS, Mobile, and citizen reporting applications that can work independently and/or collectively in concert as one unified platform based on a client’s budget, operational needs, and installation timeframe, with systems that can be installed locally on a customer’s computer network or accessed as a Software as a Service (SaaS) hosted on CJIS compliant, secured “cloud” network.
Versa Networks

-
Best Network Security Solution (Tie**)
-
Versa SASE (Software as a Service) is an industry-first solution that delivers leading Secure SD-WAN services and private connectivity for employees who are remote or working from home, so they can securely connect to applications in both private and public cloud services.
-
This new solution is based on the Versa Operating System (VOS™), a comprehensive and advanced next-generation virtual appliance that powers Secure SD-WAN networks on-premises and in the cloud for thousands of customers globally.
-
To protect the enterprise, which now has an expanded threat perimeter with the majority of connections being remote, Versa SASE offers the industry’s widest range of security functions in a Secure SD-WAN solution, which includes stateful firewall, DOS protection, next-generation firewalls, IPS, and URL filtering on end users’ client devices connecting privately to company resources hosted in private data centers, the public cloud, and Software as a service (SaaS) locations.
(Available via the cloud, on-premises, or as a blended combination of both, Versa SASE connects Work-from-Home users to Enterprise branches securely and reliably to applications in the cloud or data centers around the world. Courtesy of Versa Networks and YouTube.)
West Virginia American Access Control Systems

-
Best Integrated Security Mgmt System
-
The West Virginia American Access Control Systems (AACS) Series 400 makes security easy.

-
Designed to easily replace existing swing doors without additional construction, the AACS Series 400 is a fully customizable, ADA compliant security portal solution, trusted to meet the high-security needs of America’s most secure facilities for years.
-
Additionally, the AACS Series 400 portal now outfitted with Temperature Scanning capabilities automatically scans the user’s body temperature, and if the temperature exceeds the threshold the user is denied access to the building.
-
WVAACS security portals are 100% Made in the USA with US components.
-
*WVAACS was also recognized in the 2020, 2019, and 2018 ‘ASTORS’ Homeland Security Awards Programs.
WireSecure
-
Best Identification Mgmt Solution
-
WireSecure
-
While cyberattacks are a constant threat, impersonation remains one of the most prolific forms of fraud.

-
In the US alone, billions of dollars of fraudulent losses have been incurred by participants in M&A and real estate transactions, customers of financial institutions, investors, and other high-value targets.
-
WireSecure offers a new approach to identity management and authentication for wire transactions that applies AI and biometrics to make wire transactions more secure – while doing it in the context of how people work.
-
Frictionless and innovative, WireSecure digital ID credentials combine best-in-class facial recognition technology with government-issued ID and financial information to create an irrefutable form of identification.
-
In essence, WireSecure creates secure communities – where identities have been validated and accounts are verified, so that exchanges can be conducted in a secure manner.
(See how to create secure, verified communities to prevent fraud, provide confidentiality, and automate financial transactions. Courtesy of WireSecure and Vimeo.)
Yubico

-
Best Cyber Security Solution
-
The YubiKey 5 FIPS Series is the industry’s first set of multi-protocol security keys with support for FIDO2 and WebAuthn, along with smart card (PIV/CAC), to receive FIPS 140-2 validation, Overall Level 1 and Level 2, which enables government agencies and regulated industries to meet the highest authenticator assurance level 3 (AAL3) requirements from the new NIST SP800-63B guidance.

-
The addition of the YubiKey 5 NFC, YubiKey 5C NFC, and YubiKey 5Ci into the FIPS series lineup significantly expands coverage for mobile-first environments that many organizations have been waiting for.
-
The YubiKey 5 FIPS Series hardware authenticator, offers one-touch strong authentication, does not require a battery or network connectivity, and reduces password support incidents by 92% to dramatically lower IT support cost.
-
This combination of desktop and mobile functionality allows U.S. government agencies and contractors, as well as other highly-regulated entities, to modernize their existing authentication framework and achieve phishing-resistant passwordless authentication for all users.
(See how easy it is to set up the YubiKey 5 FIPS Series YubiKey in just 4 easy steps to protect your online accounts, and you’ll be on your way to a safer online experience. Courtesy of Yubico and YouTube.)
-
*Yubico was also recognized in the 2020, 2019, and 2018 ‘ASTORS’ Homeland Security Awards Programs, respectively.
** In the rare event of a Tie in the Annual ‘ASORS’ Awards Program, this result occurs based on overall differing goals and technology applications of the products or services, or overall similarities of the products.
AST is Proud to Introduce the 2021 ‘ASTORS’ Excellence and Government Awards
Thomas Richardson
-
Excellence in Public Safety
-
-
FDNY Chief of Department
-
Chief Richardson is a 40-year veteran and true servant leader who served tirelessly as a Battalion Chief in the aftermath of 9/11 – after having lost 343 of his colleagues, Chief Richardson never sounding retreat or surrender to those who tried to harm our Country.
-
-
Richard Blatus
-
Excellence in Public Safety
-
-
FDNY Assistant Chief of Operations
-
Assistant Chief of Operations Blatus, also a 40-year Department veteran who also served as a Battalion Chief in the aftermath of 9/11 attacks, Chief Blatus continues to lead, to inspire, and to mentor firefighters.
-
-
James Albrecht
-
Excellence in Public Safety
-
A retired NYPD Captain, First Responder, and Incident Command Management Member at the World Trade Center on September 11, 2001, and many other major events across New York City.
-
Captain Albrecht is also a Retired Police Chief who served as the Chief of Criminal Investigations for the United Nations and European Union police agencies in Kosovo, and is presently a Professor of Criminal Justice and Homeland Security at Pace University in New York City.
Derrick Driscoll
-
Excellence in Homeland Security
-
-
United States Marshals Service Deputy Director COO & Chief Risk Officer (Ret)
-
-
-
Deputy Director Driscoll is a 27-year veteran of federal law enforcement recognized for his relentless and global pursuit of criminals and criminal organizations.
-
Derrick now uses that same drive to build strategic alliances in the private sector, serving as the Principle of Strategic Alliances for Peraton’s Civil & Health sector, where he leads the sector’s federal government strategy and engagement.
(Derrick Driscoll, United States Marshals Service. Courtesy of WMAR-2 News and YouTube.)
Frank Larkin
-
Excellence in Public Safety
-
In honor of Mr. Larkin’s career service to our Nation as a United States Secret Service Special Agent and First Responder to the World Trade Center; as a Navy SEAL and extraordinary leader who now leads a global effort to recognize early signs of TBI in our service members to prevent generations of grief to families and to society in the absence of these future leaders. His efforts result from the loss of his son Ryan, a Navy SEAL to suicide following repeated undiagnosed percussive injuries.
(Listen to surviving dad Frank Larkin share lessons learned on the lookback in an effort to save lives in honor of his son, Ryan. At TAPS they say that “postvention is a critical component of any comprehensive suicide prevention strategy.” Learn about suicide risks and protective factors as well as our field-leading TAPS Suicide Postvention Model at https://www.taps.org/suicide. Courtesy of Tragedy Assistance Program for Survivors and YouTube. Posted on Oct 8, 2020.)
John Merrill
-
Excellence in Homeland Security
-
-
Deputy Director, Technology Centers Division (Acting) at U.S. Department of Homeland Security
-
-
(Learn More about how the DHS Science and Technology Directorate (S&)T is mobilizing innovation to secure our world. From sensors to cybersecurity to technology for first responders, we work with you to find tomorrow’s solutions, today. Courtesy of DHS Science and Technology Directorate.)
Kevin Becker, PsyD, LCP
-
Excellence in Scientific Research
-
-
Trauma Counselor, and Owner of ORI Consulting
-
-
-
In recognition of Dr. Becker’s lifetime of service as a practitioner and as a psychologist helping individuals, organizations, and governments prepare for, respond to, and recover from crisis and traumatic events, and the human impact of trauma, crisis, and disaster for organizations and individuals.
(Hear Dr. Kevin Becker, keynote speaker at Newtown Sandy Hook Community Connections Day posted on Jul 10, 2017. Courtesy of ORI Consulting and YouTube.)
National Center for Disaster Medicine and Public Health (NCDMPH)
-
Excellence in Public Safety
-
Trauma is the leading cause of death for young Americans, and there have been calls to teach children about hemorrhage control however little was known about adolescents’ ability to perform hemorrhage control, and the ideal way(s) to teach them.
-
The origins of FAST were developed using battlefield lessons-learned, evidence-based research, and student, medical, and educational expert input, and with the experience of Dr. Craig Goolsby, Professor & Vice Chair, Dept of Military & Emergency Medicine; Science Director, NCDMPH at Uniformed Services University, who has an extensive background in emergency medicine, medical education, combat casualty care, first aid, mass casualty, and disaster medicine.
-
The evidence-based nature of FAST was successfully documented through focus groups and educational research (with both high school students and teachers), which led to the development of the three training modalities to include live-actor videos featuring high school students.
-
Excellence in Public Safety
-
FAST is a school-age training initiative offered in multiple modalities, designed to enhance a bystander’s ability to take decisive, lifesaving action to assist victims with traumatic injuries.
-
FAST training provides the knowledge necessary to stabilize the injured and control severe bleeding in the minutes until first responders arrive on scene.
(The FAST education program is based on funding provided by the Department of Homeland Security (DHS) Science and Technology Directorate (S&T) to the National Center for Disaster Medicine and Public Health (NCDMPH). The FAST course and digital materials, developed by the American Red Cross in collaboration with NCDMPH, will be offered at no charge to high school students under the age of 19, thanks to the S&T grant. Courtesy of the DHS Science and Technology Directorate and YouTube.)
DHS Science & Technology (First of Four)
-
Excellence in Public Safety
-
The DHS Science and Technology Directorate (S&T) awarded a grant to the National Center for Disaster Medicine and Public Health (NCDMPH) to develop the school-age trauma training that became First Aid for Severe Trauma (FAST).
-
FAST is the first national STOP THE BLEED® course designed specifically for high school students and made available through the American Red Cross, thanks to the S&T grant.
-
While FAST is available for anyone, the course and digital materials are offered at no charge to high school students under the age of 19.
DHS Science & Technology (Second of Four)
-
Excellence in Public Safety
-
-
Wildland Fire Sensor Technology
-
The Wildland fires present a significant threat to the United States, and the DHS Science and Technology Directorate (S&T) is fighting fire with technology.
-
Wildland Fire Sensor Technology could provide the public with the advanced notice necessary to reduce the loss of life and property while giving communities the information and time necessary to make life-saving evacuations.
-
-
(Learn More, courtesy of the DHS Science and Technology Directorate and YouTube.)
DHS Science & Technology (Third of Four)
- Excellence in Homeland Security
-
In the event of a radiological or nuclear incident, emergency response agencies and HAZMAT teams could utilize this new technology to set up community reception centers to screen members of the public for potential exposure to radioactive contaminants.

-
Two inventors from the DHS National Urban Security Technology Laboratory (NUSTL) have developed a personal radiation detector (PRD) that could be placed beneath an entry ramp to detect radioactivity on the shoes of people being pre-screened before entering main screening areas.
-
This innovative and unique new device emits an alarm sound that is both louder than, and distinctive from other alarms, to ensure it can be easily heard and distinguished from other devices.
-
Additionally, the remote alarm box does not require any batteries nor external power and can be stored indefinitely without maintenance so that it is immediately ready for use in an emergency.
DHS Science & Technology (Fourth of Four)
-
Excellence in Homeland Security
-
DHS S&T identifies research the agency will conduct to understand the opportunities, as well as the risks, that accompany the rapidly changing AI/ML technology landscape and its impacts to DHS missions, and incorporate the technological advancements in AI/ML to enhance the efficiency and effectiveness of the DHS operational components and the broader Homeland Security enterprise.

-
S&T’s three strategic goals are to 1) drive next-generation AI/ML technologies for cross-cutting homeland security capabilities; 2) facilitate the use of proven AI/ML capabilities in homeland security missions; and 3) build an interdisciplinary AI/ML-trained workforce.
-
The Strategic Plan aligns with the DHS Artificial Intelligence Strategy, which lays out goals to govern the Department’s approach to integrating AI into the DHS mission.
Naval Postgraduate School
-
Excellence in Homeland Security
-
The Center for Homeland Defense and Security offers programs developed in partnership with and are sponsored by the National Preparedness Directorate of FEMA, focused on assisting current and emerging leaders in Homeland Defense and Security to develop the policies, strategies, programs, and organizational elements needed to defeat terrorism and prepare for and respond to natural disasters and public safety threats across the United States.
-
Through CHDS graduate and executive-level coursework, seminars, and research, homeland security leaders gain the analytic and critical thinking skills and substantive expertise they need to create innovative solutions that address the threats facing the nation and local communities.
(See how CHDS resources are utilized daily by hundreds of local, state, territorial, tribal, and federal agencies, the private sector, and academic institutions to accomplish their missions. The Center facilitates leaders in taking their ideas out of the classroom and into the real world where they become new policies and strategies that better protect our communities and country. Courtesy of CHDS and YouTube.)
Federal Protective Service in Collaboration with the Argonne National Laboratory
-
Excellence in Homeland Security
-
FPS uses the Modified Infrastructure Survey Tool (MIST) which was developed in partnership with the Department of Energy’s Argonne National Laboratory.

-
Using MIST, FPS can survey a facility’s current security posture and make countermeasure recommendations.
-
This multi-component application includes a survey tool, artificial intelligence-powered threat determination, a security asset tracking system, and a stakeholders communication tool.
-
The MIST Stakeholder Self-Service Tool (SST), is currently providing more than 300 Federal agencies with the documentation and data necessary to maintain ISC compliance at the national level, through a secure application gateway that allows security managers and agency leadership to view current and prior facility security assessments and countermeasure recommendations while documenting and ensuring their ISC compliance.
DHS/CISA/Infrastructure Security Division/Interagency Security Committee
-
Excellence in Homeland Security
-
The Interagency Security Committee’s (ISC) Risk Management Process and Facility Security Committee Training positively impacts federal facility security through a systemic and deliberate risk management approach, which is a level of protection commensurate with the level of risk.

-
These virtual instructor-led courses cover the ISC Risk Management Process and the roles and responsibilities of the Facility Security Committee, and is offered at no cost to participants and is available on a first-come, first-served basis.
-
The ISC Risk Management Process and Facility Security Committee Training is highly recommended for Facility Security Committee (FSC) Chairs, FSC Members, Executives, Managers, and any personnel involved in making facility funding, leasing, security, or other risk management decisions.
U.S. Fire Administration
-
Excellence in Public Safety
-
The U.S. Fire Administration (USFA) supports the fire and emergency services professional development community through the Fire and Emergency Services Higher Education (FESHE) initiative to standardize training, education, experience, and certification activities.

-
USFA and National Fire Academy (NFA) work to advance the professional status and expand the knowledge and skills of fire and emergency services personnel, with free training and education programs to support fire departments and emergency services organizations in preparing for, preventing, and responding to fires and other hazards.
-
This national, competency-based professional development system helps to eliminate duplication of efforts and enhance the overall professional development of the fire and emergency services.
(Tonya Hoover, Superintendent at United States Fire Administration describes how the USFA supports the training, education, and professional development of fire departments so they are better prepared to respond to all hazards. Learn more about the staff behind their mission. Courtesy of the U.S. Fire Administration, FEMA, and YouTube.)
Washington DC Metropolitan Police Department
-
Excellence in Public Safety
-
One of the 10 largest local police agencies in the United States, the Metropolitan Police Department is the primary law enforcement agency for the District of Columbia.
-
Founded in 1861, the Metropolitan Police Department of today is on the forefront of technological crime fighting advances, from highly developed advances in evidence analysis to state-of the-art-information technology.
-
Each and every member of the Metropolitan Police Department lives their motto: We are here to help, each and every day!

San Diego Harbor Police Foundation
-
Excellence in Public Safety & Community Enrichment
-
For police officers, the concept of devotion to duty is second nature. Every day, the men and women of uniformed law enforcement serve on the front lines, protecting the communities and individuals in their care.

-
True to its heritage, the nonprofit San Diego Harbor Police Foundation represents a deep-rooted commitment to service and has made significant contributions toward improving the lives of children, families, and police officers.
-
Envisioned by Mark Stainbrook, Chief of the Port of San Diego Harbor Police, and led by Chief Executive Officer Jeff Wohler, the San Diego Harbor Police Foundation supports three critical initiatives, each of which make the world a safer place: Community Outreach, Officer Wellness, and Countering Human Trafficking Awareness & Training programs.
(The San Diego Harbor Police Foundation celebrates the holidays by helping others. And there’s no better way than to help fund the Shop with a Cop program. In 2020 COVID-19 got in our officers’ way, but barely. Courtesy of the San Diego Harbor Police Foundation and YouTube.)
Washington DC Police Foundation
-
Excellence in Public Safety & Community Enrichment
-
The Washington DC Police Foundation, a 501 (c) (3) organization in our Nation’s Capital, serves over 15,000 youth annually through mentoring programs led by police officers, designed to enhance communication and build positive relationships between youths, families, and law enforcement.

-
“At a time when the relationships between police and some communities are strained, these programs are designed to build positive relationships, between officers and at-risk youth,” explains Patrick Burke, Executive Director at the Washington DC Police Foundation.
-
The Washington DC Police Foundation expands public safety awareness and advances public safety initiatives helping make the Nation’s Capital a safer place for all to live, work and visit with world-class community engagement and support for the Washington DC Metropolitan Police Department.
(Learn More about the Foundation and how you can help to become part of the solution in our children’s lives. Courtesy of the Washington DC Police Foundation and YouTube.)
PWPORG
-
Excellence in Public Safety & Community Enrichment
-
PWPORG (Preparedness Without Paranoia) is a 501(c)(3) built by law enforcement and security industry practitioners and educators to provide educational resources to kids, families, and communities on safety and emergency preparedness.

-
PWPORG is proactively taking action to introduce the children and families in our communities, to skills and educational resources on safety and emergency preparedness, that when learned and practiced, will last for a lifetime.
-
Guided by Dr. Kathleen Kiernan, a 29-year veteran of Federal Law Enforcement and President of NEC National Security Systems, the nonprofit PWPORG was created to educate, engage and empower families and kids on issues of preparedness and resiliency to create a safer world, free of active threats and human traffickers.
(Learn about how YOU can Make a Difference in the lives of our Nation’s Children and Families. Be a Superhero, Make a Donation and Make a Difference by helping to support Preparedness Without Paranoia and Parents with Preparedness Magazine. Courtesy of Kiernan Group Holdings and YouTube.)
InfraGard National Alliance
-
Excellence in Homeland Security
-
-
InfraGard National Alliance – Protecting America for 25 Years
-
-
-
InfraGard is the largest public-private partnership in the world with 80,000 members, founded by the Federal Bureau of Investigation (FBI), which was recognized in the 2020 ‘ASTORS’ Awards Program, dedicated to the protection of U.S. critical infrastructure.

-
Through seamless collaboration, InfraGard connects owners and operators within critical infrastructure to the FBI, to provide education, information sharing, networking, and workshops on emerging technologies and threats.
-
InfraGard’s vetted membership includes business executives, entrepreneurs, lawyers, security personnel, military, and government officials, IT professionals, academia, and state and local law enforcement—all dedicated to contributing industry-specific insight and advancing national security.
-
The InfraGard National Members Alliance is a nonprofit 501(c)3 organization, is comprised of 77 chapters across the country.
Naval Criminal Investigative Service
-
Excellence in Homeland Security
-
The Naval Criminal Investigative Service (NCIS) Transnational Crime Unit (TCU), is combatting illegal narcotics by deploying special agents aboard multinational Combined Task Force 150 (CTF-150) warships during maritime security operations.
-
This team of highly skilled special agents patrols the high seas aboard ships from the United States, France, New Zealand, Australia, Canada, and the United Kingdom, to provide law enforcement expertise and collect intelligence during interdictions of illicit narcotics aboard suspicious vessels found in areas known for drug trafficking operations.
-
These interdictions deny funding for terrorism, significantly contribute to the National Defense Strategy, and also strengthen military readiness by keeping illicit narcotics from reaching service members and their families throughout Europe, Africa, and the United States.
(Learn about the NCIS mission to investigate and defeat criminal, terrorist, and foreign intelligence threats to the United States Navy and Marine Corps—ashore, afloat, and in cyberspace. Courtesy of NCIS and YouTube.)
Sandia National Laboratories
-
Excellence in Homeland Security
-
This neutron electric-field (E-field) imaging technology developed by Yuan-Yu Jau and funded by Neutron E-Field Imaging, will determine whether a concealed, electric detonator is charged for nuclear reactions in weapons and power plants.

-
E-field imaging technology can solve the problems of determining various electric properties inside a physically isolated space and the electronic charge/voltage state inside a metal box, the kind of metrology that was thought to be impossible.
-
When finished, it will enable the safe examination of sealed metal boxes when opening them could be dangerous, whether it’s because inside is an explosive weapon or a malfunctioning, high-voltage fire set at a missile range.
-
This important breakthrough in imaging technology will provide new diagnostic powers of great value across widespread security applications.
TENEO
-
Excellence in Homeland Security
-
In today’s complex operating environment, organizations are charged with mitigating an array of interdisciplinary and intersecting risks across the enterprise, whether terrorism, reputational risk, geopolitical risk, or cyber threat, and the complexity of this risk landscape demands new mitigation strategies and tactics that transcend traditional security processes.

-
Led by former NYPD, BPD, and LAPD Police Commissioner, and Vice Chairman of the Secretary of Homeland Security’s Advisory Council, Bill Bratton, who was recognized as the ‘2019 ‘ASTORS’ Person of the Year’ for his Lifetime of Dedication and Extraordinary Leadership in Homeland Security and Public Safety, TENEO Risk Advisory is made up of leading security and political risk consultants with backgrounds from the world’s most respected corporate, intelligence, public-safety, public-health and technology organizations.
-
TENEO Risk Advisory offers CEOs a holistic approach to identify, manage, and mitigate operational risks to their businesses by providing comprehensive strategic guidance to build risk awareness, resiliency, and mitigation.
(See an ‘American Security Today Exclusive Interview’ with Commissioner Bill Bratton facilitated by Dr. Kathleen Kiernan, President of NEC National Security Systems at the 2020 “ASTORS’ Awards Presentation Luncheon in New York City on November 17, 2021. Courtesy of My Pristine Images, and Vimeo.)
U.S. Immigration and Customs Enforcement
-
Excellence in Homeland Security
-
HSI is the principal investigative arm of the U.S. Department of Homeland Security, responsible for investigating transnational crime and threats, specifically those criminal organizations that exploit the global infrastructure through which international trade, travel, and finance move, with a mission to investigate, disrupt and dismantle terrorist, transnational and other criminal organizations that threaten or seek to exploit the customs and immigration laws of the United States.

-
HSI has broad, legal authority to conduct federal criminal investigations into the illegal cross-border movement of people, goods, money, technology, and other contraband throughout the United States, and utilizes these authorities to investigate a wide array of transnational crime, including terrorism; national security threats; narcotics smuggling; transnational gang activity; child exploitation; human smuggling and trafficking; illegal exports of controlled technology and weapons; money laundering; financial fraud and scams; worksite and employment crimes; cybercrime; intellectual property theft and trade fraud; identity and benefit fraud; and human rights violations and war crimes.
(See how law enforcement can more effectively collaborate to form a force multiplier of resources and capabilities in the ever-expanding global world of crime. Homeland Security Investigations (HSI) bridges the gap. HSI has the ability to follow the “pipeline” and to proactively pursue the larger networks of illicit activities. HSI can serve as a force multiplier from anywhere domestic; from Minot, ND to New York City – to almost anywhere around the world with our international partners, either through the Transnational Criminal Investigative Units (TCIU’s) – which expand HSI’s footprint and enhance cooperation between partner nations and the United States – or through our 63 HSI International Attaché offices. State and Local law enforcement have the ability to leverage HSI’s unique legal authorities and global footprint to help combat crimes in their community; such as the growth and proliferation of transnational crimes and the rampant and far-reaching cyber crimes – most notably, the darknet. Courtesy of WebsEdgeSociety and YouTube.)
-
In collaboration with its strategic partners in the U.S. and abroad, HSI special agents gather evidence to identify and build criminal cases against Transnational Criminal Organizations (TCOs), terrorist networks and facilitators, and other criminal elements that threaten the United States, and their efforts protect U.S. national, border, and economic security, and ensure the safety of the public and our communities.
-
*ICE Enforcement and Removal Operations (ERO), was also recognized in the 2020 ‘ASTORS’ Homeland Security Awards Program, and the Human Rights Violators and War Crimes Unit (HRVWCU) was recognized in the 2018 ‘ASTORS’ Awards Program.
U.S. Customs and Border Protection
-
Excellence in Homeland Security
-
The Office of Field Operations (OFO) is a federal law enforcement agency within the U.S. Customs and Border Protection (CBP) responsible for managing United States customs operations at 20 Field Operations offices, 328 ports of entry, and 16 pre-clearance stations in Canada, Ireland, the UAE, and the Caribbean.

-
Headed by a CBP Assistant Executive Commissioner, OFO directs the activities of more than 27,000 employees, including more than 22,000 CBP Officers and Agriculture Specialists.
-
CBP Office of Field Operations is the largest component in CBP, has the largest working Law Enforcement Canine Program in the world, in addition to the Office of Air and Marine (AMO), and the U.S. Border Patrol, which was recognized in the 2019 ‘ASTORS’ Awards Program.
-
The vast majority of CBP’s resources are located along the Southwest border, from Brownsville, Texas to San Diego, California, and CBP canine teams are also strategically assigned to other ports of entry around the country, and located at pre-clearance stations abroad.
(Hear from U.S. Customs and Border Protection Office of Field Operations Executive Assistant Commissioner William A. Ferrara, on his U.S. Trade experience with a focus on the unprecedented times of the COVID-19 global pandemic.
-
The CBP was also recognized in the 2018, and 2017 ‘ASTORS’ Homeland Security Awards Programs, respectively.
NEC Corporation of America
-
-
Excellence in Innovation for Airport/Aviation Safety
-
-
NEC Thermal Express combines NEC’s world-class artificial intelligence (AI)-driven advanced video and thermal analytics, and industry-leading face recognition technologies with trusted infrared (IR) thermal imaging sensors to deliver a solution that simultaneously verifies identities and detects body temperatures without contact.
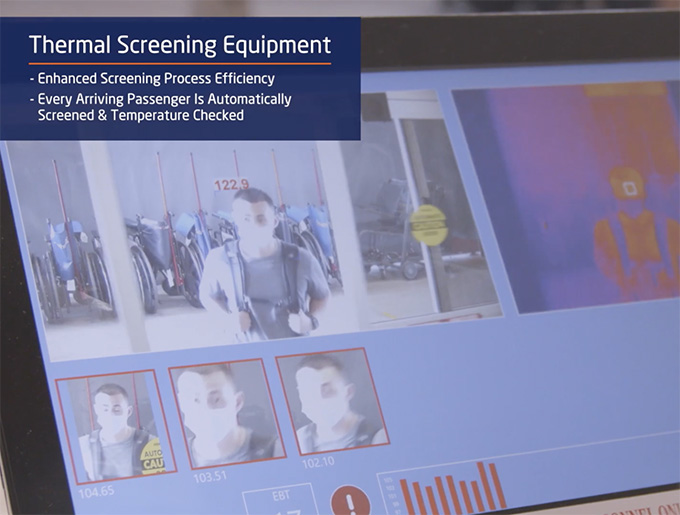
-
This innovative NeoFace Thermal Express technology was successfully deployed by the State of Hawaii at all five Hawaiian airports in response to the COVID-19 global pandemic, to automatically screen the body temperature of every arriving passenger entering the airport terminal, to ensure they would not become hotspots of virus contraction as people cross paths from across the globe.
-
As a global technology leader for 120 years, NEC has proven its ability to anticipate and meet market needs, to demonstrate technical excellence, and to build a dependable and enduring business model based on NEC’s primary mission, to help orchestrate a brighter world.
(The Hawaii Department of Transportation (DoT) partners with NEC to install a hygienic, contactless, thermal body temperature screening solution at Hawaii’s 5 major airports. The purpose of this project is to protect the health and safety of the traveling community, the visitors, and the residents and to prevent the spread of COVID-19. Courtesy of NEC Corporation of America and YouTube.)
NEC Corporation of America
-
-
Excellence in Innovation for Airport/Aviation Safety
-
-
The NEC I:Delight digital identity management platform provides a unified experience for a variety of aviation services using a unique Digital ID to transform the passenger curb-to-gate journey.
-
NEC I:Delight enables a hygienic and seamless travel experience that benefits everyone, from travelers to airport staff by giving travelers a single Digital ID that they can use within the airport and beyond.”
(The world’s largest global airline alliance, Star Alliance, launched its new #biometrics service, Star Alliance Biometrics in November 2020. Watch this video to see how Star Alliance members can enjoy and experience various airport touchpoints using a single #DigitalID. Touchpoints include check-in, baggage drop, VIP lounge, duty-free shopping, and many more. Powered by NEC I:Delight, this technology is now available at Frankfurt and Munich airports, for Lufthansa flights. Courtesy of NEC Corporation of America and YouTube.)
Gordon (Scott) Armstrong
-
Excellence in National Security for Traveler Security Mgmt
-
-
-
Aviation Program Branch
Law Enforcement/Federal Air Marshal Service (FAMS)
-
-
-
-
In recognition of the outstanding training and support the ‘Crew Member Self Defense Training Program‘ provided our industry partners.
-
Through this training, TSA enhanced the safety and security of the traveling public and the flight crew members who serve them.
(Run. Hide. Fight. Everyone is familiar with how to deal with certain threats on the ground. But the rules are different at 35,000 feet. Take an inside look at how the TSA’s Federal Air Marshals Service is teaching airline crew members how to defend themselves – and the aircraft – from terrorists. Courtesy of the TSA and YouTube.)
Transportation Security Administration (TSA)
-
Excellence in National Security for Traveler Security Mgmt
-
-
-
TSA Team Newark at
Newark Liberty International Airport
-
-
-
-
In recognition and with sincere appreciation of your exceptional contributions at Newark International Airport, in promoting the transportation security mission and outstanding dedication to the agency, stakeholders, and the traveling public.
(On this the 20th Anniversary of the TSA, please join us in celebrating the fabulous work of this comprehensive and innovative agency in securing public transportation across our Nation, and keeping our citizens safe, one plane, train, bus, highway, and mass transit hub at a time. See selected highlights from the TSA’s 20th Anniversary event held at Ronald Reagan Airport on November 19, 2021. Courtesy of the TSA and YouTube.)
Introducing the 2021 ‘ASTORS’ Extraordinary Leadership & Innovation Award Recipients
AMAROK
2021 ‘ASTORS’ Extraordinary Leadership & Innovation Award

-
AMAROK provides Security Solutions for industrial and commercial properties throughout the United States and Canada.
-
When touched, the company’s 10-foot-high, solar-powered Electric Guard Dog fence shocks would-be thieves with 7,000 medically safe volts. Any attempt to cut or scale the fence triggers alarms and bright LED lights.
-
After over 40 years, the leadership of Electric Guard Dog decided it was time to give the brand a fiercer and more modern name, and Electric Guard Dog was transformed into AMAROK, named after the wolf-like creature of legend that was said to guard villages from intruders, to reflect their commitment to relentlessly protect their customers.
-
Today, AMAROK specializes in providing Multiple Layers of Security to stop criminals before they get in with the world‘s first integration of electric security fencing, video surveillance, and video monitoring to create the ultimate crime prevention solution for your commercial business or industrial site.
(See an ‘American Security Today Exclusive Interview’ with Michael Dorrington, Senior VP of Sales and Marketing at AMAROK, a full-perimeter security company based in Columbia, South Carolina, that provides service throughout the United States and Canada. Specializing in electric fencing on commercial properties, AMAROK also provides supplemental surveillance solutions, including cameras, lights, and alarms. Together, they form the ultimate crime prevention solution for any business. Courtesy of AMAROK and YouTube.)
Acoustic Technology Inc. (ATI Systems)
2021 ‘ASTORS’ Extraordinary Leadership & Innovation Award

-
ATI Systems continues to demonstrate an unfaltering commitment to the design, manufacture, integration, and installation of the industry most innovative, reliable, cost-effective, and compact emergency warning and natural and man-made disaster notification systems to colleges and universities, communities, ports, refineries, power plants, military bases all over the world.
-
Incorporated in Massachusetts in 1981 as an acoustic consulting firm, ATI Systems developed a cutting-edge wireless system that provided audible and visual warnings via a reliable, compact hardware design, user-friendly software, and redundant communication methods, including radiofrequency, Ethernet, and satellite technology.
-
Implementing advanced encryption and the latest security features ATI enables users to initiate advanced Emergency Alert Systems (EAS) coverage, that ensures ease of communication in the most critical moments.
(See an ‘American Security Today Exclusive Interview’ with Robert McLaughlin, Sales Manager at Acoustic Technologies, Inc. (ATI Systems), a world-leading provider of reliable emergency warning & mass notification systems (MNS), that provide audible and visual warnings via reliable, compact hardware. Courtesy of My Pristine Images and Vimeo.)
Attivo Networks
2021 ‘ASTORS’ Extraordinary Leadership & Innovation Award

-
Attivo Networks continues to build upon the field of advancing deception technology and developing advanced network security threat detection technologies for deployment both on-premise or as a cloud service, to the company’s ThreatDefend™ Deception & Response Platform.
-
Additionally, Attivo now also includes Active Directory Protections, and has expanded upon their Identity Detection & Response (IDR) Portfolio with their new IDR Suite of Products, which includes Attivo’s new Cloud Infrastructure Entitlement Management (CIEM) solution, IDEntitleX, that delivers unprecedented visibility to identity risks across Endpoint, Active Directory Environments and Cloud Infrastructures.
(Attacking Active Directory and obtaining domain admin-level access is one of the attackers’ primary objectives. Active Directory and Domain controllers are prime reconnaissance targets to hunt for privileged credentials and privileged access. Attivo Networks provides innovative solutions for assessing Active Directory cyber hygiene, identifying specific domain, computer, and user-level risks, and detecting live attacks. Courtesy of Attiov Networks and YouTube.)
Automatic Systems America
2021 ‘ASTORS’ Extraordinary Leadership & Innovation Award

-
For over 50 years Automatic Systems has enabled innovative secure access management, for the fluidity of movement, security of people, and infrastructure through the design and manufacture of automated pedestrian, vehicle, and passenger access systems.
-
Automatic Systems America continues to evolve its award-winning SlimLane swing optical barrier turnstiles to offer customized solutions able to meet customer requirements for even the most unique installations with a variety of speedgate cabinets range from the sleek standard unit and evolve to the SlimLane EP model or the rounder SlimLane EPR.

-
Larger biometric peripherals such as facial recognition and frictionless fingerprinting offer a contactless alternative to proximity readers and can easily be integrated within the SlimLane EPW or NK cabinets.
-
With the current social distancing and contactless requirements, the SlimLane can also offer a fully touchless solution while protecting its users.
-
The hand “wave” and facial recognition readers were easily integrated and offer a fully contactless solution while the UL 2593 Certified SlimLane offers a highly reliable (10 Million MCBF) physical access control turnstile, and with its 5-year standard warranty and infinite customizations, the SlimLane continues to be a perfect solution for lobby entrances.
-
Selected as the “standard” for multiple financial institutions, we are confident that the SlimLane will continue to answer any pedestrian access control requirements for your years to come.
(Automatic Systems’ Slimlane EPW speed gates offer extended integration capabilities, allowing us to offer contactless identification solutions, with best-in-class #biometric readers such as the MorphoWave Compact device from IDEMIA. Courtesy of Automatic Systems and YouTube.)
Fortior Solutions
2021 ‘ASTORS’ Extraordinary Leadership & Innovation Award

-
Fortior Solutions is a leader in world-class identity and access control solutions that specialize in National Crime Information Center Interstate Identification Index (NCIC III) checks and third-party commercial background screenings.
-
The company which is headquartered in Hillsboro, Oregon, is a nationally recognized leader in high-assurance identity management solutions, that helps organizations reduce risk by quickly identifying who they can trust.
-
Fortior Solutions through their RAPIDGate® and RAPID-RCx® programs, provide unparalleled perimeter control at some of the most security-conscious organizations in the world including, the U.S. Army, U.S. Coast Guard, U.S. Navy, U.S. Marine Corps, and NASA among others, and is largest commercial provider of recognized vendor credentials to the U.S. Department of Defense.
-
The RAPIDGate program is a complete vendor management solution that includes verification of company sponsorship, company enrollment, multi-language kiosk-based registration, individual biographic and biometric collection, equipment, commercial background screenings, DOJ/FBI NCIC/III checks (subject to approval of the relevant government authorities).
SIMS Software
2021 ‘ASTORS’ Extraordinary Leadership & Innovation Award

-
SIMS Software is the leading provider of industrial security information management software to the government and defense industries.
-
The company’s flagship product Security Information Management System (SIMS), has protected classified and high-value information for security stakeholders since 1983, and has been assessed and certified as meeting the requirements of ISO 9001:2015 for providing development, support, and training for software used in auditing critical assets of the US government, defense contractors, and emergency responders.
-
SIMS Dashboards is the newest and most powerful tool to maximize your investment in SIMS, providing real-time visibility, analysis, and reporting of your security domain – 24 hours a day, 7 days a week.
(See an ‘American Security Today Exclusive Interview’ with Michael Struttmann, CEO & President of SIMS Software, the leading provider of industrial security information management software to the government and defense industries. Courtesy of My Pristine Images and Vimeo.)
Dr. Kathleen Kiernan
2021 ‘ASTORS’ Extraordinary Industry Leadership & Innovation Person of the Year

-
Dr. Kathleen Kiernan is the Founder and CEO of national security, education, risk management, and training firm Kiernan Group Holdings (KGH), Chair Emeritus of InfraGard National Members Alliance, and adjunct faculty member at the Naval Postgraduate School.
-
KGH serves customers across the US Government trade space, law enforcement, security, the risk management community.
-
With a special focus on the ultimate soft-target, our Nation’s schools, Kiernan believes preparedness is a mindset that can be learned and when practiced, prevents ordinary days from turning into extraordinary ones due to an active threat in any form, including those posed by insiders.
(Hear directly about the ‘Preparedness Without Paranoia’ Education and Training Series from Dr. Kathleen Kiernan, CEO & Founder of Kiernan Group Holdings. Courtsy of KGH and YouTube.)
-
A 29-year veteran of Federal Law Enforcement, Dr. Kiernan retired as Assistant Director for the Office of Strategic Intelligence and Information for ATF, serves as a subject matter expert for the defense, intelligence, and law enforcement communities, and works with organizations making a difference in the world including the Business Executives for National Security (BENS) Resilience Council, the AFCEA Intelligence Committee, and the Center for Advanced Red Teaming (CART), University of Albany, SUNY.

-
Dr. Kiernan believes experience brings an obligation to foster professional development in others through mentoring and education which she does both inside and outside of formal classrooms.
-
She developed an approach to citizen engagement and education to increase confidence and decrease victimization in active threat environments.
-
Her dedication to public service includes her support to Veteran organizations and her 18-year participation in the Susan G. Komen 3-Day walk to raise awareness and funding for breast cancer research.
TSA Administrator David Pekoske
2021 ‘ASTORS’ Extraordinary Government Leadership & Innovation Person of the Year

TSA Administrator David Pekoske being presented his 2021 ‘ASTORS’ Extraordinary Government Leadership & Innovation Person of the Year Award, by Dr. Kathleen Kiernan, President of NEC National Security Systems, and Tammy Waitt, Editorial Director of AST.
-
TSA Administrator David Pekoske was confirmed by the U.S. Senate as the Transportation Security Administration’s seventh administrator in August 2017.
-
He leads a workforce of approximately 60,000 employees, including the Federal Air Marshal Service, and is responsible for security operations at nearly 450 airports throughout the United States and shared security for highways, railroads, ports, mass transit systems, and pipelines.

-
Under the Administrator’s leadership, TSA is working continuously to raise the security baseline for both aviation and surface transportation through close partnerships and alliances and a robust homeland security network.
-
While continuing to serve as TSA Administrator, Pekoske also served at the Department of Homeland Security as Acting Secretary from January 20 to February 2, 2021, and as the Senior Official Performing the Duties of Deputy Secretary from April to November 2019 and again from February to June 2021.
-
At the Department, Administrator Pekoske helped lead a unified national effort to ensure the continued security of the United States, coordinating components with missions ranging from prevention and protection to recovery and response.
(Hear more from Administrator Pekoske on his priorities for 2022, staying ahead of threats, supporting frontline employees, and protecting the traveling public. Courtesy of the TSA and YouTube.)
-
Before joining TSA, Administrator Pekoske was an executive in the government services industry where he led teams that provided counterterrorism, security, and intelligence support services to government agencies.
-
Most notably, Administrator Pekoske served as the 26th Vice Commandant of the U.S. Coast Guard, culminating a Coast Guard career that included extensive operational and command experience.

-
As the Vice Commandant, Pekoske was second in command, also serving as Chief Operating Officer and Component Acquisition Executive of the Coast Guard. He is a recognized expert in crisis management, strategic planning, innovation, and port and maritime security.
-
Administrator Pekoske holds a Master of Public Administration degree from Columbia University and a Master of Business Administration degree from the Massachusetts Institute of Technology. He earned his Bachelor of Science degree in ocean engineering from the U.S. Coast Guard Academy.
-
His awards include the Homeland Security Distinguished Service Medal, Coast Guard Distinguished Service Medal, the Meritorious Service Medal, Coast Guard Commendation and Achievement Medals.
American Security Today would like to Congratulate each and every one of our Outstanding 2021 ‘ASTORS’ Homeland Security Awards Winners!
Why American Security Today?
The traditional security marketplace has long been covered by a host of publications putting forward the old school basics to what is Today – a fast-changing security landscape.
American Security Today is uniquely focused on the broader Homeland Security & Public Safety marketplace with over 75,000 readers at the Federal, State, and Local levels of government as well as firms allied to the government.
American Security Today brings forward a fresh compelling look and read with our customized digital publications that hold readers’ eyes throughout the story with cutting-edge editorial that provides solutions to their challenges.
Harness the Power of the Web – with our 100% Mobile Friendly Publications

The AST Digital Publications is distributed to over 75,000 qualified government and homeland security professionals in Federal, State, and Local levels.
‘PROTECTING OUR NATION, ONE CITY AT A TIME’
AST Reaches both Private & Public Experts, essential to meeting these new challenges.
Today’s new generation of public safety and security experts need real-time knowledge to deal with domestic and international terrorism, lone wolf attacks, unprecedented urban violence, shifts in society, culture, and media bias – making it increasingly difficult for Homeland Security, Law Enforcement, First Responders, Military and Private Security Professionals to implement coordinated security measures to ensure national security and improve public safety.
These experts are from Government at the federal, state, and local level as well as from private firms allied to the government.
AST provides a full plate of topics in our AST Monthly Magazine Editions, AST Website, and AST Daily News Alerts, covering 23 Vital Sectors such as Access Control, Perimeter Protection, Video Surveillance/Analytics, Airport Security, Border Security, CBRNE Detection, Border Security, Ports, Cybersecurity, Networking Security, Encryption, Law Enforcement, First Responders, Campus Security, Security Services, Corporate Facilities, and Emergency Response among others.
AST has Expanded readership into integral Critical Infrastructure audiences such as Protection of Nuclear Facilities, Water Plants & Dams, Bridges & Tunnels, and other potential targets of terrorism.
Other areas of concern include Transportation Hubs, Public Assemblies, Government Facilities, Sporting & Concert Stadiums, our Nation’s Schools & Universities, and Commercial Business Destinations – all enticing targets due to the large number of persons and resources clustered together.
To learn more about ‘ASTORS’ Homeland Security Award Winners solutions, be on the lookout for the 2021 ‘ASTORS’ CHAMPIONS Edition Fully Interactive Magazine – the Best Products of 2020 ‘A Year in Review’.
The Annual CHAMPIONS edition includes a review of Annual ‘ASTORS’ Award Winning products and programs, highlighting key details on many of the winning firm’s products and services, including video interviews and more.
 It will serve as your Go-To Source throughout the year for ‘The Best of 2021 Products and Services‘ endorsed by American Security Today, and can satisfy your agency’s and/or organization’s most pressing Homeland Security and Public Safety needs.
It will serve as your Go-To Source throughout the year for ‘The Best of 2021 Products and Services‘ endorsed by American Security Today, and can satisfy your agency’s and/or organization’s most pressing Homeland Security and Public Safety needs.
From Physical Security (Access Control, Critical Infrastructure, Perimeter Protection, and Video Surveillance Cameras and Video Management Systems), to IT Security (Cybersecurity, Encryption, Data Storage, Anti-Malware and Networking Security – Just to name a few), the 2021 ‘ASTORS’ CHAMPIONS EDITION will have what you need to Detect, Delay, Respond to, and Mitigate today’s real-time threats in our constantly evolving security landscape.
It will also include featured guest editorial pieces from some of the security industry’s most respected leaders, and recognized firms in the 2021 ‘ASTORS’ Awards Program.
For more information on All Things American Security Today, as well as the 2021 ‘ASTORS’ Awards Program, please contact Michael Madsen, AST Publisher at mmadsen@americansecuritytoday.com.
AST strives to meet a 3 STAR trustworthiness rating, based on the following criteria:
- Provides named sources
- Reported by more than one notable outlet
- Includes supporting video, direct statements, or photos